- A previously unreported phishing-as-a-service (PaaS) offering named “Greatness” has been used in several phishing campaigns since at least mid-2022. Greatness incorporates features seen in some of the most advanced PaaS offerings, such as multi-factor authentication (MFA) bypass, IP filtering and integration with Telegram bots.
- Greatness, for now, is only focused on Microsoft 365 phishing pages, providing its affiliates with an attachment and link builder that creates highly convincing decoy and login pages. It contains features such as having the victim’s email address pre-filled and displaying their appropriate company logo and background image, extracted from the target organization’s real Microsoft 365 login page. This makes Greatness particularly well-suited for phishing business users.
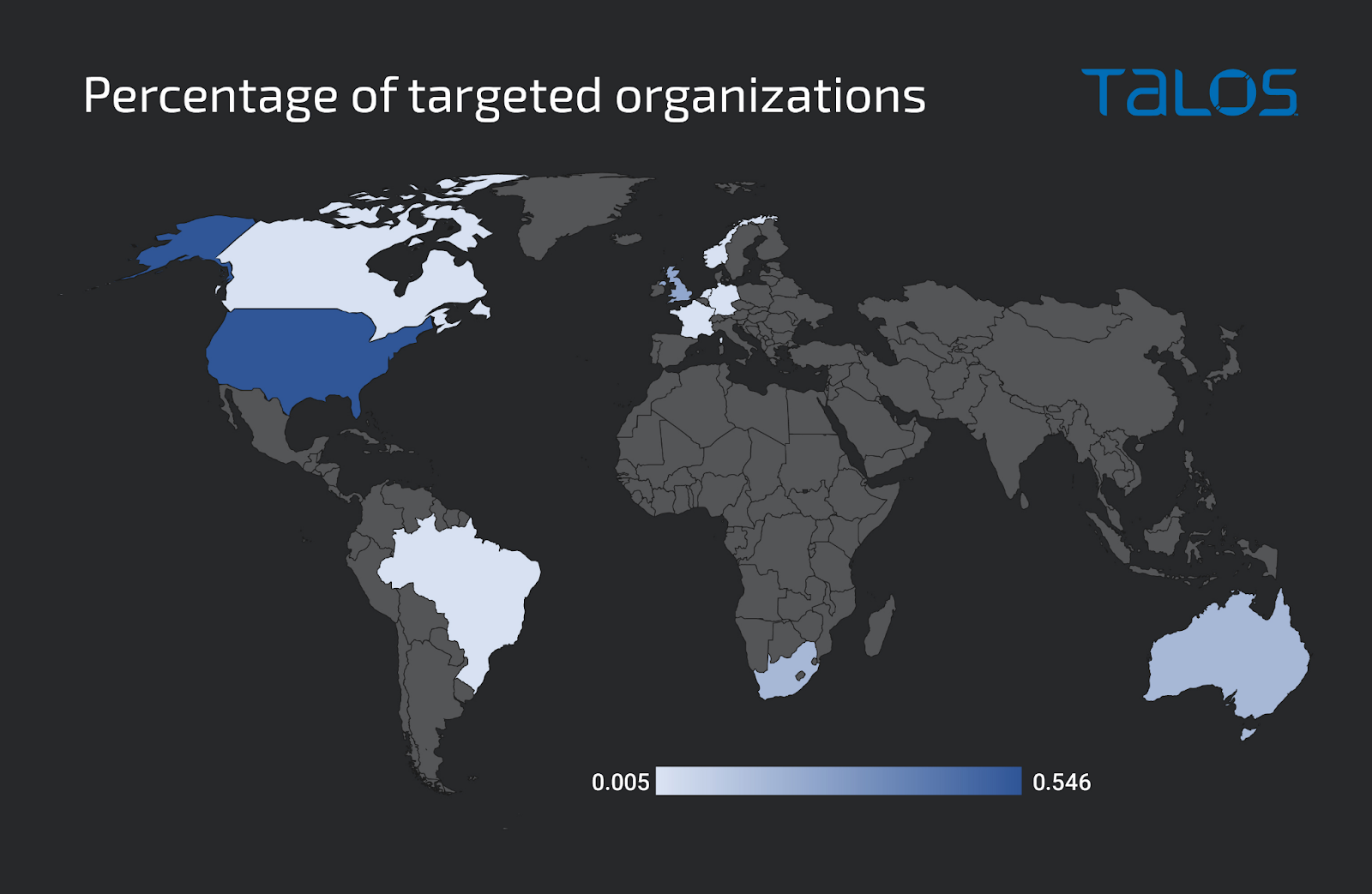
- An analysis of the domains targeted in several ongoing and past campaigns revealed the victims were almost exclusively companies in the U.S., U.K., Australia, South Africa, and Canada, and the most commonly targeted sectors were manufacturing, health care and technology. The exact distribution of victims in each country and sector varies slightly between campaigns.
