As part of the Subscription Services team, the consultants delivering the Analytic Co-Pilot Service, have come together to share Q3 2023 security use cases we have worked on in our own internal environments, as well as with LogRhythm customers. We strive to continue to grow the library of use cases that strengthen our arsenal to help secure our customers.
This quarter, we’ve revisited several out-of-the-box rules to keep up with new techniques and trends. Plus, recent cybersecurity incidents have sparked change in the way we approach administrative controls and how we can help customers monitor and investigate administrative breaches, in addition to technical attacks.
Let’s dive into a recap of Q3 2023 security use cases that our team worked on.
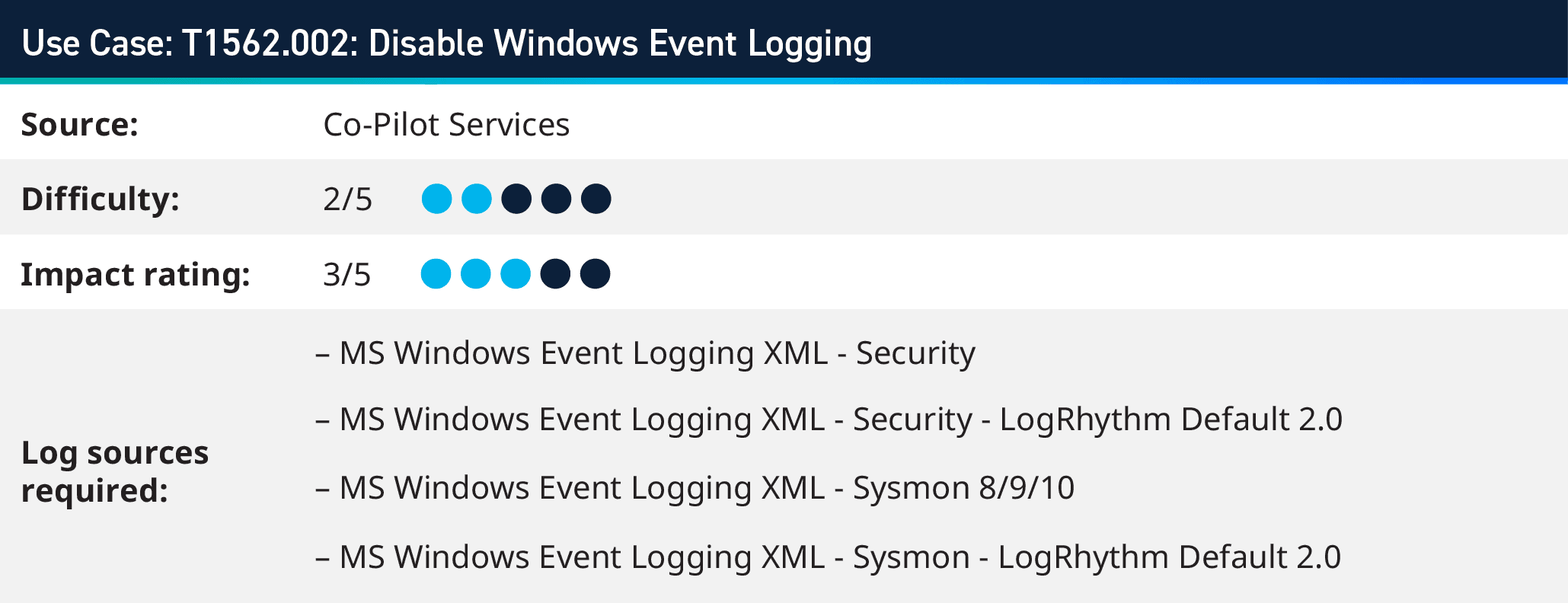
1. Monitoring for Disable Windows Event Logging (T1562.002)
Adversaries may strategically attempt to deactivate Windows event logging to minimize traceable data that could lead to their detection and subsequent auditing. This deactivation could be applied across the entire system or targeted at specific applications. The techniques they might employ include:
- Using specific commands to halt the EventLog service
- Altering registry keys to render the service inactive
- Leveraging the auditpol tool to disable auditing or entirely clearing the audit policy
These maneuvers enable adversaries to operate under the radar, leaving minimal evidence of their intrusive activities. As such, defenders must monitor these potential activities and implement robust security measures to thwart unauthorized alterations to event logging.
