Today, Talos is publishing a glimpse into the most prevalent threats we've observed between April 21 and April 28. As with previous roundups, this post isn't meant to be an in-depth analysis. Instead, this post will summarize the threats we've observed by highlighting key behavioral characteristics, indicators of compromise, and discussing how our customers are automatically protected from these threats.
As a reminder, the information provided for the following threats in this post is non-exhaustive and current as of the date of publication. Additionally, please keep in mind that IOC searching is only one part of threat hunting. Spotting a single IOC does not necessarily indicate maliciousness. Detection and coverage for the following threats is subject to updates, pending additional threat or vulnerability analysis. For the most current information, please refer to your Firepower Management Center, Snort.org , or ClamAV.net .
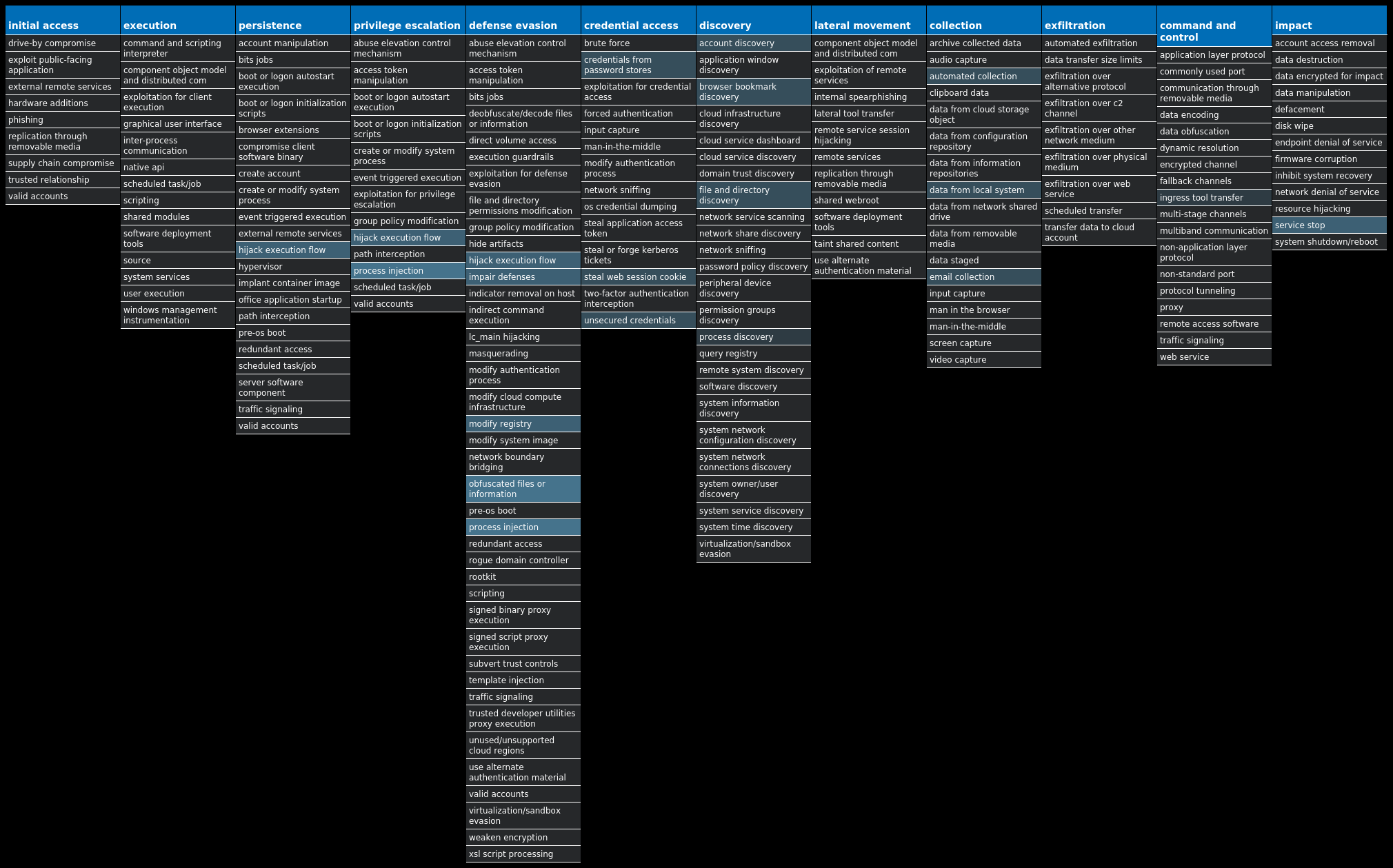
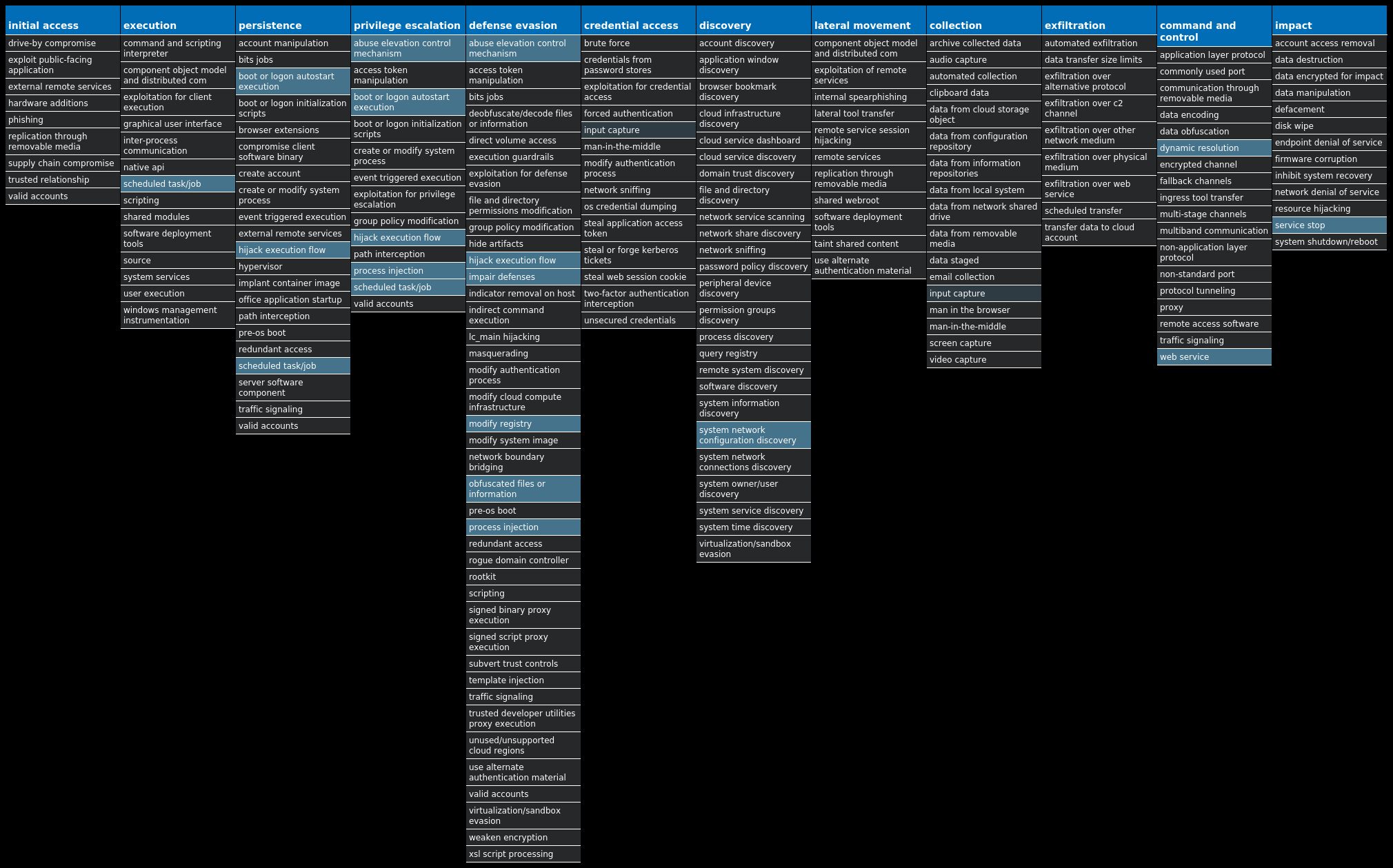
For each threat described below, this blog post only lists 25 of the associated file hashes and up to 25 IOCs for each category. An accompanying JSON file can be found here that includes the complete list of file hashes, as well as all other IOCs from this post. A visual depiction of the MITRE ATT&CK techniques associated with each threat is also shown. In these images, the brightness of the technique indicates how prevalent it is across all threat files where dynamic analysis was conducted. There are five distinct shades that are used, with the darkest indicating that no files exhibited technique behavior and the brightest indicating that technique behavior was observed from 75 percent or more of the files.