- To use Greatness, affiliates must deploy and configure a provided phishing kit with an API key that allows even unskilled threat actors to easily take advantage of the service’s more advanced features. The phishing kit and API work as a proxy to the Microsoft 365 authentication system, performing a “man-in-the-middle” attack and stealing the victim’s authentication credentials or cookies.
Activity and victimology

Greatness seems to have started operating in mid-2022 and, based on the number of attachment samples available on VirusTotal, there were spikes in activity in December 2022 and March 2023.
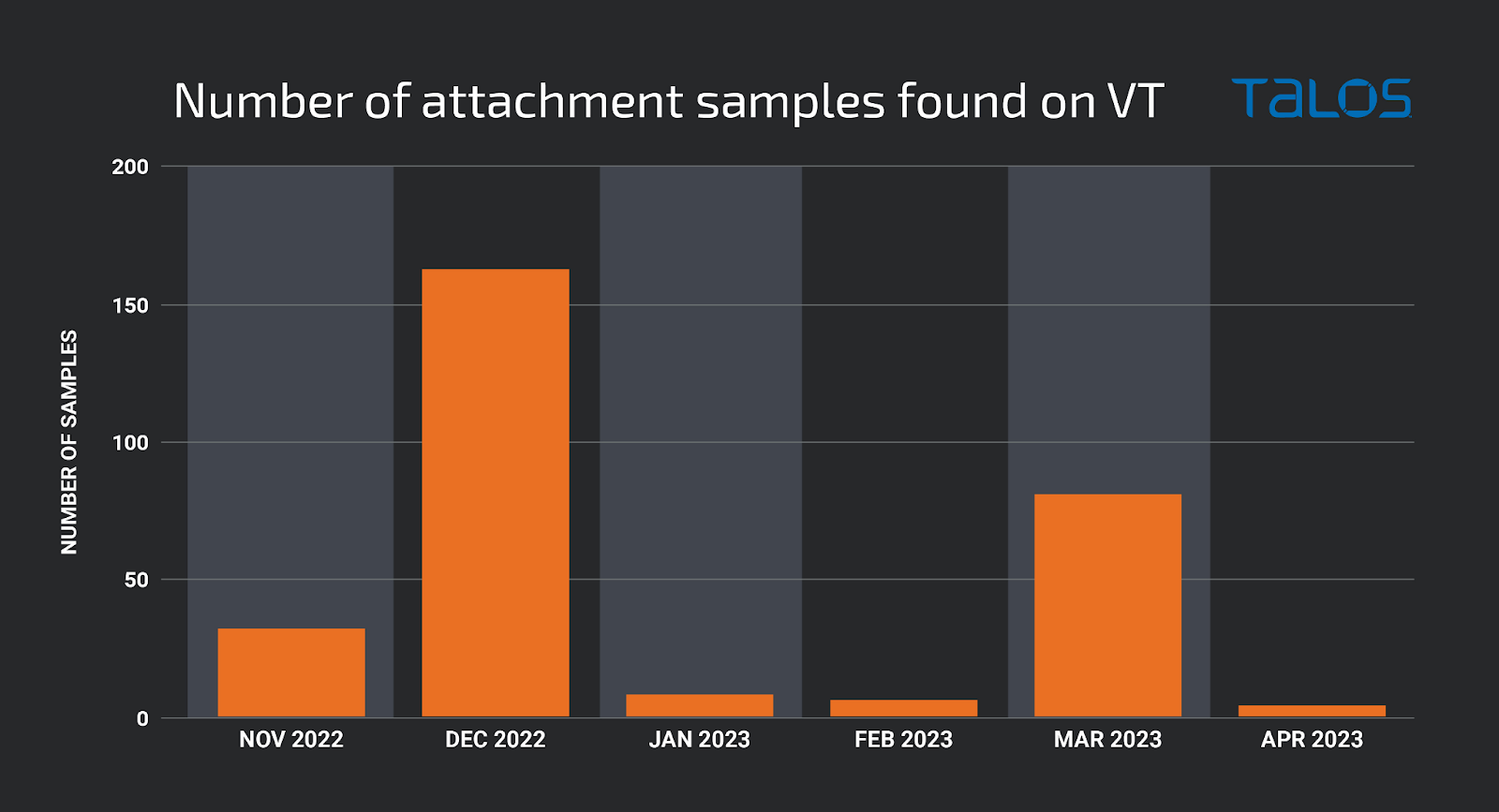
Although each campaign had a slightly different geographic focus, collectively, over 50 percent of all targets were based in the U.S. The next most-targeted countries are the U.K., Australia, South Africa and Canada.
