Implementing the CTI Process Lifecycle as a Hyperloop
The Intelligence Hyperloop is an implementation model for the Cyber Threat Intelligence (CTI) Process Lifecycle. The lifecycle is a well-established process describing how intelligence products are driven by planning & direction initially, followed by collection, processing, analysis, production, and dissemination phases. The cyclical nature describes how disseminated products then inform a new planning & direction step of a new cycle.
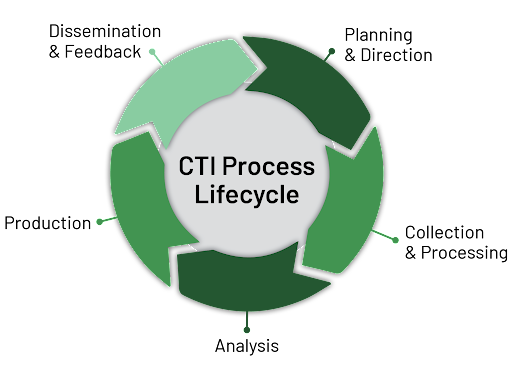
The CTI Process Lifecycle (Figure 1) can be leveraged on a tactical level, where an analyst is given a task (planning & direction) and works their way through all the steps of the cycle, until they disseminate a report. It could also be used as a guide when developing and building a CTI program. Organization-level requirements for the program can inform what data, sources, tools, and training needs to be provisioned to be able to deliver against those requirements.
This blog post describes how the CTI Process Lifecycle can be practically implemented on both tactical and strategic levels, and how those levels complement each other. The CTI Process Hyperloop (Figure 2) is a visualization of that approach, and takes a step back and combines those two interpretations of the CTI Process Lifecycle. It describes how strategic level threat intelligence informs tactical and operational level threat intelligence planning & direction, and in turn, collectively informs strategic threat intelligence products.
Before a process can be defined, the mission and purpose of the CTI program needs to be defined. This blog post describes how organizations can take a requirements-driven approach to do so. After a mission is defined, the CTI Process Hyperloop can be leveraged to describe how strategic threat intelligence drives and directs the focus of multiple tactical CTI processes, which, in turn, inform strategic insights and analysis. This strategic insight enables the reporting on threat trends for executive management, which informs the decision making for prioritization and focus of the next tactical cycles.
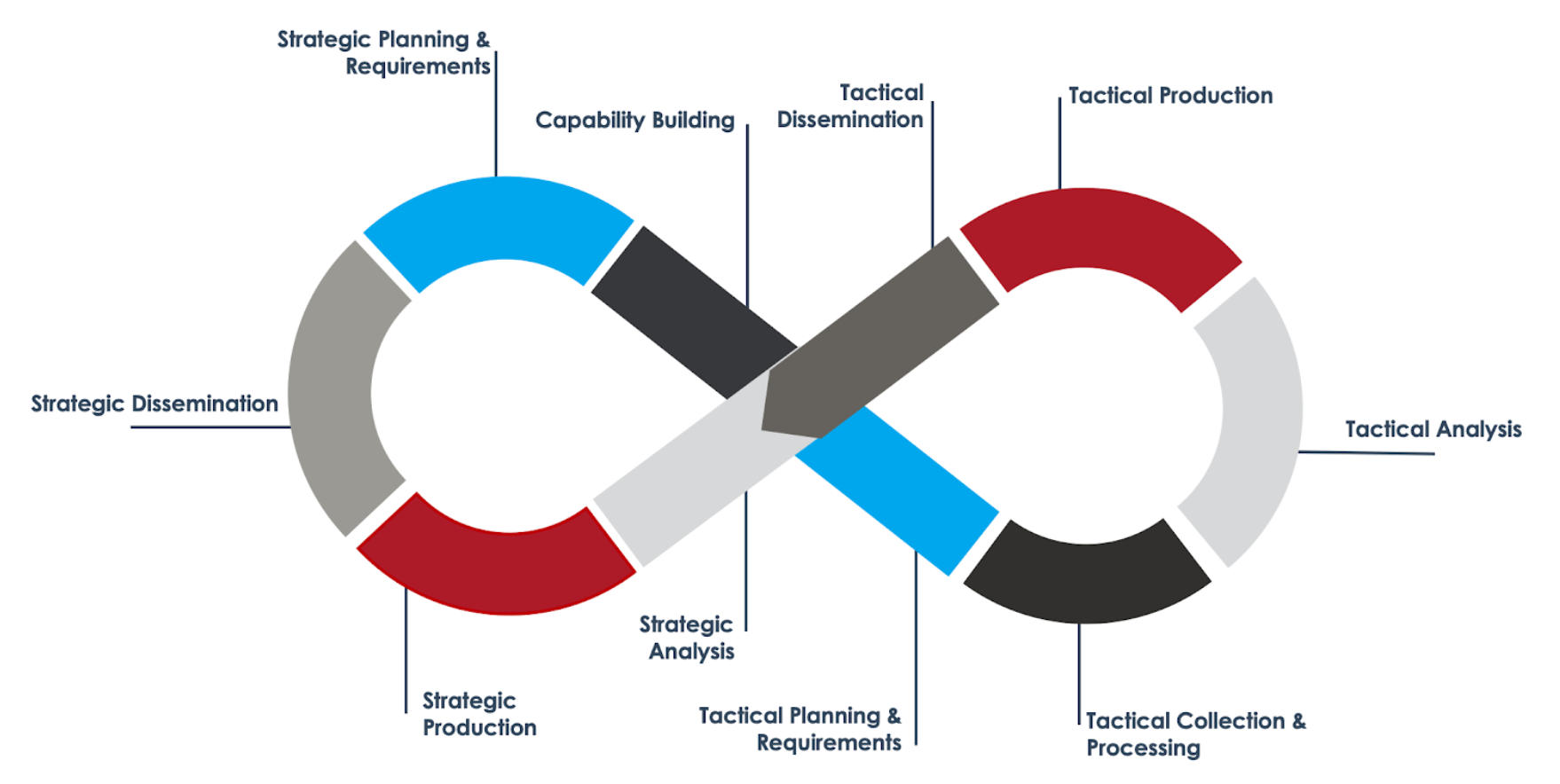