The most prevalent threats highlighted in this roundup are:
Threat Name
Type
Description
Win.Dropper.Bifrost-9998862-0
Dropper
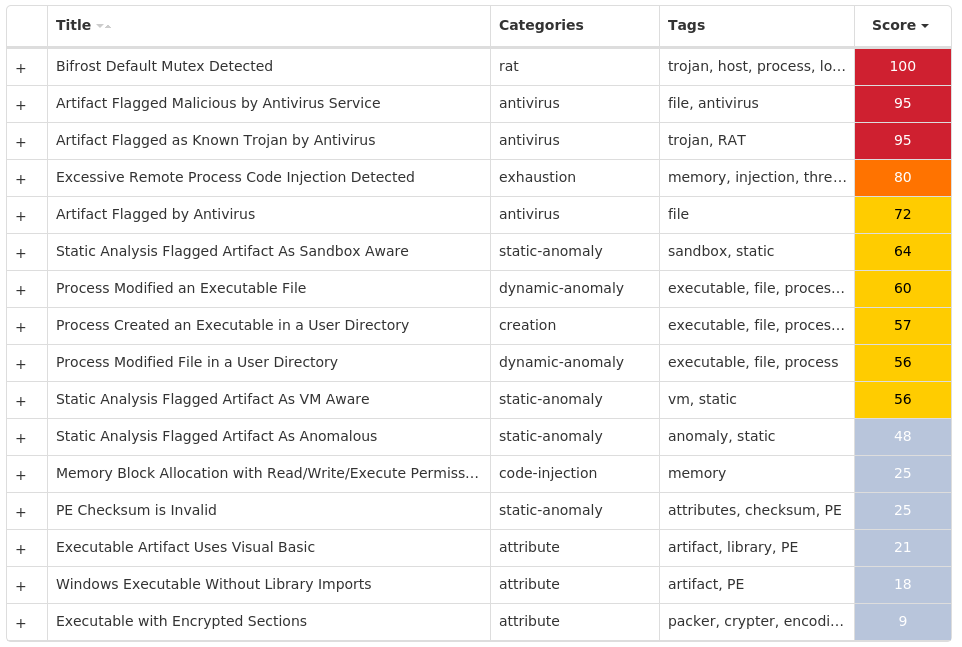
Bifrost is a backdoor with more than 10 variants. Bifrost uses the typical server, server builder, and client backdoor program configuration to allow a remote attacker, who uses the client, to execute arbitrary code on the compromised machine. Bifrost contains standard RAT features including a file manager, screen capture utility, keylogging, video recording, microphone and camera monitoring, and a process manager. In order to mark its presence in the system, Bifrost uses a mutex that may be named "Bif1234," or "Tr0gBot."
Win.Dropper.Tofsee-9997698-0
Dropper
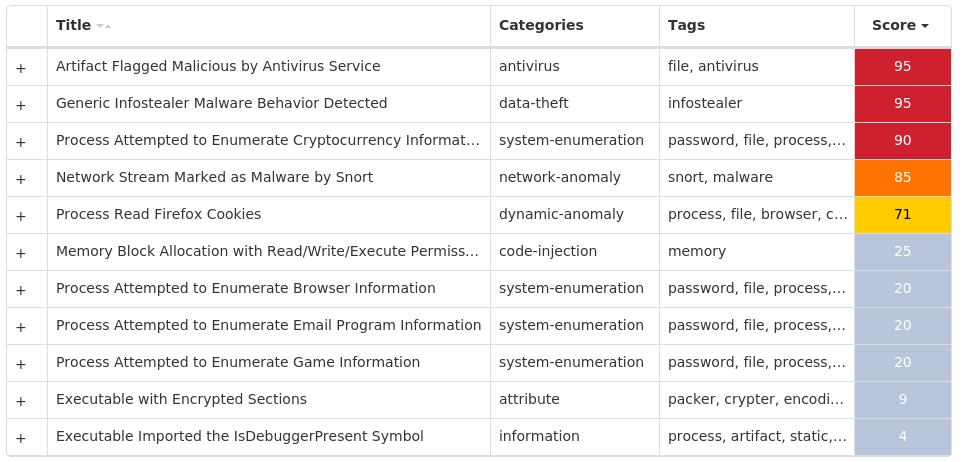
Tofsee is multi-purpose malware that features a number of modules used to carry out various activities such as sending spam messages, conducting click fraud, mining cryptocurrency, and more. Infected systems become part of the Tofsee spam botnet and are used to send large volumes of spam messages in an effort to infect additional systems and increase the overall size of the botnet under the operator's control.
Win.Virus.Ramnit-9997699-0
Virus
Ramnit is a banking trojan that monitors web browser activity on an infected machine and collects login information from financial websites. It also has the ability to steal browser cookies and attempts to hide from popular antivirus software.
Win.Dropper.Remcos-9998831-1
Dropper
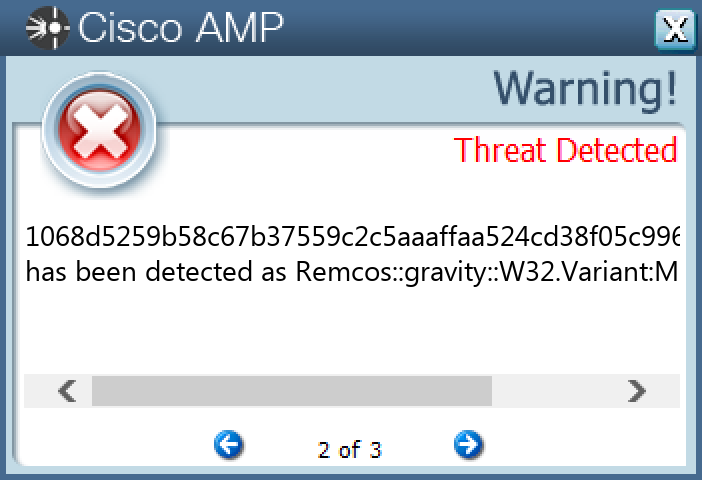
Remcos is a remote access trojan (RAT) that allows attackers to execute commands on the infected host, log keystrokes, interact with a webcam, and capture screenshots. This malware is commonly delivered through Microsoft Office documents with macros, sent as attachments on malicious emails.
Win.Dropper.DarkComet-9998118-1
Dropper
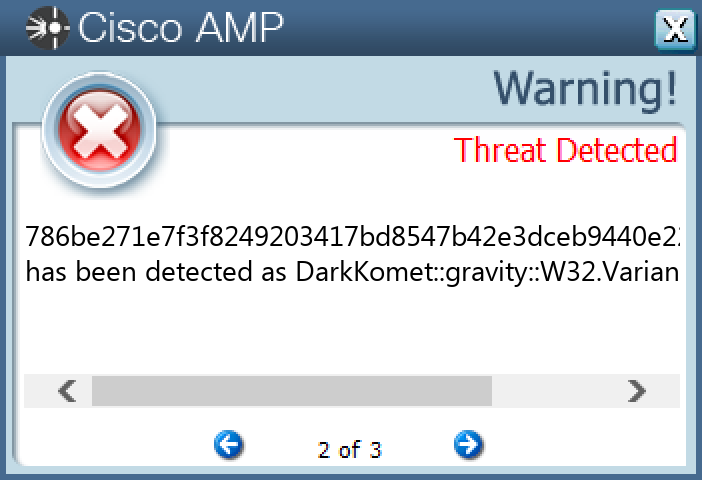
DarkComet and related variants are a family of remote access trojans designed to provide an attacker with control over an infected system. Capabilities of this malware include the ability to download files from a user's machine, mechanisms for persistence and hiding, and the ability to send back usernames and passwords from the infected system.
Win.Virus.Xpiro-9998650-1
Virus
Expiro is a known file infector and information-stealer that hinders analysis with anti-debugging and anti-analysis tricks.
Win.Dropper.LokiBot-9997784-0
Dropper
Lokibot is an information-stealing malware designed to siphon off sensitive information stored on an infected device. It is modular in nature, supporting the ability to steal sensitive information from a number of popular applications. It is commonly pushed via malicious documents delivered via spam emails.
Win.Downloader.Upatre-9998551-0
Downloader
Upatre is a malicious downloader often used by exploit kits and phishing campaigns. Upatre downloads and executes malicious executables, such as banking malware.
Win.Ransomware.Cerber-9998102-0
Ransomware
Cerber is ransomware that encrypts documents, photos, databases and other important files. Historically, this malware would replace files with encrypted versions and add the file extension ".cerber," although in more recent campaigns other file extensions are used.