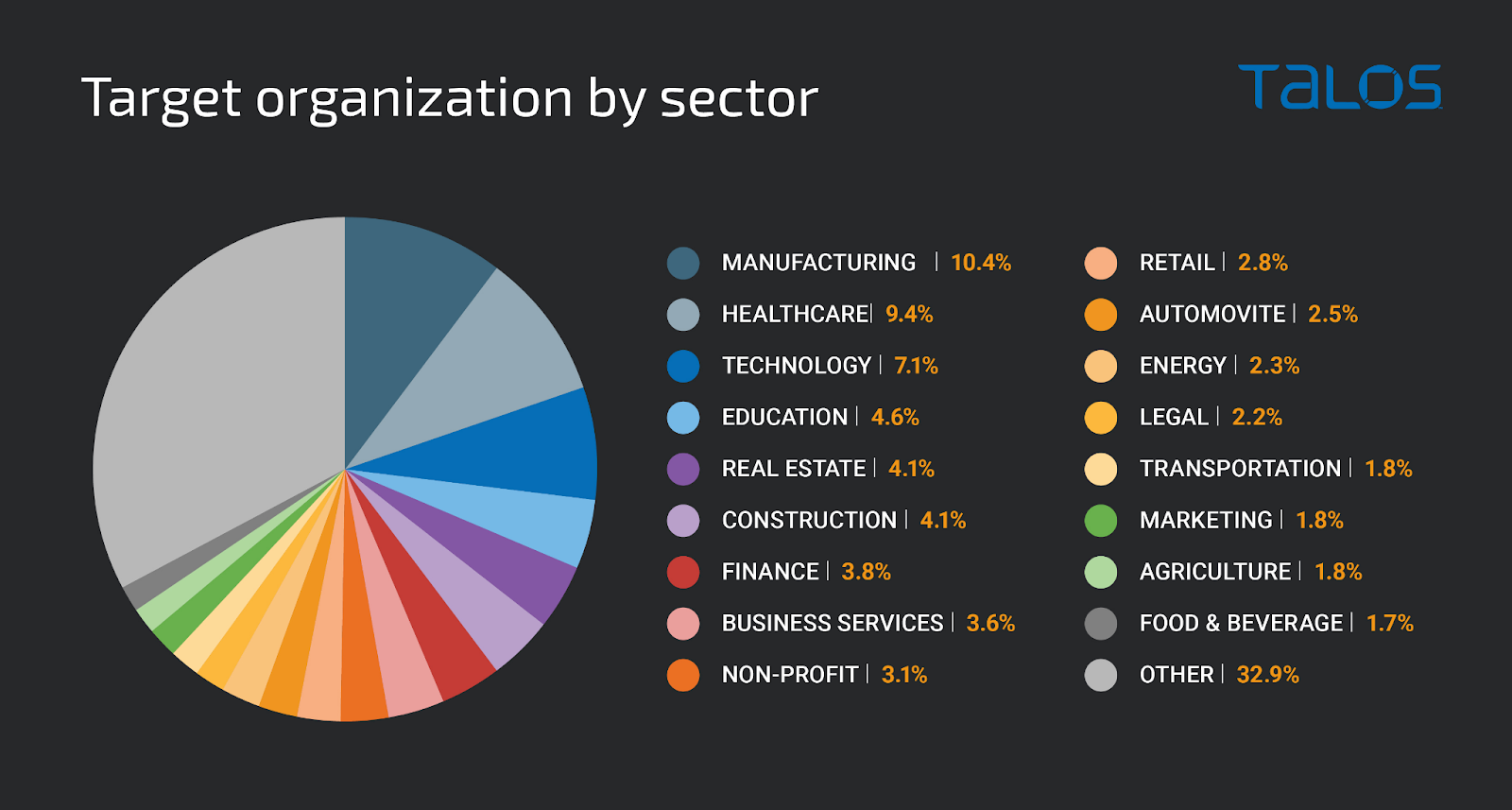
Greatness is designed to compromise Microsoft 365 users and can make phishing pages especially convincing and effective against businesses. Based on the data Cisco Talos obtained, Greatness affiliates target almost exclusively businesses. An analysis of the targeted organizations across several campaigns shows that manufacturing was the most targeted sector, followed by health care, technology and real estate.
The attack flow
The attack starts when the victim receives a malicious email, which typically contains an HTML file as an attachment and, under the pretext of a shared document, leads the victim to open the HTML page.
Once the victim opens the attached HTML file, the web browser executes a short piece of obfuscated JavaScript code that establishes a connection to the attacker's server to obtain the phishing page HTML code and display it to the user in the same browser window. This code contains a blurred image that shows a spinning wheel, pretending to load the document.
