https://blog.docker.com/2016/08/software-security-docker-containers/
-- via my feedly newsfeed
The Docker security philosophy is Secure by Default. Meaning security should be inherent in the platform for all applications and not a separate solution that needs to be deployed, configured and integrated.
Today, Docker Engine supports all of the isolation features available in the Linux kernel. Not only that, but we've supported a simple user experience by implementing default configurations that provide greater protection for applications running within the Docker Engine, making strong security default for all containerized applications while still leaving the controls with the admin to change configurations and policies as needed.
But don't take our word for it. Two independent groups have evaluated Docker Engine for you and recently released statements about the inherent security value of Docker.
Gartner analyst Joerg Fritsch recently published a new paper titled How to Secure Docker Containers in Operation on this blog post. In it Fritsch states the following:
"Gartner asserts that applications deployed in containers are more secure than applications deployed on the bare OS" because even if a container is cracked "they greatly limit the damage of a successful compromise because applications and users are isolated on a per-container basis so that they cannot compromise other containers or the host OS".
Additionally, NCC Group contrasted the security features and defaults of container platforms and published the findings in the paper "Understanding and Hardening Linux Containers." Included is an examination of attack surfaces, threats, related hardening features, a contrast of different defaults and recommendations across different container platforms. A key takeaway from this examination is the recommendation that applications are more secure by running in some form of Linux container than without.
"Containers offer many overall advantages. From a security perspective, they create a method to reduce attack surfaces and isolate applications to only the required components, interfaces, libraries and network connections."
"In this modern age, I believe that there is little excuse for not running a Linux application in some form of a Linux container, MAC or lightweight sandbox."
– Aaron Grattafiori, NCC Group
The chart below depicts the outcome of the security evaluation of three container platforms. Docker Engine was found to have a more comprehensive feature set with strong defaults.
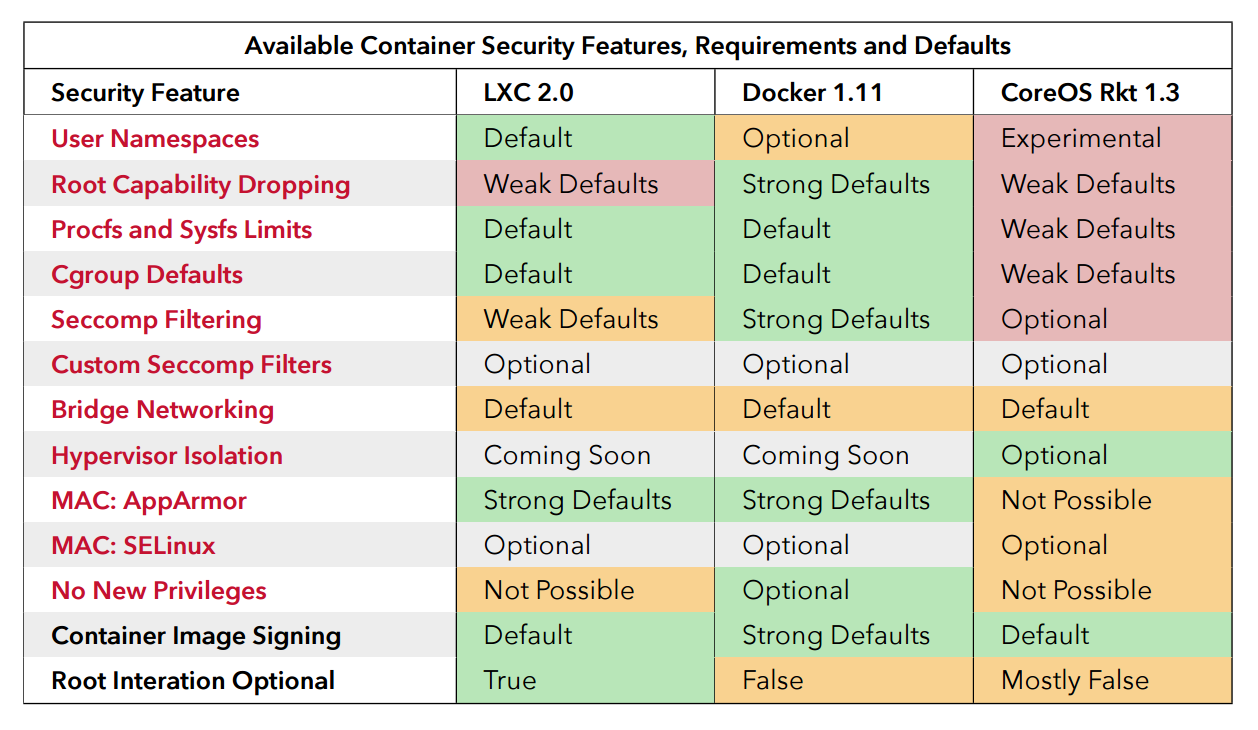
Source: Understanding and Hardening Linux Containers
The Docker security philosophy of "Secure by Default" spans across the concepts of secure platform, secure content and secure access to deliver a modern software supply chain for the enterprise that is fundamentally secure. Built on a secure foundation with support for every Linux isolation feature, Docker Datacenter delivers additional features like application scanning, signing, role based access control (RBAC) and secure cluster configurations for complete lifecycle security. Leading enterprises like ADP trust Docker Datacenter to help harden the containers that process paychecks, manage benefits and store the most sensitive data for millions of employees across thousands of employers.
Your apps are safer and more secure in #Docker containers #security
Click To Tweet
More Resources:
- Read the Container Isolation White Paper
- Learn how Docker secures your software supply chain
- ADP hardens enterprise containers with Docker Datacenter
- Try Docker Datacenter free for 30 days
The post Your Software is Safer in Docker Containers appeared first on Docker Blog.
No comments:
Post a Comment