Threat Breakdown
Win.Dropper.Bifrost-9998862-0
Indicators of Compromise
IOCs collected from dynamic analysis of 36 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\FORUM SERVER6
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{OY2O4VXC-P514-O36S-5W0B-V135334Y4PE5}6
<HKLM>\SOFTWARE\WOW6432NODE\FORUM SERVER6
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\ACTIVE SETUP\INSTALLED COMPONENTS\{OY2O4VXC-P514-O36S-5W0B-V135334Y4PE5} Value Name: StubPath 6
<HKCU>\SOFTWARE\FORUM SERVER Value Name: FirstExecution 6
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: tbtrb 6
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: bbbt 6
<HKCU>\SOFTWARE\FORUM SERVER Value Name: FileNameAtual 6
<HKCU>\SOFTWARE\FORUM SERVER Value Name: ByPersist 6
<HKCU>\SOFTWARE\FORUM SERVER Value Name: FileName 6
<HKLM>\SOFTWARE\WOW6432NODE\FORUM SERVER Value Name: HKLM 6
<HKCU>\SOFTWARE\FORUM SERVER Value Name: HKCU 6
Mutexes
Occurrences
Spy-Net6
Spy-Net_Sair6
Bif12344
stb1
Global\71b0ff21-e3cc-11ed-9660-001517619ccc1
Global\a08a09e1-e3cc-11ed-9660-0015178afdb91
Global\6bc18981-e3cd-11ed-9660-0015170e0b8c1
Global\1dc44421-e3cd-11ed-9660-0015177d9b691
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
mola1986[.]no-ip[.]org6
Files and or directories created
Occurrences
%TEMP%\Decrypted.exe13
%SystemRoot%\SysWOW64\btbrtb6
%SystemRoot%\SysWOW64\btbrtb\btrbbtr.exe6
File Hashes
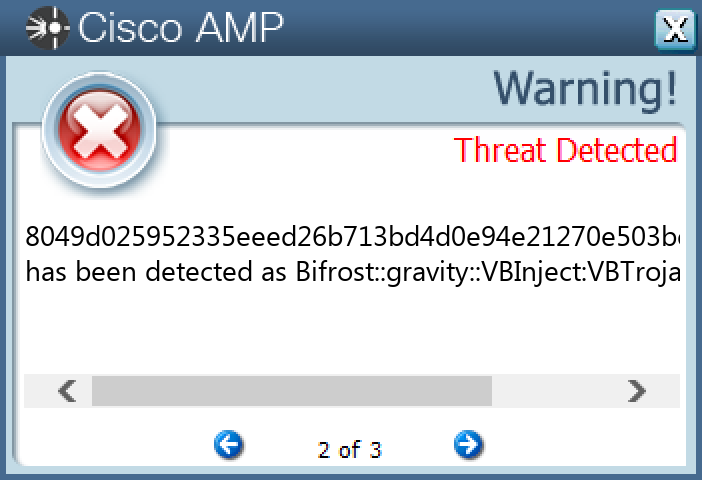
084dc3306858ab9f11034d16d0501a428d6bca1c87ff35f9e51f00309c372994088094d805941273abfdb59e583ce17ec3aca62b4536c8c69fdb7031182848620a9ee8eaad2a4f30d82b93ff3b5212b97ceb83e99410418ee37e151d0512fa971773cbf7d98b8c4e0c06ef18ba7184c2ced2b84160ab577a9ee75c583097c25a1d03f8d2e3b50d152aad6c4b419771a947bdaaa34d7844306116fc033fa208041e4718f6a64a05bfab681396a29588bfb53c513daf5797e7637acc7144e86a07255c46863d02a30cb9ee83df61cd7c64d0fdc07dca22b1dbff149d2905a2117c38e152f0162531bec131cd72a1b2dabde9db05146f62c6b949ff22ac94a37aca44e509007c8cbf8d218f8aa3cce3dfb9f95aaa1c16f4664125dbac54b6f0bf81495ab6d9993d6ca3ba252a3399eea0eeb1024b7483bf599389da459ec366316e4baa7eeb20a838eb0108cf84a4de3c4aad260e2b6077ccb2905cc5aa43e110bf52a6dfd20dc733393c7e00ce86fcf1ea3519c776ea6a5d24cfd9b58dfba9d3ad52c43009e2fe9ace2a375bf3ceee4f27bfb1133c451b96ed10cdda9a1469049b64d6d35fe7a4d2d3026a9195fcec34ef2e1751e47b7aefb728dd2b558a619b5a706929906d67d8670f15fe378c8dfd8df5eeaf29aba6689374dccec54a6df1877484eff0c8ecd8ea6ed2efde9e65a3dfacfd286c676fe9d2159427ba7b0eae107c4dbab37a8702b4c3299a28349db3e1d36c307ecbe95330ea41a0c5426f862a8049d025952335eeed26b713bd4d0e94e21270e503be8551d6a93c6a861554dd8dea08009858acb2dc2ab5d37af86067cbd9117df76912a178f7a2bed9b6e9b0959bf6dd78031b9c5479eb4a6bd1939e40e75865454b950ff2058bdd6a954bf4a099bfd621d82bdaab9dfef4dc379ab5e018456eaf801b93e9b03740d7fdcc90a6ed598c222d92a37d24d7f52c4589d7239d3d311737dfa83bab8dc46e7f662fa781183870f48fdc2b9047f34dbd9c9a7104f55dec98c31d10405c3c6cdef3cdab311c9d88db2eaaeb33d41ed93b17f05eef0e7ad81d24588bcf1a8f60fd11c2adcd113723cefba68b98d7f2ee7988fca18e826a46d723758a62d4949ba328b6
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
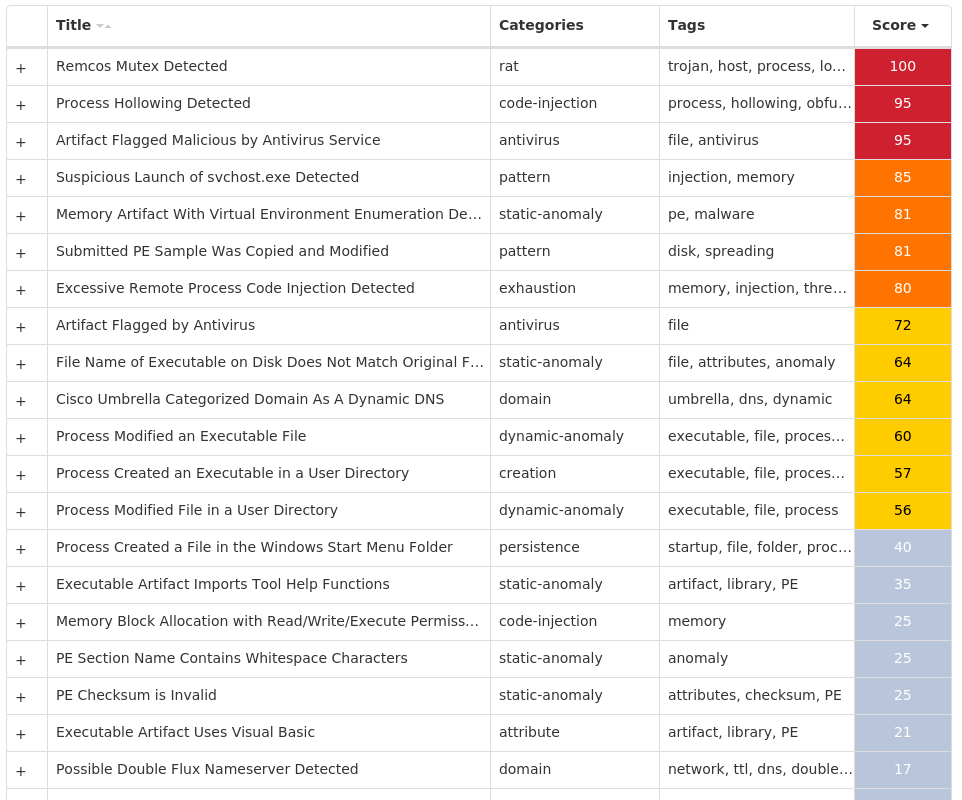
Screenshots of Detection
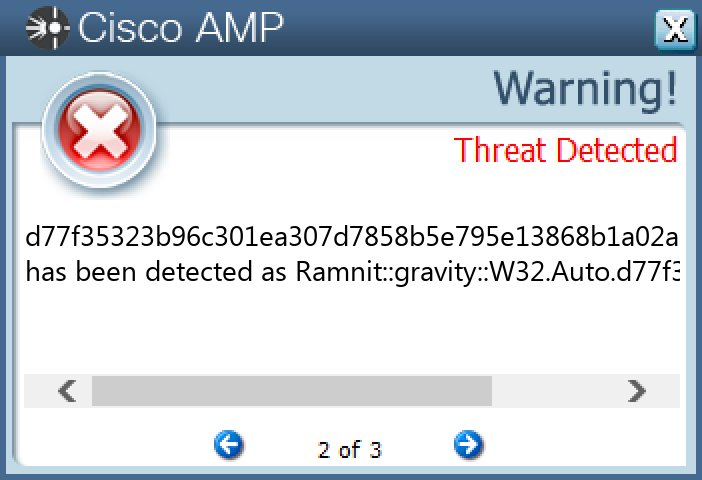
Secure Endpoint
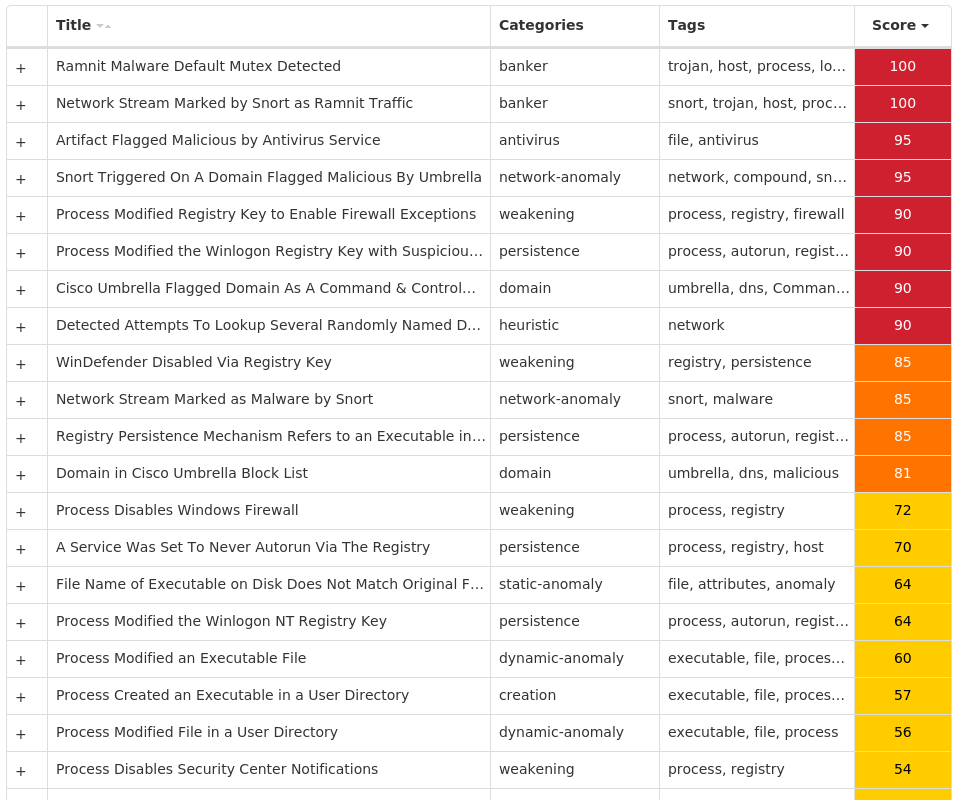
Secure Malware Analytics
MITRE ATT&CK
Win.Dropper.Tofsee-9997698-0
Indicators of Compromise
IOCs collected from dynamic analysis of 245 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER Value Name: DisableAntiSpyware 111
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoRebootWithLoggedOnUsers 111
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: NoAutoUpdate 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableBehaviorMonitoring 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableOnAccessProtection 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableScanOnRealtimeEnable 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableIOAVProtection 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE111
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES111
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS DEFENDER\FEATURES Value Name: TamperProtection 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER\REAL-TIME PROTECTION Value Name: DisableRealtimeMonitoring 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AUOptions 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: AutoInstallMinorUpdates 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS DEFENDER SECURITY CENTER\NOTIFICATIONS Value Name: DisableNotifications 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE\AU Value Name: UseWUServer 111