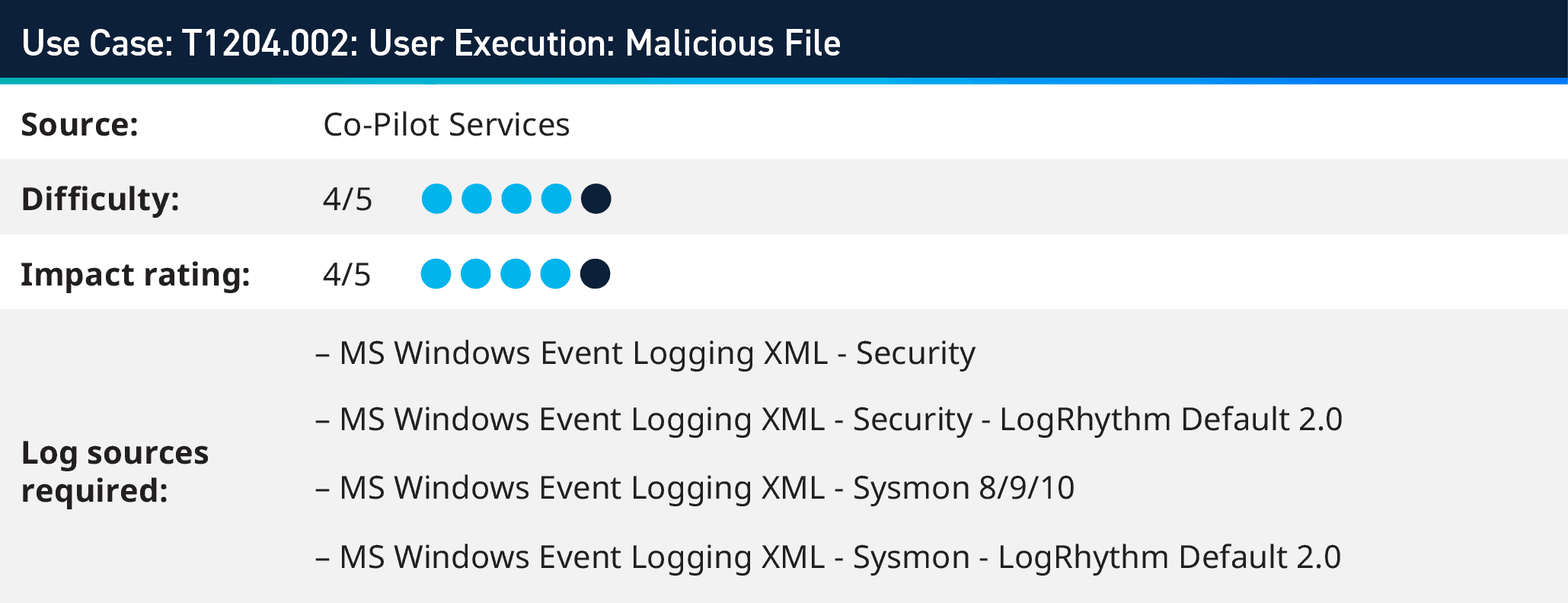
2. User Execution: Malicious File (T1204.002)
As the attacker completes the Initial Access phase of the attack through techniques such as spearphishing or internal phishing, the attachment files used can be of various types, with the most popular being PDF, XLS, INK, EXE, or Doc, and others. To entice the user to open the file, adversaries might use masquerading, obfuscation, or other deceptive tactics.
The goal is to gain access to the target machine by executing malicious code. The process could result from a targeted social engineering tactic, so the probability of the user opening the file and allowing the code to run increases. Other methods could also involve encrypting the file with a password and sending the details of that password in a separate email or using similar naming conventions for the file name.
More often, the frequency of these attacks is carried out shortly after the initial access phase; however, attackers can also drop these types of files in a shared directory on a user’s desktop, hoping they inadvertently click and open the file.