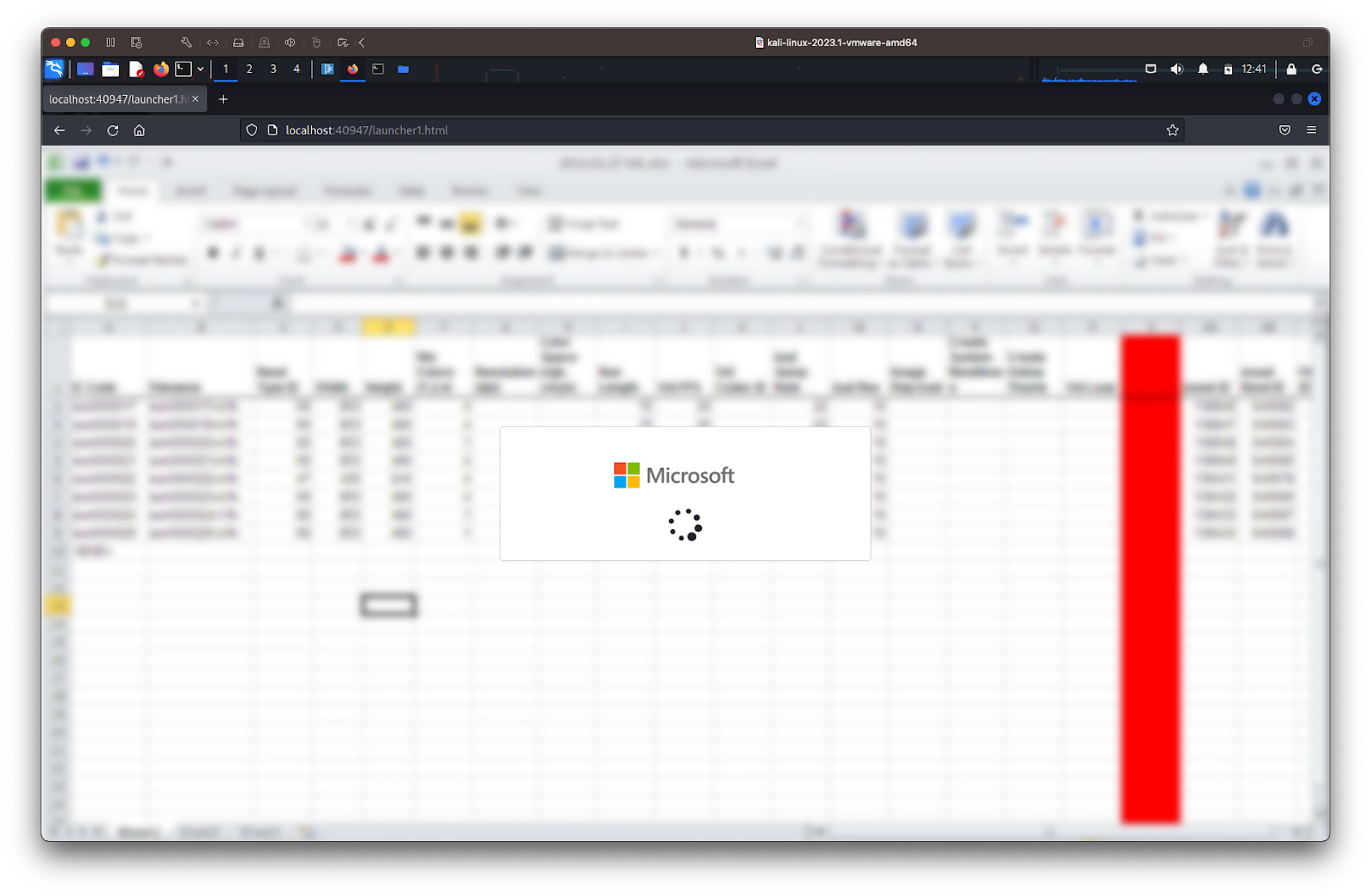
The page then redirects the victim to a Microsoft 365 login page, usually pre-filled with the victim’s email address, and the custom background and logo used by their company. In the following example, for privacy reasons, we manually replaced the real victim’s email address, background image and company logo on an actual phishing sample with fake Talos data, to show what it looks like.
