----
Foreshadow vulnerability on XenServer and XCP-ng
// Xen Orchestra

This is a recap on the latest Foreshadow vulnerability and how it affects XenServer and XCP-ng.
Foreshadow, XSA-273
Yet another Intel x86 security issue… Basically, someone could steal data in RAM, outside the VM boundaries (ie: from other VMs on the same host). If you have non-trusted users in your VMs, it's time to patch ASAP. And maybe disable hyper-threading.
You can find more details here and here.
Should I disable hyper-threading?
No obvious answer sadly:
If an HVM guest kernel is untrusted (i.e. not under host admin control), it is probably not safe to be scheduled with hyper-threading active.
But if you have control on your VMs, please be sure you have all recent fixes available from your OS vendor. Then, no "need" to disable HT.
XAPI security issue, XSA-271
Let's quote the XSA document:
An unauthenticated user with access to the management network can read arbitrary files from the dom0 filesystem. This includes the pool secret
/etc/xensource/ptokenwhich grants the attacker full administrator access.
This is… big. Update ASAP (see below on how) or close your XAPI from outside, now! If you have hosts all around the world, another possibility is to let your XAPI only reachable from a secured tunnel, without external access.
On XenServer
There are multiple patches, depending on your current XenServer version. Citrix did a recap on those vulnerabilities here: https://support.citrix.com/article/CTX236548
Patched versions are:
- 7.0
- 7.1 CU1
- 7.4
- 7.5
You can patch directly from Xen Orchestra UI as soon Citrix publishes them in their official online XML (few days in general).
XenServer 7.2/7.3
If you are using XenServer 7.2 (and 7.3) you have 2 options:
- upgrade ASAP to XenServer 7.5 (WARNING FOR XENSERVER FREE USERS: you'll lose some features previously free!)
- upgrade to XCP-ng 7.5 (you won't lose any feature, 100% free, easy upgrade path)
If you already have a paid contract with Citrix, 7.2 and 7.3 aren't supported anymore, please upgrade to XenServer 7.5!
On XCP-ng
You can read this official XCP-ng blog post regarding both XSAs. As usual and as documented, 2 possibilities:
- CLI:
yum updateon each host - Web UI in Xen Orchestra (see screenshots below)
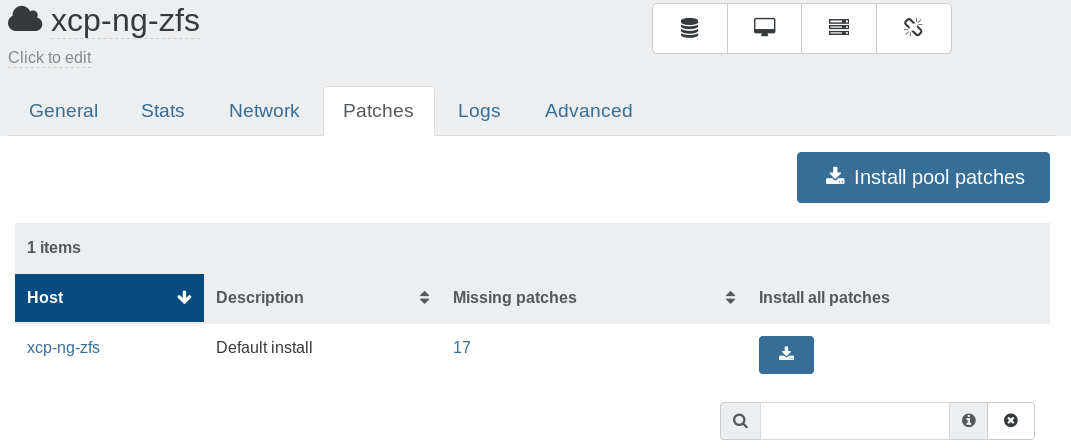
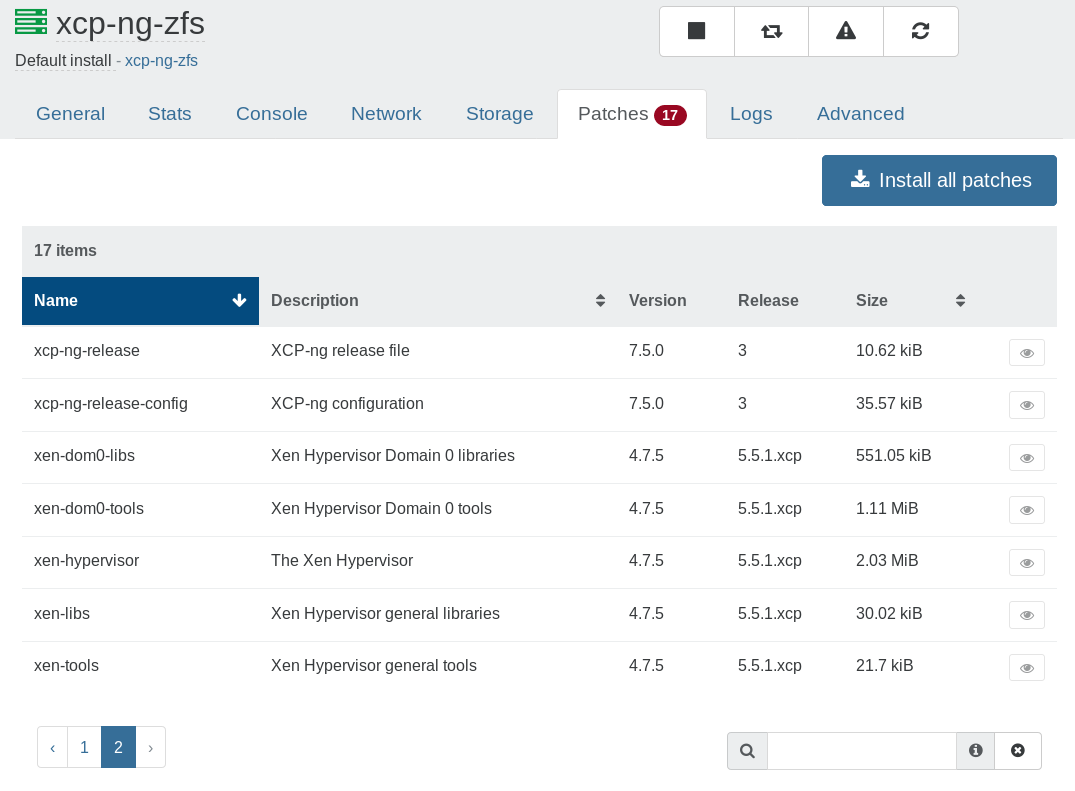
Please reboot your hosts then, and always reboot the pool master first.
Note: a toolstack restart is enough to fix
XSA-271, but reboot is needed forXSA-273

----
Read in my feedly

No comments:
Post a Comment