Cyber Sanctions | Russian National Faces Multiple Charges for Ransomware Operations
The US government has announced cyber-related sanctions on Mikhail Pavlovich Matveev; a Russian national also known as Wazawaka, m1x, Boriselcin, and Uhodiransomwar online. For his alleged involvement in targeted hijacking activities against American law enforcement, schools, and businesses, Matveev faces charges for conspiring to damage protected computer equipment, conspiring to transmit ransom demands, and intentionally damaging protected computers. All charges, if convicted, spell a 20-year prison term at the very least.
Operating out of his native Russia, Matveev reportedly led several campaigns using LockBit, Babuk, and Hive ransomware since 2020, earning him some $200 million in ransom demands over the years. The DoJ’s press release noted that these campaigns have affected thousands of victims, including healthcare entities, and government agencies. Information leading up to Matveev’s arrest will be rewarded up to $10 million and he has been added to the FBI’s Most Wanted List.
LockBit, Babuk, and Hive ransomware all share a similar modus operandi. They involve an intrusion via a vulnerable computer system leading to encryption and data theft. Both LockBit and Hive are ransomware-as-a-service (RaaS) groups infamous for leveraging double extortion against their victims. While Hive was shut down by authorities earlier this year, LockBit ransomware continues to be prolific. As for Babuk, its source code was leaked two years ago but this has since spawned at least ten new ransomware families. In an interview given last summer, Matveev confirmed that he was one of the original developers and administrators behind Babuk.
According to the U.S. Treasury, 75% of all ransomware-related incidents are traced back to Russian-backed attackers and the top five highest grossing variants available today are connected to Russian threat actors.
macOS Attacks | Increased Threat Level After Appearance of New Zero Days and Attack Frameworks
It’s been a busy week in macOS security. A Go-based implementation of Cobalt Strike Beacon called ‘Geacon’ was this week reported to be on the rise, while Apple issued patches across its operating system platforms for multiple software bugs, including three zero day vulnerabilities.
An open source port of well-known attack simulation kit Cobalt Strike was paid little attention when it debuted on GitHub some four years ago, but two forks of the Geacon project, Geacon Plus and Geacon Pro, which appeared late last year appear to be behind a rising number of sightings of Geacon in the wild.
SentinelOne’s report this week highlighted two examples of Geacon payloads being packaged inside fake macOS applications. One case featured an application bundle masquerading as SecureLink, a legitimate enterprise application used for remote support, with a Geacon Pro payload.
Late on Thursday, Apple also released fixes for three zero day bugs, CVE-2023-32409, CVE-2023-28204, and CVE-2023-32373, in its WebKit browser engine, widely in use by Safari and other browsers across Apple’s platforms. CVE-2023-32409 is a sandbox escape that allows malicious code embedded in webpages to execute outside of its protected container. CVE-2023-28204 may enable attackers to access sensitive information on the device via maliciously crafted web content, and CVE-2023-32373 may lead to arbitrary code execution. In all three cases, Apple says it is aware of reports that the bugs may have been actively exploited.
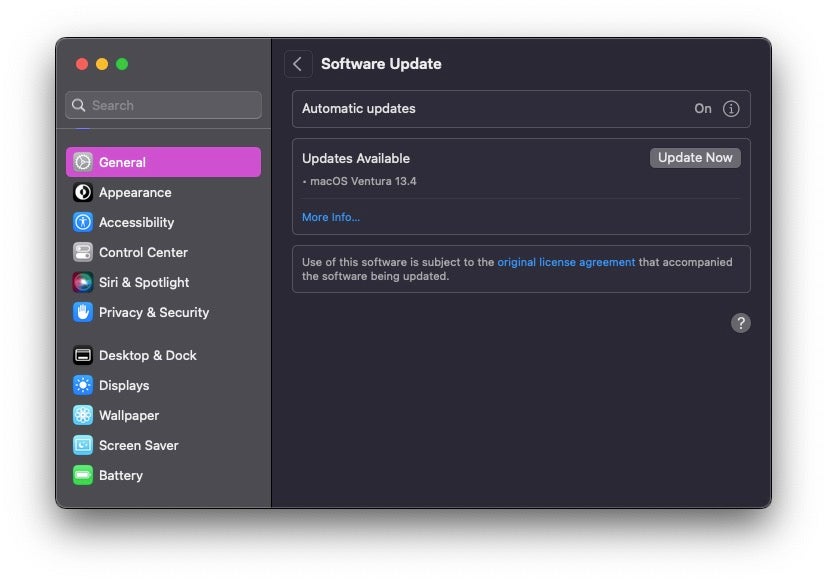
The security flaws impact a wide range of Apple devices and operating system versions, and updates are available for Big Sur, Monterey and Ventura versions of macOS, as well as iOS, iPadOS, watchOS and tvOS. Users are urged to apply patches as soon as possible.
Social Engineering | Potential Risks Surrounding Google’s New Top-Level Domains
Two of Google’s newly released top-level domains (TLD), .zip and .mov, have cybersecurity experts warning against potential phishing and malware attacks. Earlier this month, Google introduced eight new TLDs to the general public, available to anyone purchasing a domain. Since .zip and .mov are widely-used file extensions, the release gives threat actors another way to trick unsuspecting users who think they are accessing legitimate compressed files or videos into clicking malicious URLs.
To further the cause for concern, some online messaging platforms and social media automatically convert ZIP files into clickable links, leading the user quickly to a website of the same address. Since internet users regularly post instructions that reference zip files and videos directly, threat actors could begin to create malicious sites named after commonly-shared files to launch phishing schemes or deploy malware onto the victim’s device. This use case is especially dangerous in corporate environments where just one infected endpoint could infect an entire network.
Since the launch of these new TLDs, there have been debates in the IT community about the severity of the issue. Google has responded to the matter, citing that the risk of confusion between domain names and file names is an existing challenge and can be mitigated through browser security measures. Security practitioners fall back on the suggestion to check links before clicking, access links through trusted sites only, and to be wary of files from untrusted sources.
from SentinelOne https://bit.ly/3BHc3KW
via IFTTT


No comments:
Post a Comment