<HKLM>\SOFTWARE\POLICIES\MICROSOFT\WINDOWS\WINDOWSUPDATE Value Name: DoNotConnectToWindowsUpdateInternetLocations 111
Mutexes
Occurrences
Random name3
MSCTF.Asm.{00000009-4fb3f26-9d18-66b568-627b8a85e4b6}3
Global\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3
Session\1\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3
Session\2\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3
Session\3\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3
Session\4\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3
Session\5\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3
Session\6\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3
Session\7\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3
Session\8\MSCTF.Asm.{04fb3f26-9d18-66b5-6862-7b8a85e4b620}3
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
176[.]113[.]115[.]145124
185[.]11[.]61[.]1255
179[.]43[.]154[.]2163
192[.]229[.]211[.]1082
69[.]192[.]209[.]232
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
cacerts[.]digicert[.]com2
download[.]microsoft[.]com2
Files and or directories created
Occurrences
%LOCALAPPDATA%\Yandex89
%LOCALAPPDATA%\Yandex\YaAddon89
\x5c\x55\x73\x65\x72\x73\x5c\x41\x64\x6d\x69\x6e\x69\x73\x74\x72\x61\x74\x6f\x72\x5c\x41\x70\x70\x44\x61\x74\x61\x5c\x4c\x6f\x63\x61\x6c\x5c\x4d\x69\x63\x72\x6f\x73\x6f\x66\x74\x5c\x57\x69\x6e\x64\x43e\x77\x734
File Hashes
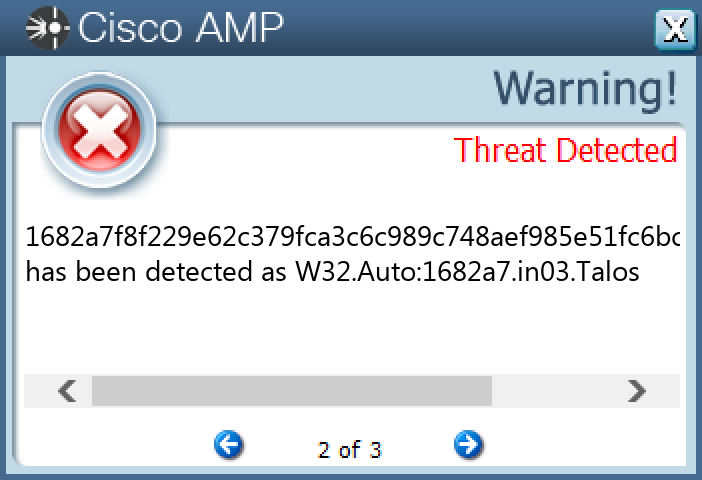
00206b2f652aaec449943e55d93ab85e9e87ef25f95578bde2ceed78feae3e7b00716c634467bb8fdf909ba82c19ab498f8ef0423fde2d52b87d7b1c6308c1a802f075f4410cd77c70e51d2cd3b3990845345e799b9d9e1c3a2f70871f3ccfa40383eb5111c99149f27feb3c4d216b8057424ed5dc107575eeab3384d667a7c103dd6172107745be428868d9dc148f027d332a488668b9d7e401f9e7d7345536047e794c09e7a4e7641574373a003bdd135ecb533b854464756e70f6dc46d55706116b9095938c053f1c92d0b959fafa15127c19b681d09e01d699d8b8d4245d06a539bbb4c43074abf5434c7291eac3f9fcb54beede07e3ff2aa087675c380f07075825ec1f57b3f3bfa84eb839d5013e53cfcf7970360b19607794ac9daa7107a571c2ba97badc98d92e522c3c84d0a1146b8eeae0172525b4ecd4b0e9a5eb07dfd38512fc0f4bc010f164a9bc16f5ae76f18567701f6c2fed14bc9b00e73c09f29244d4c89254e02426a2e9f8d783a190656154fe71a26495be0db69c5c2b0bfdb5d464b82ebedeef2fe7e0f78c7e802267e7702ea20bc72d4886afef099e0cec4fdbfad160dee0d939291083ee7b74adecf772f369c4a29839d1f5ee2b610d06e6076b309edb93b3cc71011970f69c371ed897fec2fbffec3d91e9c280cb0dc803cd1f73fbfd38c42e13ff263e64fffdaf624ed43c7cf6c477c702b92d2f0e391c41a2b2438935e818df13db66da10990306c514f431434ce37b2e9ce5e70fcc2c5d723b5b418beb83b215cfb294ac80c4f57d549f4fea04933b03cf058e118ad96124e17b7445562a4ef815719cc63b556a1f54db86bb8ab984e181d08a127af8143d8badde9f311fb806815f1a5f6fcc2f6a2d9a614b8221a1ec4331f216637a60cc0ff214fcbbdbc71cd93789ca61140ed2cef23a7fafd4a4fa81bd6a1682a7f8f229e62c379fca3c6c989c748aef985e51fc6bcf76d06bde9b0484cf16f405d2c293aa64c8b2fbd020332db2d7ae0b5ce00f33d659db6a5174ac27251878a7910e7d8aa1062bd5c7a7530984b22f0c8112d26836e2bdd1b8abf726e2189e0a0f6fdcc385d54bb131b256adf7e35e8e04b90f9d432047b2808d434f16
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
Win.Virus.Ramnit-9997699-0
Indicators of Compromise
IOCs collected from dynamic analysis of 12 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusOverride 12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: AntiVirusDisableNotify 12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallDisableNotify 12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: FirewallOverride 12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UpdatesDisableNotify 12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\SECURITY CENTER Value Name: UacDisableNotify 12
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\POLICIES\SYSTEM Value Name: EnableLUA 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: EnableFirewall 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DoNotAllowExceptions 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\SHAREDACCESS\PARAMETERS\FIREWALLPOLICY\STANDARDPROFILE Value Name: DisableNotifications 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MPSSVC Value Name: Start 12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION Value Name: jfghdug_ooetvtgk 12
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: JudCsgdy 12
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WUAUSERV Value Name: Start 12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: Windows Defender 12
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 12
<HKLM>\SOFTWARE\WOW6432NODE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON Value Name: Userinit 12