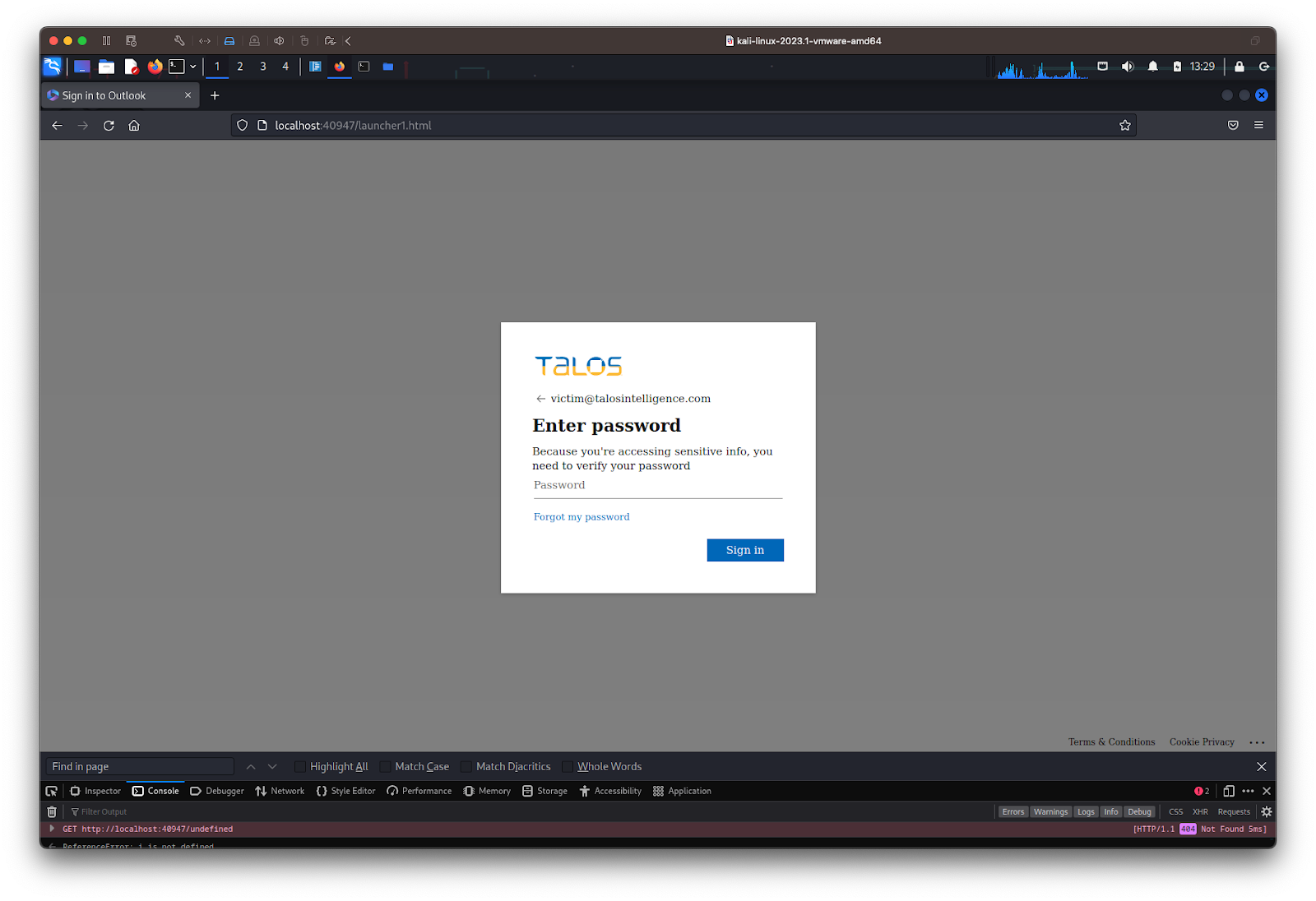
Once the victim submits their password, the PaaS will connect to Microsoft 365, impersonate the victim and attempt to log in. If MFA is used, the service will prompt the victim to authenticate using the MFA method requested by the real Microsoft 365 page (e.g., SMS code, voice call code, push notification).
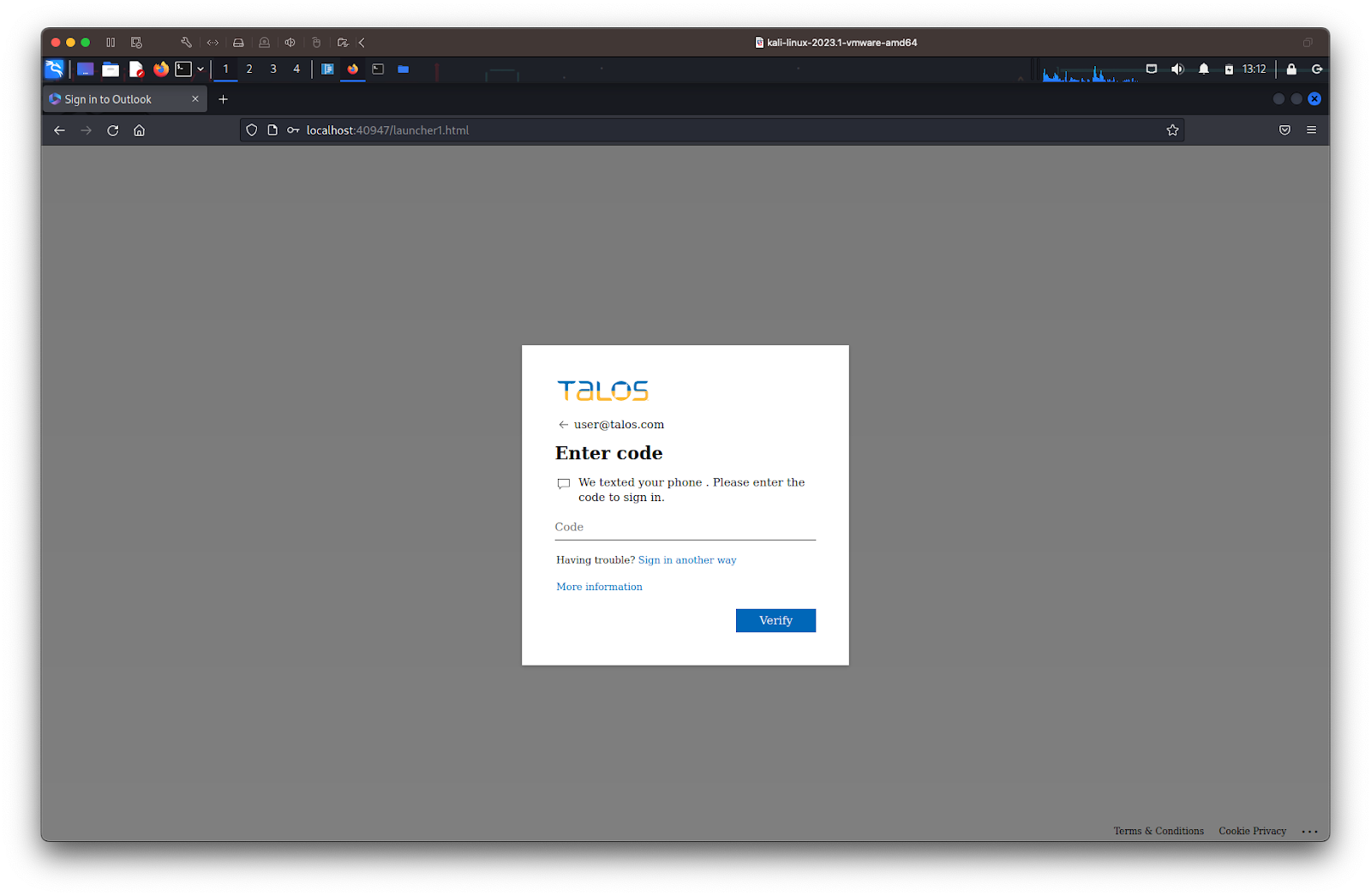
Once the service receives the MFA, it will continue to impersonate the victim behind the scenes and complete the login process to collect the authenticated session cookies. These will then be delivered to the service affiliate on their Telegram channel or directly through the web panel.