The strategic steps of the hyperloop help decision makers allocate resources in an informed and defensible manner. CISO’s leverage the outcome of these stages to justify their focus on budget, people, process, and technology. Strategic level guidance can be leveraged to inform a wide variety of tactical (and operational) lifecycles. As an example, a strategic insight into the top threat actors to an organization can inform quarterly prioritization of threat actor tracking at the tactical level. The outcome of those tactical cycles can support several use cases, such as the development of hunt playbooks, monitoring & detection, and incident response support (both proactive and reactive). This would enable tactical CTI analysts to prioritize collection of certain malware types and families, which will result in a more readily available support package during incident remediation efforts. Finally, the outcome and data of those efforts can be collected, grouped, and analyzed on a strategic level, and, along with an updated understanding of the evolving threat landscape, inform a next cycle of strategic prioritization and focus.
Having a well-defined process framework ensures structured and repeatable collection, analysis, production, and dissemination of threat intelligence. Establishing the expected resulting capabilities ensures that end-state business objectives, goals, and outcomes are clearly identified and agreed upon. It is important to define processes and related capabilities that are repeatable, aligned to business needs, and ultimately reduce risk and exposure to threats.
In the following sections of this report, each CTI process phase is examined in more detail. Note that whilst the transition from the strategic to tactical cycles is not a fixed sequential process, phases have been arranged to reflect the natural transition between them.
The Planning & Design Phases of the Strategic Stages
The strategic intelligence planning stages drive and direct tactical intelligence workflows, which in turn feed back into the strategic analysis and production phases. This section covers that initial strategic aspect of the lifecycle. These include strategic planning and requirements and capacity building.