Mutexes
Occurrences
{7930D12C-1D38-EB63-89CF-4C8161B79ED4}12
{79345B6A-421F-2958-EA08-07396ADB9E27}12
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
35[.]205[.]61[.]6712
142[.]250[.]80[.]4612
103[.]224[.]182[.]24611
46[.]165[.]254[.]20111
72[.]26[.]218[.]7011
195[.]201[.]179[.]20711
208[.]100[.]26[.]24511
206[.]191[.]152[.]5811
72[.]251[.]233[.]24511
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
google[.]com12
testetst[.]ru12
mtsoexdphaqliva[.]com11
uulwwmawqjujuuprpp[.]com11
twuybywnrlqcf[.]com11
wcqqjiixqutt[.]com11
ubgjsqkad[.]com11
iihsmkek[.]com11
tlmmcvqvearpxq[.]com11
flkheyxtcedehipox[.]com11
edirhtuawurxlobk[.]com11
tfjcwlxcjoviuvtr[.]com11
Files and or directories created
Occurrences
%LOCALAPPDATA%\bolpidti12
%LOCALAPPDATA%\bolpidti\judcsgdy.exe12
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\judcsgdy.exe12
\TEMP\nr3othpeM12
File Hashes
0fdd4e8b236b7b01e9745b40b2aa848c3184bc4096cb9bc76ddb2dbd71ccc0935912fbc0929bfd2a39d4a2ac66a58fef95ff044958c81ce5d6698b4414b76cb26970bd6846357bbca2b52303d14264c191e386331a7d1559d2a9c0e14adf9b736c4b37cce41b603af1c66cca45b3046cf986de3e2e1b5fbd2aa99d6d1c75e6be6df703d95ae69f56dffee813cbf5dc26f4345634b0227d539eb4a886387793aa93de25c070a461c87ba30b2ebdbda3db2dacc313e67f857b58a5142530f9025c99842408d235fe06c71037073a1b7bf137d983b6a10dfc73fbec2f7ae683d5d4be88f9455c0409f685507107d010301af2d3d8f95354050e28e74e032655c215d5aa9fdeeb12bc2d009ab44b490a53d6795f8e4fb11ef09ba87d9bfbc497baa9d77f35323b96c301ea307d7858b5e795e13868b1a02a7f180ef44ade0e80a049e2428ab7ee60ac074aec6c51a0c8522e639d054f3a5498876f2d3b9a643189f1f2512b5637ddc1a42c03b8733aa7ec570cf9697825f8bf6fbcf23ed6a744a252
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
WSA
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
Win.Dropper.Remcos-9998831-1
Indicators of Compromise
IOCs collected from dynamic analysis of 10 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\MSWORDOFFICESVC-QHO80M10
<HKCU>\SOFTWARE\MSWORDOFFICESVC-QHO80M Value Name: EXEpath 10
<HKCU>\SOFTWARE\MSWORDOFFICESVC-QHO80M Value Name: WD 10
Mutexes
Occurrences
Remcos_Mutex_Inj10
Mutex_RemWatchdog10
mswordofficesvc-QHO80M10
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
kelikjoinset[.]freedynamicdns[.]org10
noblegas[.]myftp[.]org10
Files and or directories created
Occurrences
%APPDATA%\remcos10
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\mswordsvc.vbe10
%APPDATA%\mswordsvc.exe10
File Hashes
1068d5259b58c67b37559c2c5aaaffaa524cd38f05c99625b5b1bc97667388df38606579b809ca28086c04af33a2bf54fbbd5a045ef60052dda6775a6e71a875486aa0afed7943aed6838bce23d4d04410f9b5570ca90aa481f17ebecd2ad09453718f911be349fb0bb16c2cd3464a4a786c41d1f34ec4830cd5d5a1a50a9fde5678468ae9e47c877300c8de9d3f12dbd65f89bdc3af8838b30341f7451e3b7aba1a8e84a9bc1a73bfa49aeb376be2a18eff3a0e980fe0ebdb6ad5478b7e479dcc0ca5bdd31ae56f5585b16988ef09ffd914d5bb461c6692e086484f892988d4d2896ee59f6a2d1c1149c58e647e2c3dcdc7cb9011845a75254563f659298373d3f05239dda9f9c81b42d7ad5f83459f8183b8592c323aa17fbb04103c08be3dd74c4daab9d068fe6388596dc4daf7d93e61d1aa4868ec69f9ccd59eac2de1a8
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
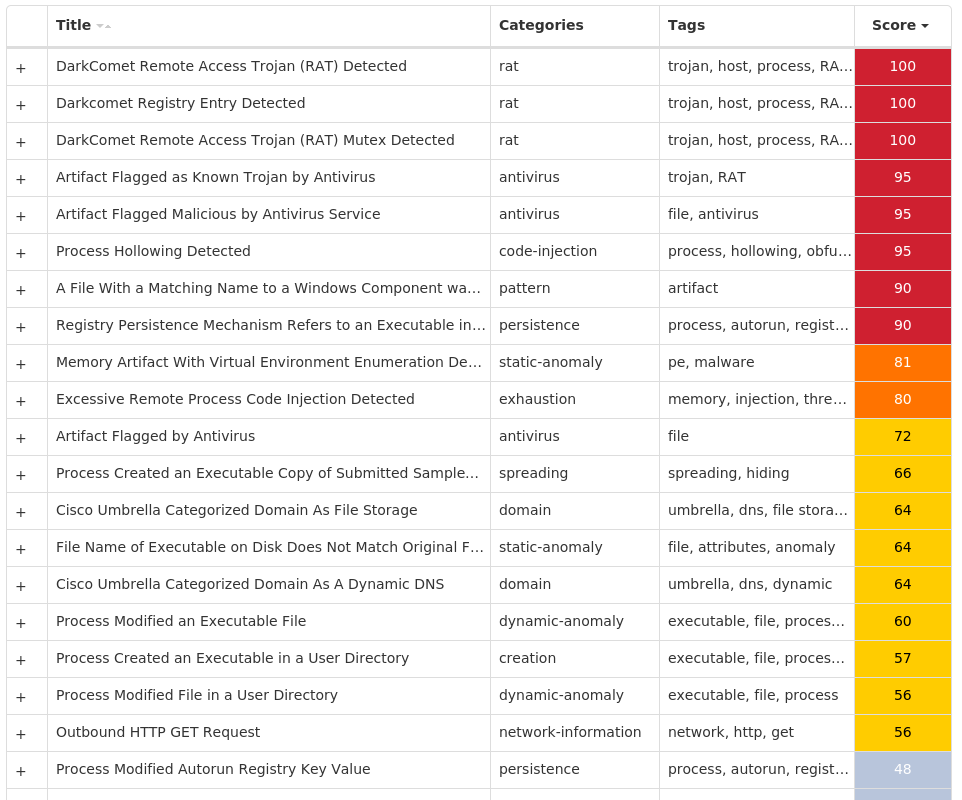
Win.Dropper.DarkComet-9998118-1
Indicators of Compromise
IOCs collected from dynamic analysis of 23 samples
Registry Keys
Occurrences
<HKCU>\SOFTWARE\DC3_FEXEC23
<HKCU>\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN Value Name: kb2456.exe 23
Mutexes
Occurrences
DC_MUTEX-13F3AYC23
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
162[.]125[.]4[.]1523
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
dl[.]dropbox[.]com23
zoukiny[.]no-ip[.]biz23
Files and or directories created
Occurrences
%APPDATA%\dclogs23
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp23
%TEMP%\tmpBD03.tmp.exe3
%TEMP%\temp_GujQurApmI2
%TEMP%\temp_GujQurApmI\svchost.exe2
%TEMP%\temp_AoPXtxyscR2
%TEMP%\temp_AoPXtxyscR\svchost.exe2
%TEMP%\tmpC06C.tmp.exe2
%TEMP%\temp_MhOpOytNAS\svchost.exe1
%TEMP%\tmpBF9C.tmp.exe1
%TEMP%\temp_dgFaHSHFIP\svchost.exe1
%TEMP%\tmpBAF0.tmp.exe1
%TEMP%\temp_XbxDBxrtQM\svchost.exe1
%TEMP%\temp_hYMuQAMQTy\svchost.exe1
%TEMP%\tmpBF44.tmp.exe1
%TEMP%\temp_AChkJWUFGO\svchost.exe1
%TEMP%\tmpC28E.tmp.exe1
%TEMP%\temp_ktuFuZaySw\svchost.exe1
%TEMP%\tmpCC7D.tmp.exe1
%TEMP%\temp_jTWgKpaNic\svchost.exe1
%TEMP%\tmpC453.tmp.exe1
%TEMP%\temp_gwLGQvZjwn\svchost.exe1
%TEMP%\tmpFFFB.tmp.exe1
%TEMP%\temp_gFRVVtvPLv\svchost.exe1
%TEMP%\tmpC0BA.tmp.exe1
*See JSON for more IOCs
File Hashes