The phishing service
The service consists of three components: a phishing kit (which contains the admin panel), the service API and a Telegram bot or email address.
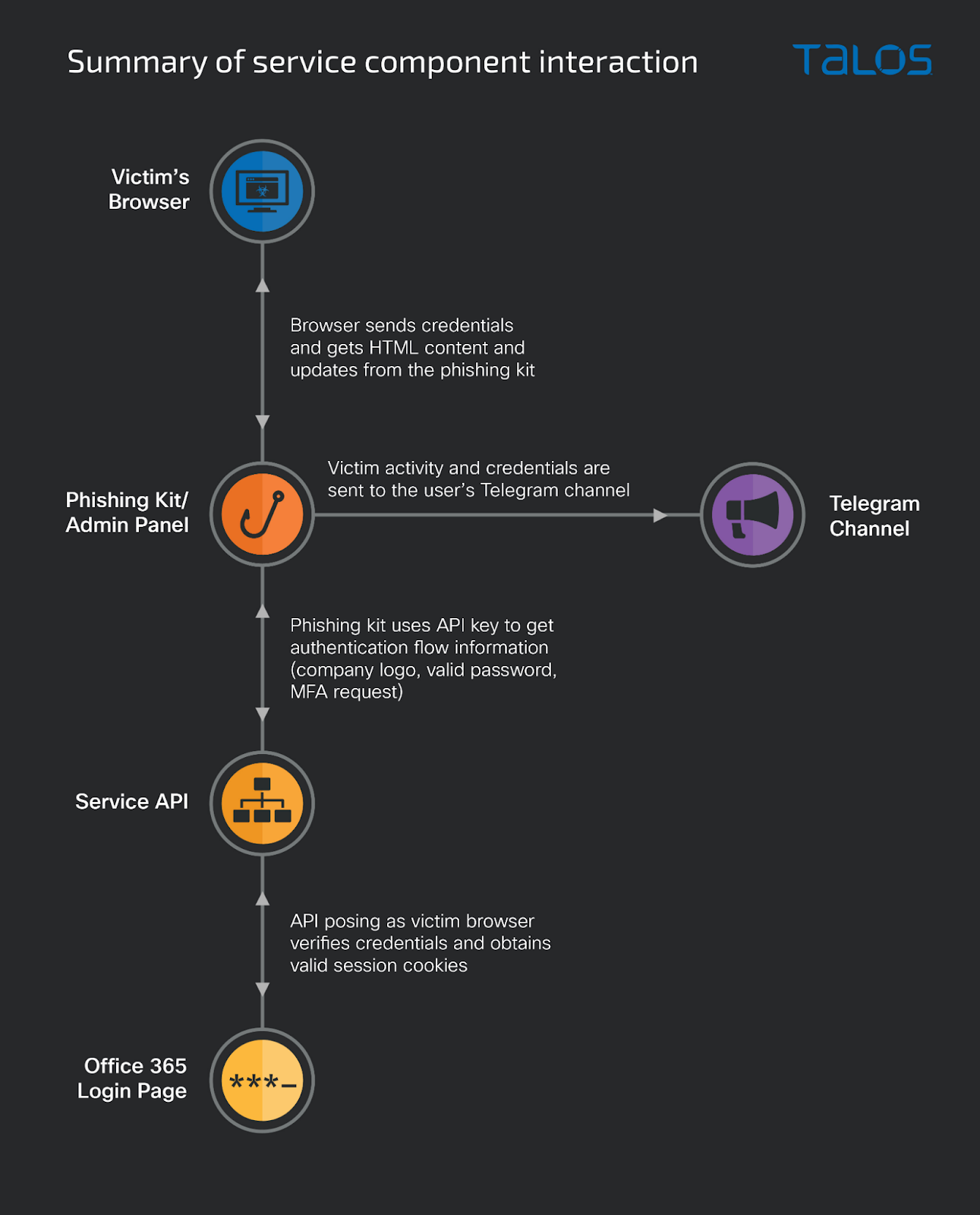
The phishing kit, the service component delivered to affiliates and deployed on a server controlled by them, is the only part of the service the victim connects to. The kit delivers the HTML/JavaScript code for each step of the attack. The kit communicates with the PaaS API service in the background, forwarding the credentials received from