Strategic Planning and Requirements
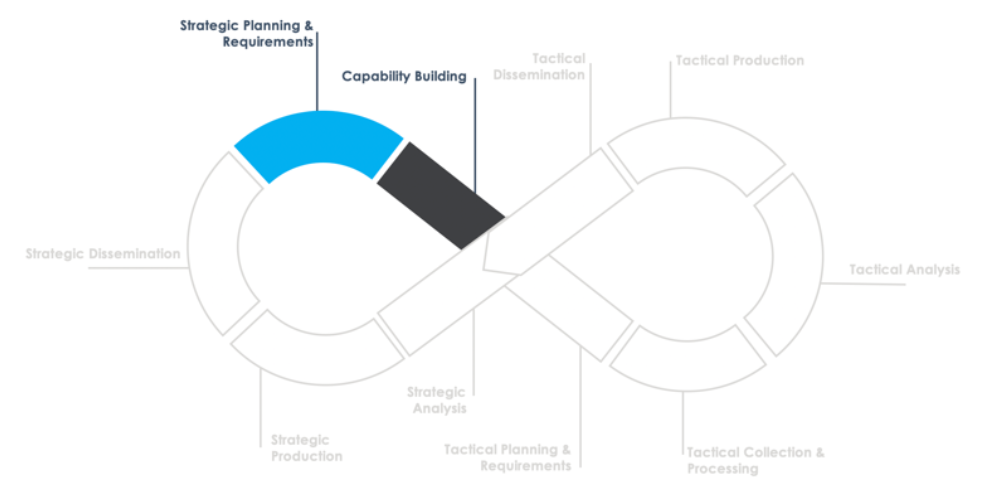
The first and most critical process component of the CTI Process Hyperloop is the identification, development, and implementation of CTI program requirements. These requirements are based on leadership directives and business needs. An important input for this phase is a Cyber Threat Profile (CTP), particularly during the first cycle, when the CTI capability is first established. In following cycles, strategic results can be leveraged to assist in updating the CTP to highlight the developments in the organization’s threat landscape.
When developing and sustaining a CTI program, it is necessary to understand how CTI products and services can or will be consumed. By exploring the needs of various stakeholder groups, the CTI Team can continuously provide relevant and actionable intelligence products. Mandiant recommends that this process be performed at a minimum annually to ensure that CTI products and services can meet the changing demands of various member groups.
As security functions within organizations evolve, both existing and newly identified stakeholders will require the creation of new (or modified) use cases for CTI. It will be up to the CTI team to determine if these may be absorbed into existing CTI service lines or require development of an entirely new one.
Following stakeholder analysis, relevant use cases can be identified. This is the fundamental input for the development of intelligence requirements. This ensures that intelligence requirements trace back to a specific business or operational need that is related to protecting the organization from threats.
Capability Building
While traditionally not a standard step in any CTI Process Lifecycle, capability building allows for the procurement and development of data sources and tools, hiring of relevant skills, as well as training required to support that process. This stage also encompasses integration with tools, systems, and data of other teams inside the organization or community of interest.
Decisions need to be made on the required data, skills, technology, and procedures to deliver on the identified CTI service lines. All the tactical cycles that will be running in parallel will be identified, and per cycle, data types and sources are identified, along with the tools and skills required to access, store, and analyze them. Care should be taken that the processing will also support later strategic analysis of the same data and the resulting intelligence products.
The CTI team is responsible for defining requirements for the collection and processing of data, information, and raw intelligence from both internal and external sources. Requirements will focus on collection methods or mechanisms (manual and automated), source identification, data format standardization, technology dependencies, collection frequency, and input validation. The expected result is that sources and methods for CTI collection are defined, and the process enables efficient consumption and normalization from multiple sources. Data can be technical or non-technical in nature, and structured or unstructured.