0405c695532cdfadb49cd6e5dc0175e2740a6b34df032e0d6370ac57781bc0b9099393350020fa9d643c1fd02dd8e0c8e2c9090ff5d4ff96a807b03cc927dae60b9d53d8392c6af28951737704765fb1a7c75a849633ef4e4a1d7b7be861f6d71ba1034f63585a98afac1b985f866ec53e66ba500c8a7e499521e47e66e7867e276e6b279f8cf83b531fcee7fe2f770f1814b5d63ba25aa407bf1676698d09c72d67a134e9a81d3f55017c4c3e395e90194d6ad6cf2d24b6f567f9df0729f55e2ed27da0b1a0cf9949aba612b54427c7d104e1fe44c98e363b3cef43289d792437c13c62990a05a6105024b075eb672723a0838eadec043618b4222ca15520b53fe6cb53ea8f0a35f828fc1e87ad9cf6a27081695ef9b709fb3367c2e8c21e82506a3537c3afbb25783fe817f230595b3c7369eaf737ee84475a6ed1d5c5c5ec66d64aad782b2ba9baf1fa04c5738d55bd23754dba179b7c01fe15837ee6b6b7781529034cef2a9316fb18187611f911d2d6463f56636e7d6393045a88302614786be271e7f3f8249203417bd8547b42e3dceb9440e228d844a78c85f2dc78228534b61a4f0c0dc39da45ddf6a874edfbaf0ea9ab36c58f470ae3e062f81c6b288789c72981be3e3f57b31771ab73ad52089f65a8b5f0544d3ae5ed9e8b14f6e889b3fe85d94c61276540ea86de2de983c7d7357eaf394717e0705cd365a307f8f12b7340c8cc0c6c7c3c3f6ed64a3f8850fa035d1f811dc4255b128ab00d4c5a7b80aea4110f98e399e64abb923dee60f70650041593358297542c33f6b8a8eb83385710b54918cdb2814e555c0b6189a2c5ba46bc2cb0a435b5b8f5a5b51cbb837289b0f42bdfbe726dfafbae51a0b5cb5af21a3a2859bedaea7ab770d2482ca67b7e760c2d09004928da6736f4784cc05899ea7ae4bf19deb16d4fee047ced24f72779958896980e074e15cc9abb88daa041c13123525db3d6ee33be32b81ffe2607eec8bda28fc38b19bbef00cfcd572f3335b3773c4df758526243f128b
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
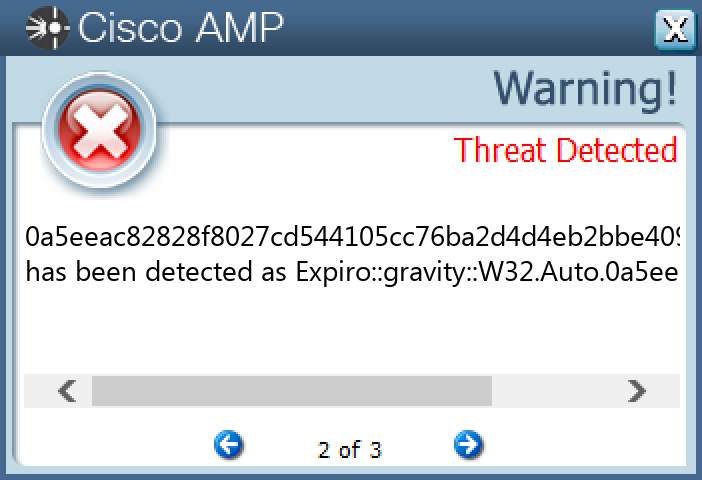
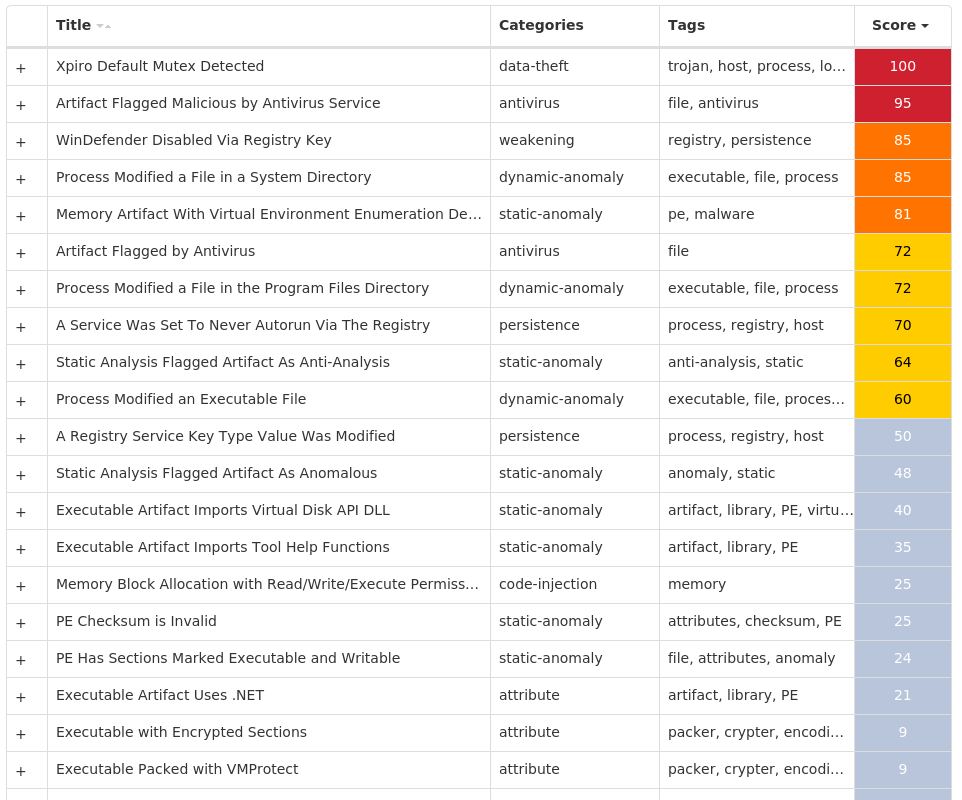
Win.Virus.Xpiro-9998650-1
Indicators of Compromise
IOCs collected from dynamic analysis of 18 samples
Registry Keys
Occurrences
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WSCSVC Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WINDEFEND Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_32 Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V2.0.50727_64 Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_32 Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\CLR_OPTIMIZATION_V4.0.30319_64 Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\COMSYSAPP Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MOZILLAMAINTENANCE Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\MSISERVER Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\OSE Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\UI0DETECT Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\UI0DETECT Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VDS Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VDS Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VSS Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\VSS Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WBENGINE Value Name: Type 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WBENGINE Value Name: Start 18
<HKLM>\SYSTEM\CONTROLSET001\SERVICES\WMIAPSRV Value Name: Type 18
Mutexes
Occurrences
kkq-vx_mtx6418
kkq-vx_mtx6518
kkq-vx_mtx6618
kkq-vx_mtx6718
kkq-vx_mtx6818
kkq-vx_mtx6918
kkq-vx_mtx7018
kkq-vx_mtx7118
kkq-vx_mtx7218
kkq-vx_mtx7318
kkq-vx_mtx7418
kkq-vx_mtx7518
kkq-vx_mtx7618
kkq-vx_mtx7718
kkq-vx_mtx7818
kkq-vx_mtx7918
kkq-vx_mtx8018
kkq-vx_mtx8118
kkq-vx_mtx8218
kkq-vx_mtx8318
kkq-vx_mtx8418
kkq-vx_mtx8518
kkq-vx_mtx8618
kkq-vx_mtx8718
kkq-vx_mtx8818
*See JSON for more IOCs
Files and or directories created
Occurrences
%ProgramFiles(x86)%\Microsoft Office\Office14\GROOVE.EXE18
%ProgramFiles(x86)%\Mozilla Maintenance Service\maintenanceservice.exe18
%SystemRoot%\Microsoft.NET\Framework64\v2.0.50727\mscorsvw.exe18
%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe18
%SystemRoot%\Microsoft.NET\Framework\v2.0.50727\mscorsvw.exe18
%SystemRoot%\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe18
%System32%\FXSSVC.exe18
%System32%\UI0Detect.exe18
%System32%\VSSVC.exe18
%System32%\alg.exe18
%System32%\dllhost.exe18
%System32%\msdtc.exe18
%System32%\msiexec.exe18
%System32%\snmptrap.exe18
%System32%\sppsvc.exe18
%System32%\wbem\WmiApSrv.exe18
%System32%\wbengine.exe18
%SystemRoot%\ehome\ehsched.exe18
%SystemRoot%\SysWOW64\dllhost.exe18
%SystemRoot%\SysWOW64\svchost.exe18
%SystemRoot%\SysWOW64\dllhost.vir18
%SystemRoot%\SysWOW64\msiexec.vir18
%SystemRoot%\SysWOW64\svchost.vir18
%ProgramFiles%\Internet Explorer\iexplore.vir18
%CommonProgramFiles(x86)%\microsoft shared\source engine\ose.vir18
*See JSON for more IOCs
File Hashes