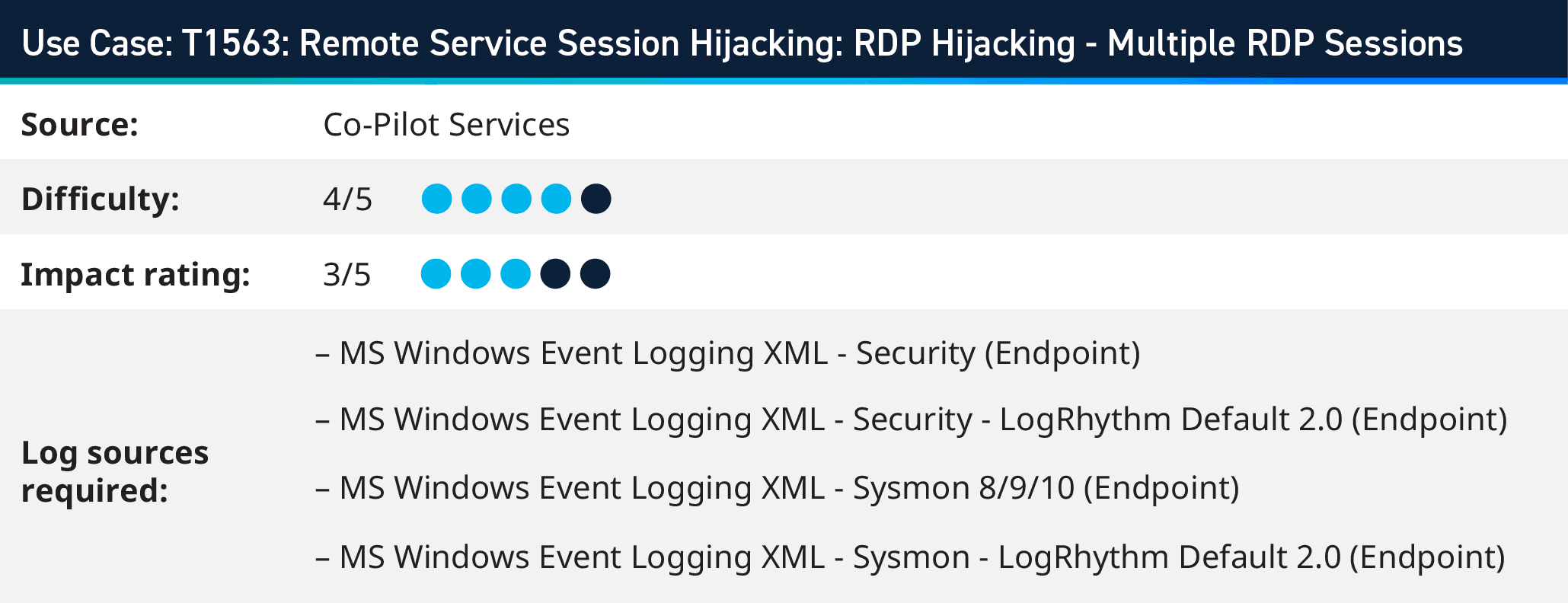
3. Detecting Remote Service Session Hijacking (T1563)
Enabling multiple Remote Desktop Protocol (RDP) sessions on a single machine is advantageous for attackers as it grants them persistence, lateral movement, and potential privilege escalation within a compromised network. Attackers achieve this by modifying the Windows Registry settings related to Terminal Services, explicitly turning off the single session per user limit. The adversary can establish and maintain multiple RDP sessions on the compromised machine.
Defenders must monitor RDP usage, implement proper access controls, and regularly assess the security of their systems to detect and mitigate such attacks.

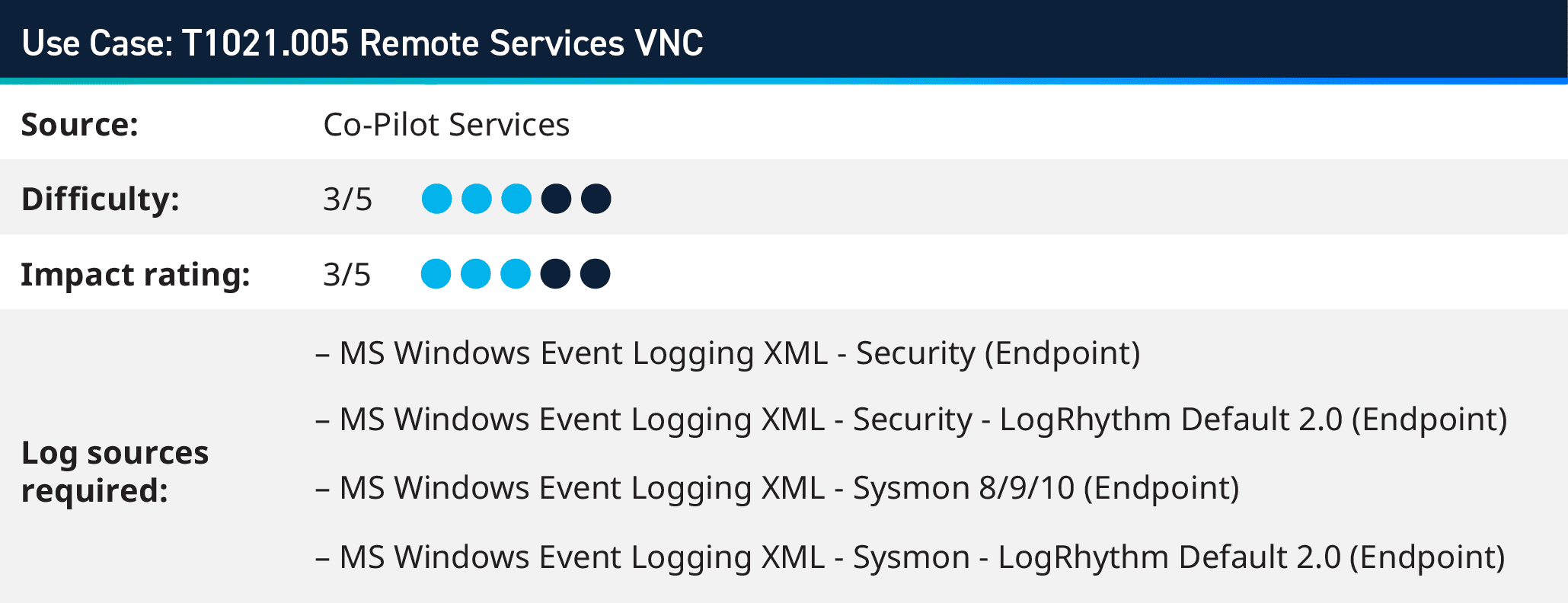
4. Monitoring Remote Services VNC (T1021.005)
Shuckworm also recognized as Gamaredon, is an espionage collective that has been operational since 2013 and is suspected of being backed by the Russian government. While Virtual Network Computing (VNC) is primarily known for its legitimate remote desktop-sharing capabilities, Shuckworm has repurposed it for their malicious activities.
