The Good | Lapsus$ Teen Members Found Responsible for High-Profile Cyber Crime Spree
This week, a London jury found 18 year-old Arion Kurtaj of Oxford, UK to be responsible for a series of cyberattacks against major firms, including Uber, Nvidia, and Rockstar Games. Additional charges include computer intrusion, fraud, and the demand for millions of US dollars in ransom backed by the threat of leaking sensitive information.
Kurtaj holds several online aliases, including teapotuberhacker, White, and Breachbase and is estimated to have made over 300 BTC from various illicit activities. Much of these ill-gotten profits, however, were reportedly lost to rival hackers and gambling. Alongside Kurtaj, a second teenager has been convicted for their association with Lapsus$ and breaching several companies.

Described by the court as a loose and unorganized collective of young “digital bandits”, Lapsus$ is thought to have members operating within the UK and possibly Brazil. Over the years, the group has targeted multiple high-profile organizations such as Microsoft, Okta, Cisco, T-Mobile, and Samsung. Since their emergence in December of 2021, members have been observed attacking government, technology, telecom, media, retail, and healthcare sectors for both notoriety and financial gain.
According to reports, Kurtaj and the unnamed 17 year-old first met online and committed cyber trespassing, sneaking into cellphone network operator servers. This soon escalated to ransoms and the use of swiped data to break into several cryptocurrency wallets. Prosecutors have noted the groups’ juvenile desire to defy and taunt victims, often leaving offensive messages after infiltrating systems. Kurtaj, who is autistic and deemed not fit to stand trial, did not appear in court to give evidence. Jurors were asked to determine whether the teen committed the alleged acts rather than to determine if he did so with criminal intent. These cases have simultaneously highlighted the vulnerability of teenage hackers and the need to enhance cyber defenses across the web.
The Bad | macOS Malware “XLoader” Returns Disguised As Productivity App
A new variant of the macOS malware known as “XLoader” has been discovered, now masquerading as an office productivity app called “OfficeNote”. In findings published this week, SentinelOne found that this version of XLoader is hidden within an Apple disk image named OfficeNote.dmg and signed with the developer signature “MAIT JAKHU (54YDV8NU9C).” Initially identified in 2020, XLoader functions as an information stealer and keylogger, operating under the Malware-as-a-Service (MaaS) model and succeeding the infamous Formbook malware.
XLoader was first seen targeting macOS in 2021, when it was distributed by attackers as a Java program. The new XLoader variant uses the C and Objective C programming languages to avoid the limitations caused by the requirement for Java Runtime Environment, which isn’t installed by default on Mac devices. SentinelOne noted several instances of this artifact on VirusTotal throughout July 2023, suggesting a widespread campaign.
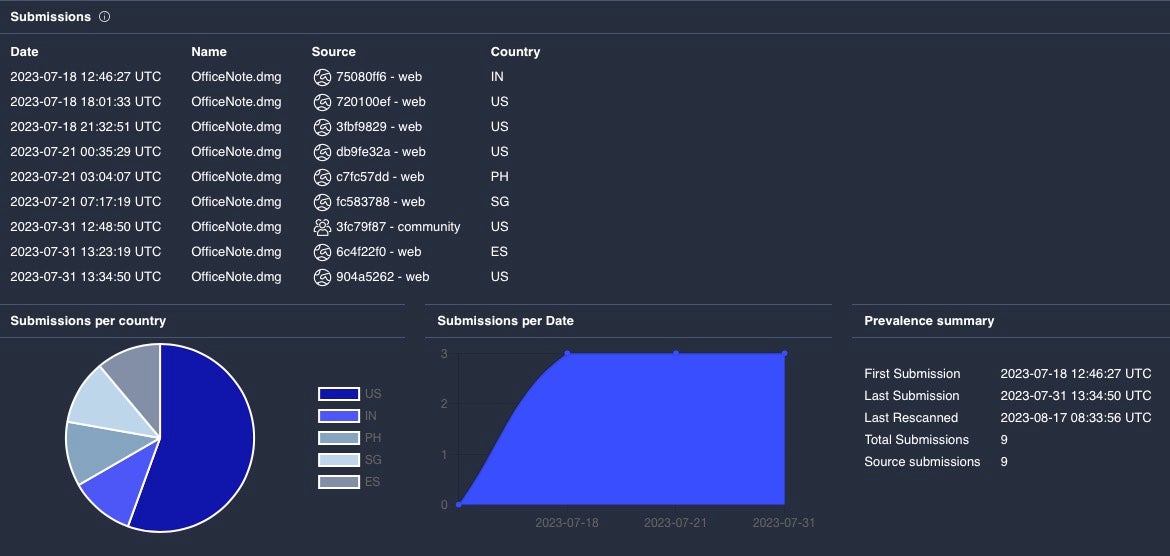
The malware pretends to be an office application named OfficeNote but in reality, installs a Launch Agent in the background for persistent execution. Once active, XLoader captures clipboard data and information stored in directories linked to popular web browsers that could be exploited or sold to other threat actors. To evade analysis, XLoader employs evasion techniques against both manual and automated analysis. It also incorporates sleep commands to delay execution in an attempt to avoid detection.