Tactical Intelligence Phases
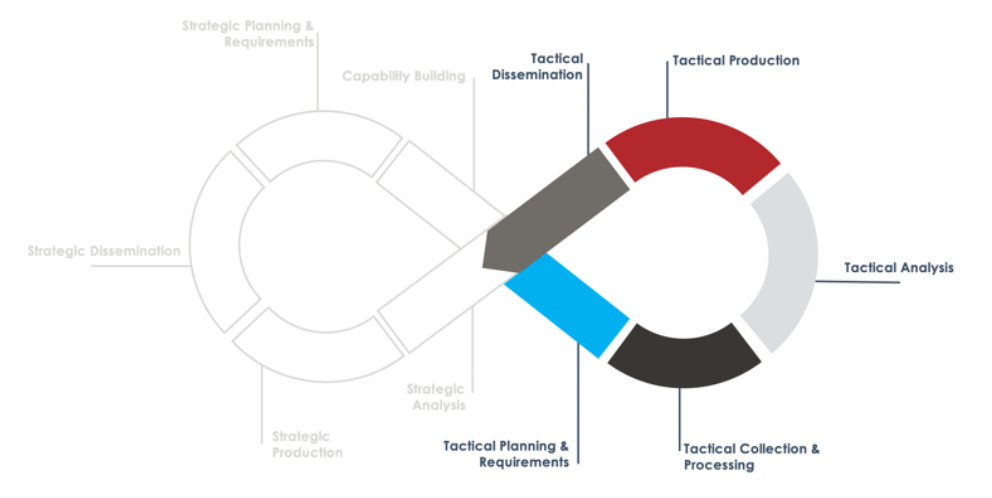
This section covers the “traditional” tactical stages of the original CTI Process Lifecycle. They are informed by the aforementioned strategic intelligence steps, and feed back into strategic intelligence analysis after dissemination. Several tactical cycles can run in parallel, depending on identified prioritized workflows during the strategic phase. For example: "IOC management" could be a tactical workflow, where IOCs based on prioritized threats are curated and fed into the SIEM. "Vulnerability Intelligence" could be another one, where vulnerabilities exploited by top threat actors are prioritized for patching and mitigation.
Tactical Planning and Direction
The completion of strategic planning and capacity building enables several parallel tactical workflows to start. These will all need their own planning and direction. For example, if a strategic requirement informs a tactical cycle focused on threat actor tracking, this stage will require planning on how to go about researching the specific threat actors identified, what stakeholders will require, what type of reporting and engagement, and how to synchronize analysis across parallel cycles.
Collection and Processing
On a strategic level, the right data and sources should have been identified and made accessible for the analyst. During this stage, CTI analysts execute the collection of the required data in preparation for analysis.
Tactical Analysis
Before tactical analysis takes place, the analyst should have been trained (if required) in using the tools, data, and systems required to execute the tactical-level analysis. Those requirements were identified during the strategic collection phase. During this analysis stage, those skills and tools are leveraged.
Tactical Production
Depending on the use case and service line associated with the tactical cycle, several varying products at varying intervals will be produced during this phase. This may include products such as a threat actor or malware or campaign profile, a geographic threat analysis, hunt playbooks, threat models for crown jewel systems and data, or threat alerts.
Tactical Dissemination
The products are then disseminated and tracked, as per agreed interval and format, to the relevant stakeholders. Note that feedback is not part of this step on a tactical level because it will be a formalized part of the strategic cycle later. Dissemination can become complex, with many of the same types of products or content going to multiple stakeholders who may need to consume the intelligence in different ways.