Shuckworm deploys a specialized VNC module in its campaigns, allowing it to sustain its presence on infiltrated systems and facilitate data exfiltration. The delivered payload module creates a reverse connection to the attacker’s infrastructure, granting them unrestrained control over the victim system. Shuckworm’s adept use of VNC underscores the group’s adaptability and proficiency in manipulating standard tools for malicious ends.

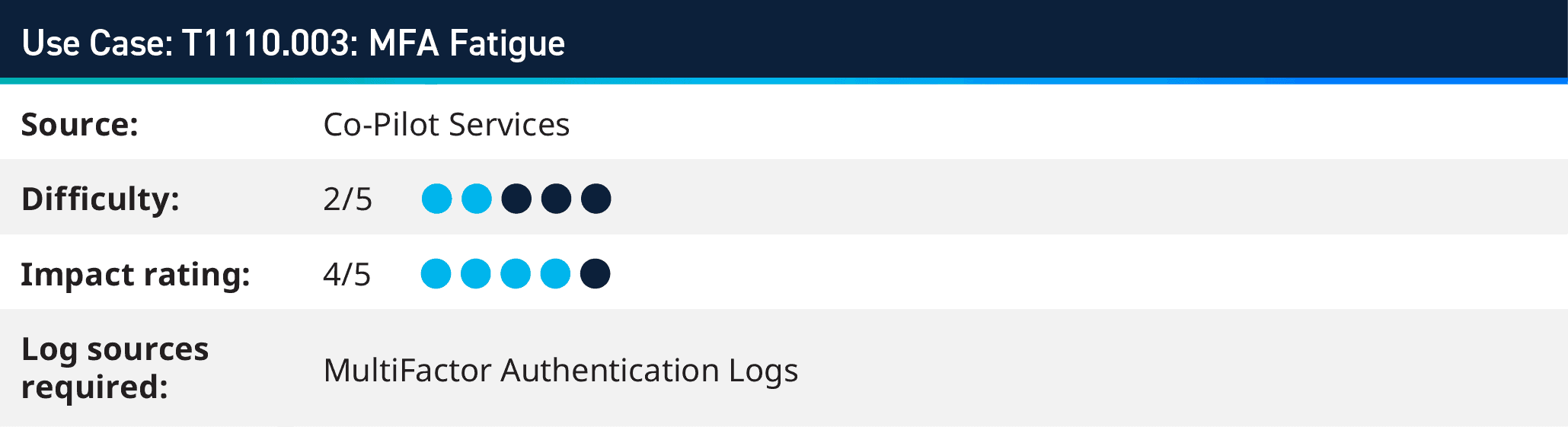
5. Detecting MFA Fatigue (T1110.003)
Multi-factor authentication (MFA) fatigue refers to the frustration or weariness that individuals may experience when repeatedly using MFA to access various online accounts or systems. MFA is a cybersecurity mechanism that requires users to provide two or more separate authentication factors (typically something they know, something they have, or something they are) to verify their identity and gain access to a system or application. While MFA significantly enhances security by adding an extra layer of protection, but hackers can leverage tactics like sending multiple MFA push notifications to a user, until they experience fatigue and accept the request for access.