SentinelOne concluded that XLoader remains a threat to macOS users and businesses, emphasizing the need for continued vigilance against such cyber threats. Customers of SentinelOne are automatically protected from this new variant of XLoader.
The Ugly | US & UK Critical Infrastructure Targeted By Lazarus Group’s New RAT
DPRK-backed Lazarus Group has exploited a patched critical security vulnerability in Zoho ManageEngine ServiceDesk Plus with the purpose of distributing a remote access trojan (RAT) named QuiteRAT. The targets of these attacks include internet backbone infrastructure and healthcare organizations in Europe and the US, according to reports by security researchers this week. Additionally, in-depth analysis of the group’s attack infrastructure uncovered a new threat called CollectionRAT.
QuiteRAT, a successor to MagicRAT and TigerRAT, exhibits similar capabilities but with a significantly smaller file size. The malware is built on the Qt framework, which adds complexity to its code and makes analysis more challenging for cyber defenders. The attacks, observed in early 2023, involved exploiting CVE-2022-47966, a vulnerability that emerged just five days before the first attack in a proof-of-concept (PoC) to deploy QuiteRAT from a malicious URL. Unlike MagicRAT, QuiteRAT lacks a built-in persistence mechanism and requires the server to issue commands for ongoing activity on compromised hosts.
The Lazarus Group is also observed incorporating open-source tools and frameworks for initial access in their attacks as opposed to using them solely post-compromise. The reports indicate the use of the open-source DeimosC2 framework and CollectionRAT for various malicious activities, such as gathering metadata, executing commands, managing files, and delivering payloads.
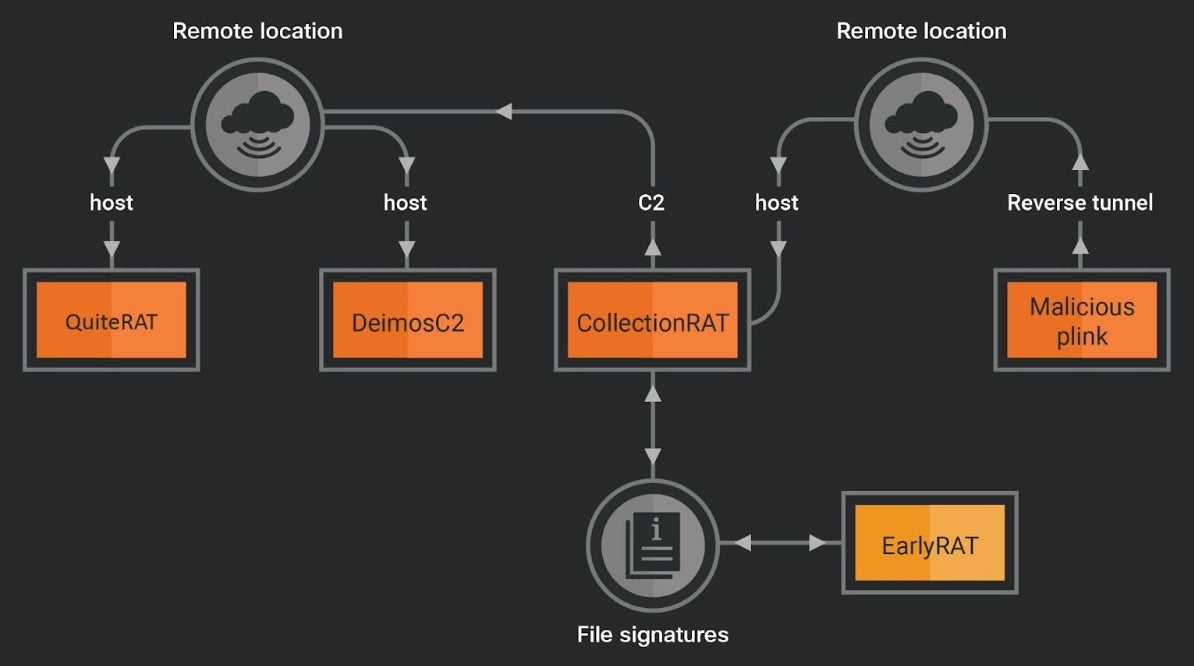
Despite the well-documented nature of Lazarus’s tactics, researchers noted that the groups’ continued use of the same infrastructure shows the threat actor has confidence in the continued success of their operations.
from SentinelOne https://bit.ly/3PdbwYP
via IFTTT
No comments:
Post a Comment