the victim and receiving information on what page it should deliver to the victim at each step of the attack. As the victim submits their credentials to the kit, it stores them locally so they can be accessed via the administrative panel and, if configured to do so, sends them to the affiliate’s Telegram channel.
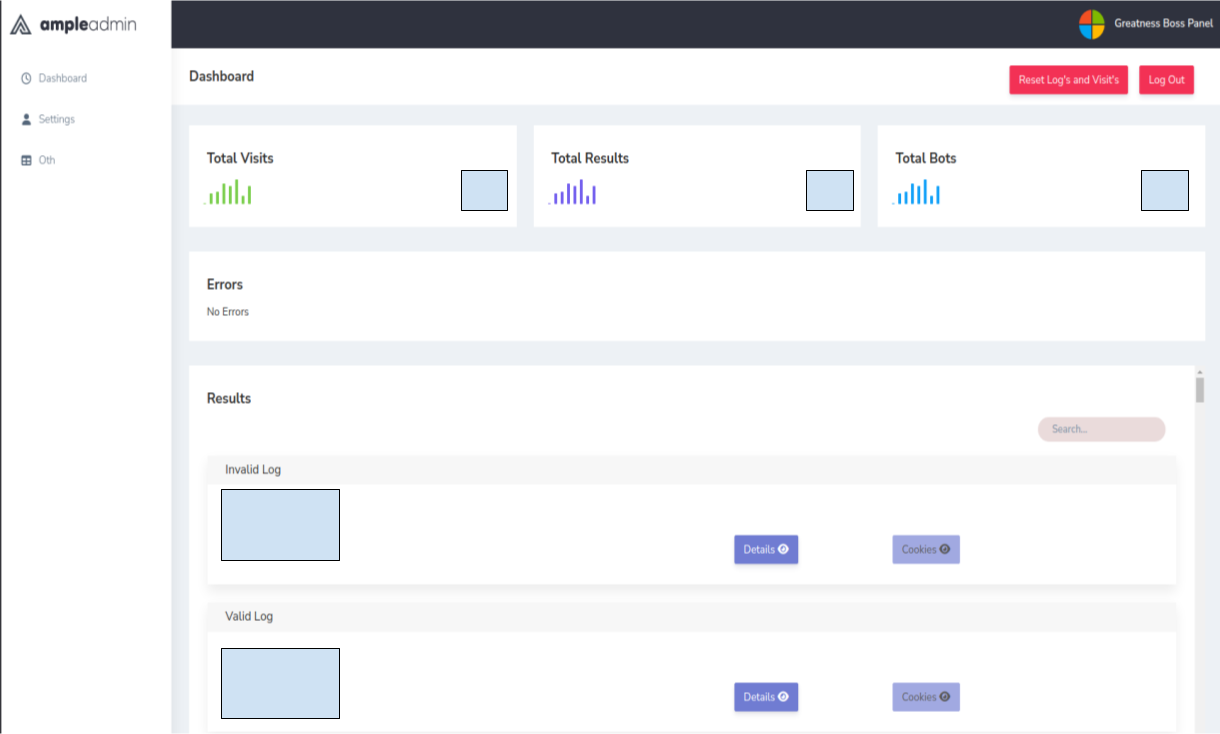
The phishing kit contains an administration panel that allows the affiliate to configure the service API key and Telegram bot and keep track of stolen credentials. The following images show an example of the administration panel login page and dashboard.