09088e115dd96c2940801cc32dc155226eb967a307b9015f889ec4683b71a48b0a5eeac82828f8027cd544105cc76ba2d4d4eb2bbe409d1ef27835ce22a0ef062081057ccb7019073fe0b9606fe2a4e7258afc0644562c5458c41ede53c7b0b02f6c1972001b2d1f1d94916db33202cc724b5d18dca54867d5da63b8cc60a9223c6d806fcb5c653732f48445a1dcbc1005e6ba80e1c38118662e2abb1791a1013f77eca6fae88bb8491b548ed512e985f9cedc7e2dc8356a20050b388cc1fdd143d78d6a1608d210e08d0cddbc95f5408133b1b75f4b57ea3b452fddc1c78e1e49efca6296124551bcca7ba1fea36a3fb0de419601db1756c83c9269c0359eb35a15877c52ca982117a6a00e50fc0e090937dcc52990baaad693934a750bc1955c0cd3e42fc0b9b6c6fd054969d712c392db40a9280acbeeaa1149d42cae34226b33374ffb1cb5596388f80168376bb19776e526e02fbefc21bb971eed75966775416463a1bd3c9d771a4cbcc092d6d13c5979659b47da3c45640a716fe9ada079e4f7df197ed82e1594e12db8a5d4374ed2cae15748861a8606391746503bfdaf1a241cf02027feaba30e34b6403204352384efe43269dd870a74b51ac77020c2d4d9ba2963a5a20adab5d66cf0cbd62b2405159d01e60eb55a014a911a1d79d2530371c070d1c6743d97850ed70999538019b088faf4231d67962f202971efef64960868cb72ee318dcde7f5f50127587e7267f33f1a647ef05dfdb2071a28f40dd15849f3a79ce8202325eb54b6dacf76346e593445a055014e43cf03cca6
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
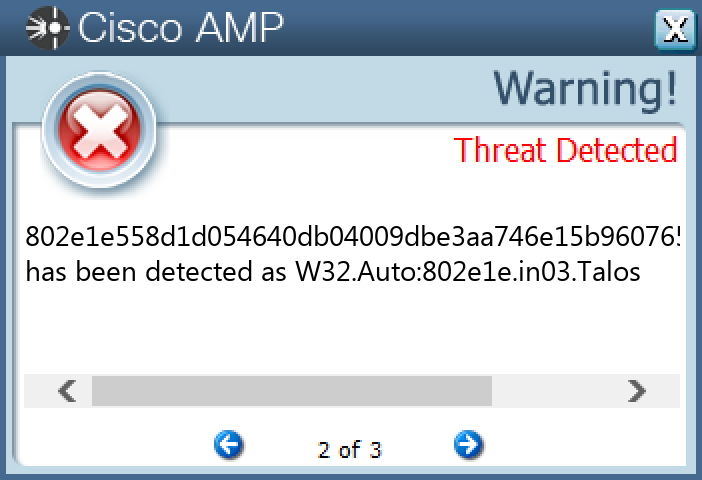
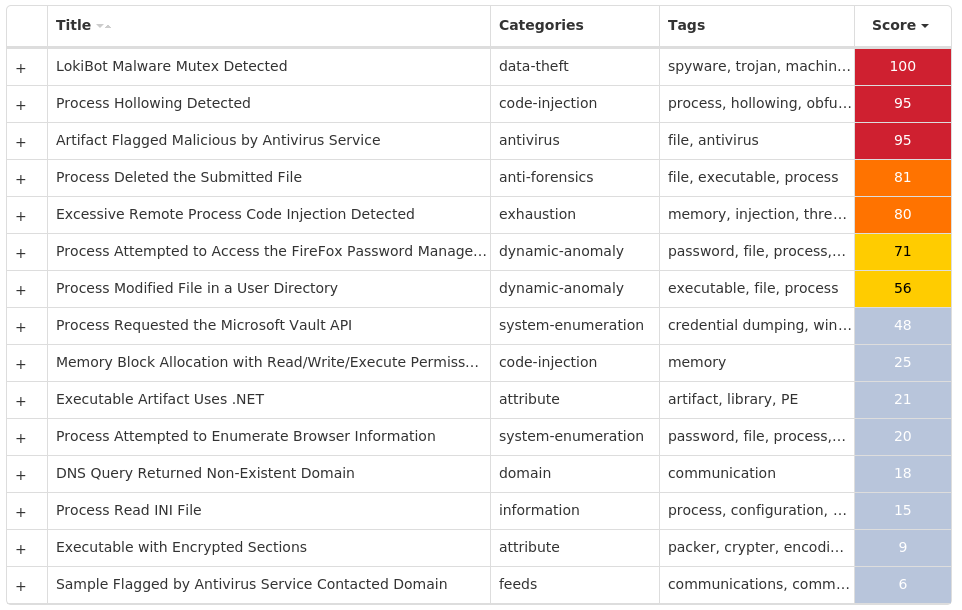
Win.Dropper.LokiBot-9997784-0
Indicators of Compromise
IOCs collected from dynamic analysis of 46 samples
Registry Keys
Occurrences
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: Path 2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: Hash 2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: Triggers 2
<HKLM>\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\SCHEDULE\TASKCACHE\TASKS Value Name: DynamicInfo 2
Mutexes
Occurrences
hGaolUAEhBhpUPhRKOMCEdZwRZtiMG20
jXKhDsqpdQybVuPEmbAKwiHxLWIux18
CbrYMlytSPCzlXpbEHuxopJkpncgG4
3749282D282E1E80C56CAE5A1
ATdPKSSVGkktNJiqkeIrKymIi1
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
34[.]229[.]94[.]22743
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
lancetasks[.]com43
poyrezbunker[.]xyz1
Files and or directories created
Occurrences
%APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\windrive.exe43
%APPDATA%\windrive.exe43
%System32%\Tasks\windrive43
%APPDATA%\Setupexe.exe42
%APPDATA%\D282E11
%APPDATA%\D282E1\1E80C5.lck1
%APPDATA%\Microsoft\Crypto\RSA\S-1-5-21-2580483871-590521980-3826313501-500\a18ca4003deb042bbee7a40f15e1970b_d19ab989-a35f-4710-83df-7b2db7efe7c51
File Hashes
05c8ba64b02dc62aba0fb1455ec15e121b172acbba66e1954643a580ce310d570861738aaef9328d136bb3d07a3d64259ed5123ed9c473cb69d08357e2c0a57a09403799c317cc67d029f6fbc01c8917e407cd9f26465f1580fa7607487e0d2c0dab311d96dac557c4504b2879e33ba995f12e739b16b094a52e0839a9606c241142c0e37678c3940d80bc05bf0b2428774c24fe99256d265db84f3983fe0a951ee30c4b53bd334c22d4ae24ae5b9253f657ecfc15c9d85075ab21b71547b31522272de4964a9f99e5eebf0f92c1c2a3a2ea7c858aa4f01aa274e100ef0f04742b1c6b2249d2c0a49e168341381431f8407b1871e3f1aa655cefd1f0e1e2d2ef2e846d46ddb277cc24e6a5ee4147397d16ce4421d034860e504217511e7207fd33f0e7d51bbef09378a752b47dffee4f6bb83c0042fecdf35e48323468b431e53409d8d2d1184a67cb56ef327383d00d8c749ece7732e952a78946e9925fad213d1dd0b1af801f27cb5639af28ed17f30900eaf4ceee050e2972303f92081960470b8bd5cdec3257b91ef325a77521b4ab804d6827284ad5a6d3c0a6c1a9645149566f476a01164aeee4f96a5321423eb718f19d97e04911e83b476a978432b84a1a9ee3a218ad5742a1f6fc58a14fedc56bb9fc35488ddfbf5a9ac660af7b984a3a2d78ca9cd193d984a2c511ee13afd818fa3b6df5b59a958c9b39d16838cb4adae5139b791d9beb9c9ec8d852e763986b90cffd4fe3df5c3e8436a67623fd50aa7ea0d282f6dfe7dd9ff774f254aa4375d50d0136460af8d15e571a0be7975fb7d55abc605e56218b2593cc2ec3769500132a106ac13a0e62232c9e76a04464b9769376d71aecd1383a5fe10fb8a3a95808dd9be96d02a5ce12b915c1795f653e8125e67e0a9b845617e4bdbf5ee8fa3e36e2f01b5b663e43186d3fd31f0c6b02d15580f3569d85f7514009d1619679571d23b25a6c0fea1947f4b8dd8544802e1e558d1d054640db04009dbe3aa746e15b960765458870228c4553fe509585510cf15298da5d428c191cce0e5baecfaa37fe754fbd6be307b7b47645886b88edc65514e9981fb2550061cccfad1e95fb642311fed93de4cfe854ec0d618a
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
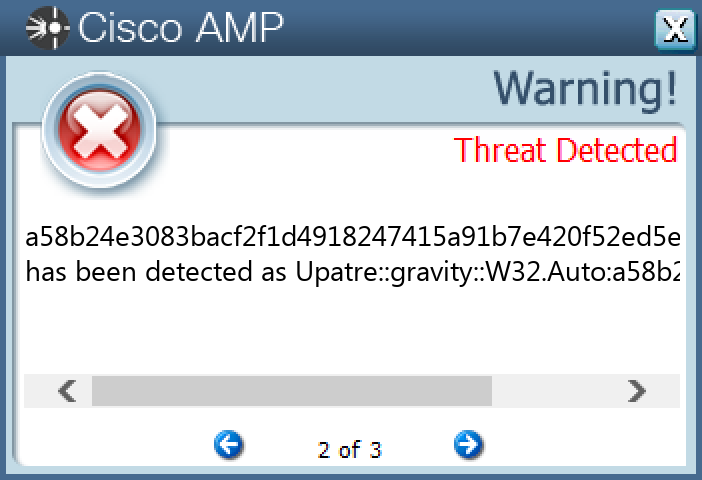
Win.Downloader.Upatre-9998551-0
Indicators of Compromise
IOCs collected from dynamic analysis of 25 samples
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
51[.]222[.]30[.]16425
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
groupesorepco[.]com25
bulkbacklinks[.]com25
Files and or directories created
Occurrences
%TEMP%\hummy.exe25
File Hashes