Consolidating Strategic Phases
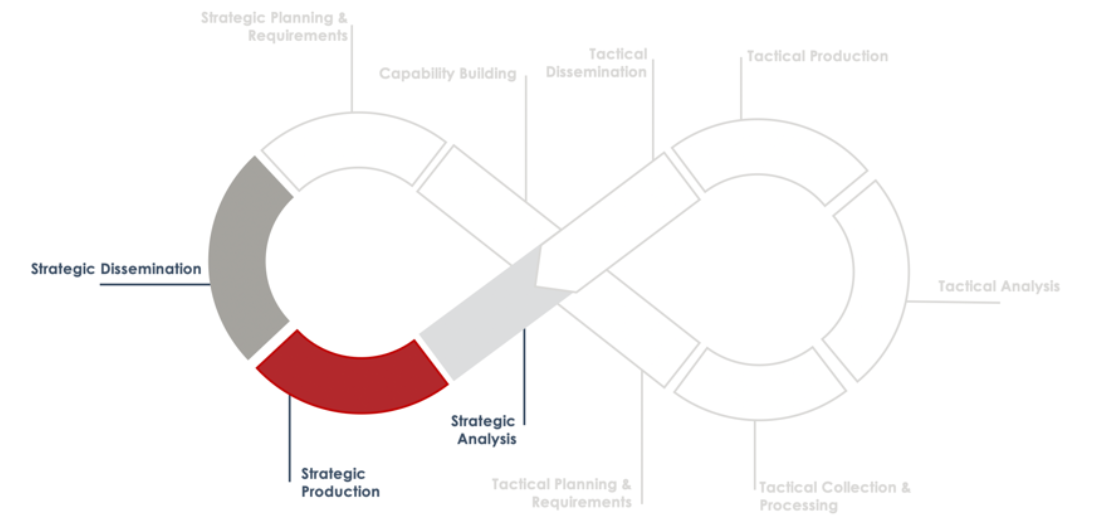
Tactical intelligence workflows, as discussed, inform strategic analysis processes. This section covers these strategic phases and illustrates how they inform new prioritization and intelligence requirements.
Strategic Analysis
The primary goal of this phase is to provide sound analytic judgments that enable adaptation to the evolving threat landscape. Processed information from the tactical cycles, augmented with any required additional sources, is analyzed to produce the required strategic intelligence products. These typically include Threat Trending reporting and updates on the threat landscape. The tactical workstreams continuously feed into this process, which results in a near real-time understanding of the prioritized threats, how the other security teams are managing them, and to what extent they are effective.
Analysts operating at this level require a combination of skills that is difficult to find in any one person, including a wide range of technical skills to understand the threats, and data analytics skills to aid the processing and analysis of large datasets. Strong C-level communication skills are also required during the later stages of the cycle.
Strategic Production
Strategic production centers on the creation of non-technical finished intelligence products that are timely, relevant, and actionable. These products must always trace back to their relevant use cases and service lines, and they may take many different forms. Different products will have multiple purposes, audiences, and intended courses of action for stakeholders. While tactical and operational reports typically hold little to no value to strategic-level stakeholders (a CISO is not enabled by an indicator feed), the opposite is true for strategic products and tactical stakeholders: a quarterly threat summary is of significant value to a SOC analyst, for example. Even if they aren’t able to directly action the intelligence, it will provide them with an up-to-date understanding of the current threats to the organization and allow them to contextualize the day-to-day work accordingly.
Strategic Dissemination and Feedback
The final strategic CTI Process Hyperloop phase entails the distribution of timely, finished intelligence products that are actionable by consumers and the corresponding feedback by consumers to those products. Dissemination of products should always occur in accordance with intelligence requirements, stakeholder needs, their desired frequency, and best method of delivery.
The success of the CTI program is largely measured by stakeholder satisfaction and the perception of product quality and service. Formally implementing the practice of garnering feedback through requests for clarification and requests for information ensures that the program can adapt to changing needs and identify deficiencies.
The strategic intelligence, provided to leadership as a primary stakeholder, provides insight, situational awareness, and an up-to-date understanding of the threat landscape and the organization’s ability to defend itself against priority threats. This will empower leadership as well as more operational and tactical-level stakeholders to formulate new or adjusted intelligence requirements as part of a new strategic planning & direction phase.
from All Blog Listing https://bit.ly/3ugcoDR
via IFTTT
No comments:
Post a Comment