The administration panel also builds malicious attachments or links that are submitted via email to the victims. The following image shows the form used to generate the attachments:
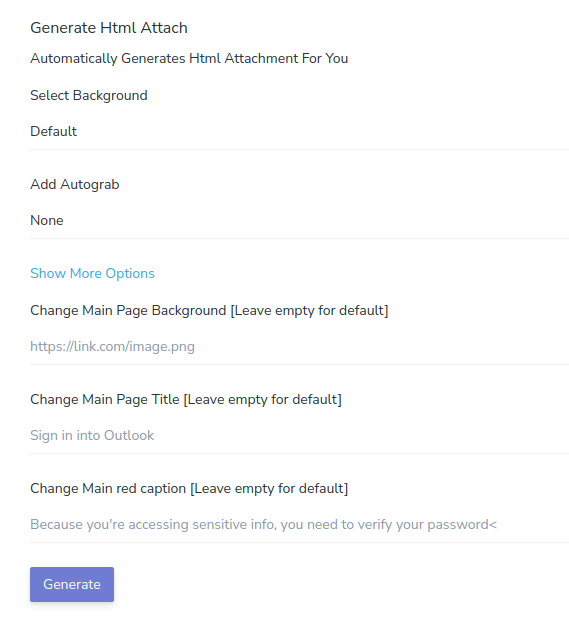
The PaaS is designed to be used in a very standard way. The payload delivered to the victim must be a link or, more commonly, an HTML attachment. The attacker can use the builder form above to create a payload with a few options:
- Autograb: This feature prefills the Microsoft 365 login page with the victim’s email, adding credibility to the attack.
- Background: The attacker can select the fake attachment background image to be a blurred Microsoft Word, Excel, or PowerPoint online document.
The API is the core part of the service. Each affiliate must have a valid API key to use Greatness, or else the phishing page will not load and displays a message saying the API key is invalid. The following image shows the configuration options available in the panel, where the affiliates can insert their API key.
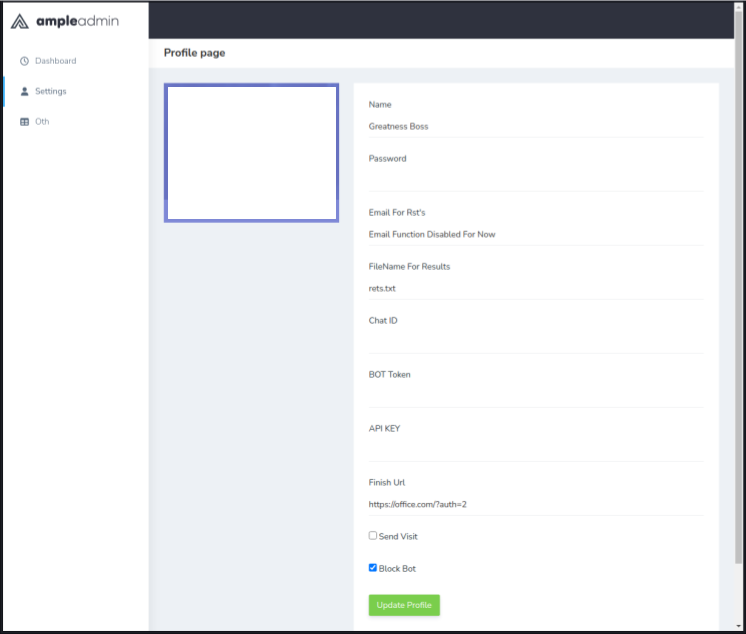
The service API contains logic to validate the affiliate’s key, block unwanted IP addresses from viewing the phishing page, and most importantly, behind-the-scenes communication with the real Microsoft 365 login page, posing as the victim.
Working together, the phishing kit and the API perform a “man-in-the-middle” attack, requesting information from the victim that the API will then submit to the legitimate login page in real time. This allows the PaaS affiliate to steal usernames and passwords, along with the authenticated session cookies if the victim uses MFA. Authenticated sessions usually time out after a while, which is possibly one of the reasons the Telegram bot is used — it informs the attacker about valid cookies as soon as possible to ensure they can reach quickly if the target is interesting.
Coverage
Ways our customers can detect and block this threat are listed below.
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
The following Snort SIDs are applicable to this threat: 61708.
Indicators of Compromise (IOCs)
IOCs for this research can also be found at our GitHub repository here
from Cisco Talos Blog https://bit.ly/3Bjglru
via IFTTT
No comments:
Post a Comment