022151901a9b9625c6e127c544e70a9b3fa199914bf85163abbf70002e4a4009060f1a46303116655092db2863f1d3ecb84ec380e3d803ea6b337538fe0f4a3b07a178595827a67016935658a6d367039aa83ba93b499f06d16732d7895403b408d692463f8a2faa215615bca8d468610861cff2ca6fca6b0b890ea5194818d00a49e94fe253fd7dd6e9320b741c89bd994ecdbcba78b4e7eaf7fffba21951dd1225163fabc0b349956dd6967d665ab1fd2c8ce54766f55961292b3d62365dd1264c2c7b692c6dc0c577837c0c88b06408e538edb3fb2b7b2079df1dc9fa15b82e887c52e98a43a06e5673d2dd960fcae7e1b769f02256972351e2b3304e782141c69fd6c43ddf1dd7a8334667709dd03782ed4b6f392032726cc0dd3bdf8cc844b445cc2e1ccf169d3630cdda3d6bdc1e72d949e38756410fc36116582774ce49b33b88e96ce51cfbfb7fa518dcc312d8e018eed3b34a6d843de5c9e07973324af862559a2d8414ceab6bb806f20cb6a99de083c5d0f7a53ebe3f1d7a7914b94beda3336e7de2cb11541b84d0eb36f5347a2b15c8237c8ee07f6bac2ecfab1a4fd5becb2403b41d495b6008ddf37353271def2fd941855a4914b48d3ca148075913746a050b223ed031f12e9726cf37a70bc38cd0799ac6d495223b6e19e72264e01754390befb75a46a7ae6e4ab44945879826c53a5c72d747aacff513e3a96970374e466577dc8e6bc0251673d8bc148019febaf65adb8af01a1b2449a8d07131b420a9cfb3d58b0aa4010994cea8db6062ca4c58f8da2a1adf83572945d9797e11c3221d0724b2f08121872f794d7fff9507305797610d99773f7cee1fcb8018abd70eac615031bc1af69f0cda4b33a46bf8d8a0578614efcb43003dded78e19065c5857c931ff51fb58f697b256deb5cdfef8275c6c6cf66fd0a9b6a892a0c1a6b20042c3640808263720c71219d096a43a9dd5668d05828b6c55ef6579a3d887cc44c266383ac3ad501a5d85d6ddb5fb627e93f611ad216e5d9cf4a6eaa4ce1f1428a91c501661ae4711fd08fbb63a2682424b09190858a41fe72ce90ba58b24e3083bacf2f1d4918247415a91b7e420f52ed5ef7b32a9f929632eafd8
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
N/A
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
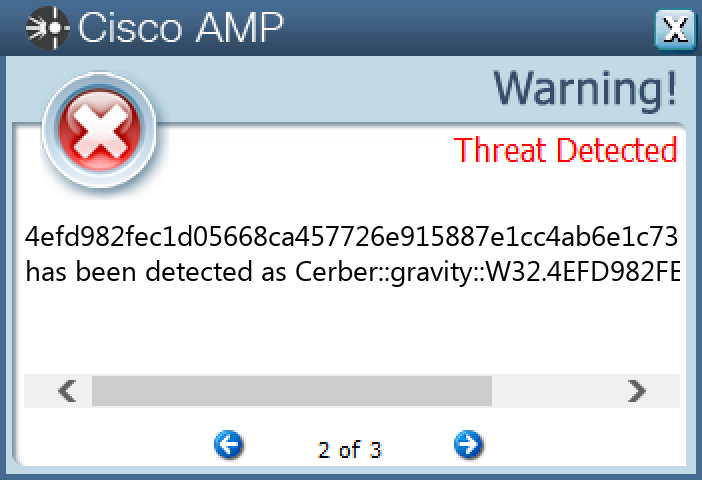
Win.Ransomware.Cerber-9998102-0
Indicators of Compromise
IOCs collected from dynamic analysis of 98 samples
Mutexes
Occurrences
ipc.{8067AF37-05F3-E0A7-F91D-CF35012EB051}96
itbeoinopoc96
IP Addresses contacted by malware. Does not indicate maliciousness
Occurrences
19[.]48[.]17[.]0/2796
77[.]12[.]57[.]0/2796
87[.]98[.]176[.]0/2296
178[.]128[.]255[.]17958
104[.]20[.]20[.]25133
104[.]20[.]21[.]25132
172[.]67[.]2[.]8831
104[.]26[.]8[.]8622
172[.]67[.]74[.]4921
104[.]26[.]9[.]8615
Domain Names contacted by malware. Does not indicate maliciousness
Occurrences
api[.]blockcypher[.]com96
bitaps[.]com58
chain[.]so58
btc[.]blockr[.]io58
qfjhpgbefuhenjp7[.]1bxzyr[.]top38
Files and or directories created
Occurrences
%TEMP%\d19ab98996
%TEMP%\d19ab989\4710.tmp96
%TEMP%\d19ab989\a35f.tmp96
%LOCALAPPDATA%\Microsoft\Office\Groove1\System\CSMIPC.dat96
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.tmp96
%TEMP%\tmp<random, matching [A-F0-9]{1,4}>.bmp96
<dir>\_R_E_A_D___T_H_I_S___<random, matching '[A-F0-9]{4,8}'>_.txt96
<dir>\_R_E_A_D___T_H_I_S___<random, matching '[A-F0-9]{4,8}'>_.hta96
\pc\users\public\recorded tv\sample media\win7_scenic-demoshort_raw.wtv69
File Hashes
002d43089d0c4ef3f41fda3ebffe0e392bd4115d91eb3964c459937d2972ccea06fbbf4aa44810136e505633664deb2ff4e69e738b0c8f1cffe7ecbe452fba580fb57fbf3813e474e366359b9bbc5bec917ad5aeec20f7257948a58b9e9cbb5210a4d53ec40c1458401eab89abdd5d03f4f95752d3f3acc714b0a156bc1c7ea61414ae8cf2ff8cd18b13fc9e982ee5e47afdd01ce2410bf14439bd21e574cd44149a4a692b40f85e1f99c4a1f631c0bb992af72ac8eff6c08a6df80179dfbabb1ada8fd30118dcc7fae7041c77b2dc77a4f844a4ca8daa146c1a436b4bf218551c28c2b98c6ab6b847913389ea8717e937edb24cd15302a37560d96ba2d2f02d22d6fc92916deb2d4477c2ecaff01d67253e2f743f265b9848caef3b43a463ae23ae4d7d6b10a77eb3b9a3899dd29292e866ffbea4623917e08374d1780223f1256137af5a5461431c81be000cf5c2cf6643be5f87366e330e3ee3f2876847e92a943c6f4117f3dab6e00135c93de17ae26e4e5e62ffe5587534267535868641361d0422b5b5e47076e0f0e4fa476649d3073e31b097572649e60d484fcfc31b3c8bf29f6c52f87c6e08d72a28551b5569ef7951eb96b16b63411c8a3f1323683d5349995dafd20c20632181b23fa5c12d63e3e086ffc2594ecf0373ac0d0ab53da3f20dc7ed83797ce0752b7f31c4008e5a08d3a27ce8a55d5a78ba5093fb513e541d44a3212fcb8c051aecdb6107814753bdd7644f7b982a098719eefe48db3ebbfd0af3a85e6911f525726a80ebfc85aab7b1b7500d6fc102b13c16b1deb33feb42368dc1cefc4646912317a9eb3ce5d6e05c5ea0f123613c38e15d02d726438b78222723877653f1fb18066a802f58374d5841cc1df518d83f1293052e5e4965fd6dab40b061bfe2ca234e23b43a60de765958f59b327d3aec29077a13b74c41f045065a4fca849d0b189024c9aa734cc7e0a7805e5df8c9be222edaccb24dea0603c4c2148572b523417470fe7669cf671b9ea21ae8ffbff58ce21f23bd4efd982fec1d05668ca457726e915887e1cc4ab6e1c735e8e11b9fd2b8530faa524c3ef042a214e02c846d09cb3e394ce811638ba6d4000df3320f63aaf29a8b
Coverage
Product
Protection
Secure Endpoint
Cloudlock
N/A
CWS
Email Security
Network Security
Stealthwatch
N/A
Stealthwatch Cloud
N/A
Secure Malware Analytics
Umbrella
N/A
WSA
N/A
Screenshots of Detection
Secure Endpoint
Secure Malware Analytics
MITRE ATT&CK
from Cisco Talos Blog https://bit.ly/3NlefyC
via
IFTTT








No comments:
Post a Comment