To help with anomaly detection, LogRhythm developed a detection rule that looks for multiple failed MFA activity from a single user and then followed by a successful MFA attempt from the same host origin. The scenario signals that there were multiple attempts to authenticate and the user either rejected or did not respond to those challenges and then simply accepted the last one. One case of false positives might be the user couldn’t locate the MFA device to respond to those challenges and then was able to, those cases can then be dismissed as false positives, but they are still worthy of an investigation.
If you’re interested in learning more about how LogRhythm helps customers detect and response to MFA fatigue and phishing attacks, check out our SIEM demo here that explores the use case in detail.
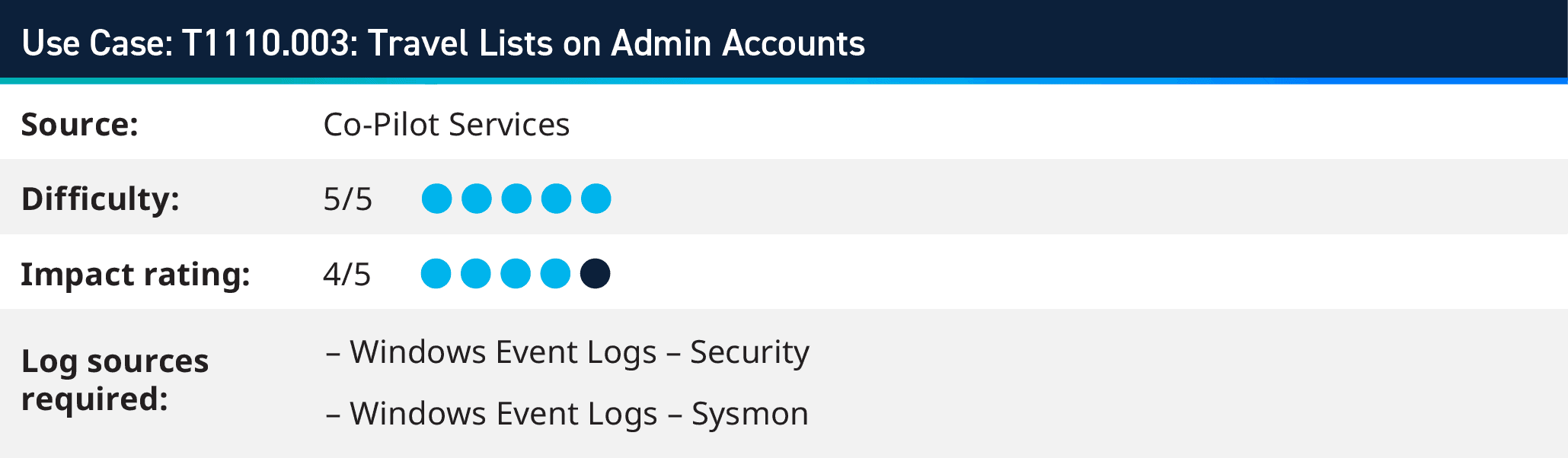
6. Travel Lists on Admin Accounts (T1110.003)
The latest ALPHV/BlackCat group attack on several Las Vegas casinos signals the need for monitoring out of office employee logins. The threat group took advantage of an out of office admin and gained control of their account deploying ransomware of key servers within the environment.
Travel lists if maintained for critical employees can be leveraged to compare against current logins within the environment, and thus this scenario can be alarmed on for proper investigation.
Where to Find Out More?
Four customers with the Analytic Co-Pilot, Support Account Manager or Technical Account Manager services, these use cases (and many others) are available to download immediately within our Subscription Services Group Hub on the LogRhythm Community.
Understanding that these use cases can be valuable, we do then share these to the wider Community after some time. To glimpse over other use cases our Co-Pilot team has worked on in previous quarters, visit the following blogs below:
2022 Cybersecurity Use Cases
- Q2 2022 Analytic Co-Pilot security Use Cases
- Q3 2022 Analytic Co-Pilot Security Use Cases
- Q4 2022 Analytic Co-Pilot Security Use Cases
2023 Cybersecurity Use Cases
To learn more about our Analytic Co-Pilot Services and how we can improve your threat detection and response, visit here. If you are a customer and you have questions, reach out to your customer success manager or account team to get more information about how we can help with your use cases and analytics!
The post Q3 2023 Analytic Co-Pilot Use Cases appeared first on LogRhythm.
from LogRhythm https://bit.ly/45ej9CZ
via IFTTT
No comments:
Post a Comment