As part of Success Services, this past quarter LogRhythm consultants have been hard at work helping customers improve their defenses against cyberthreats. This quarter, the team observed a shift in attack vectors back into Credential evasion via NTLM, DC manipulation, and the overall bypassing of normal authentication operations. Alongside phishing, authentication manipulation is still the most probable initial attack vector for elaborate exploitation.
Here is a recap of several Q4 2023 security use cases that the team worked on.
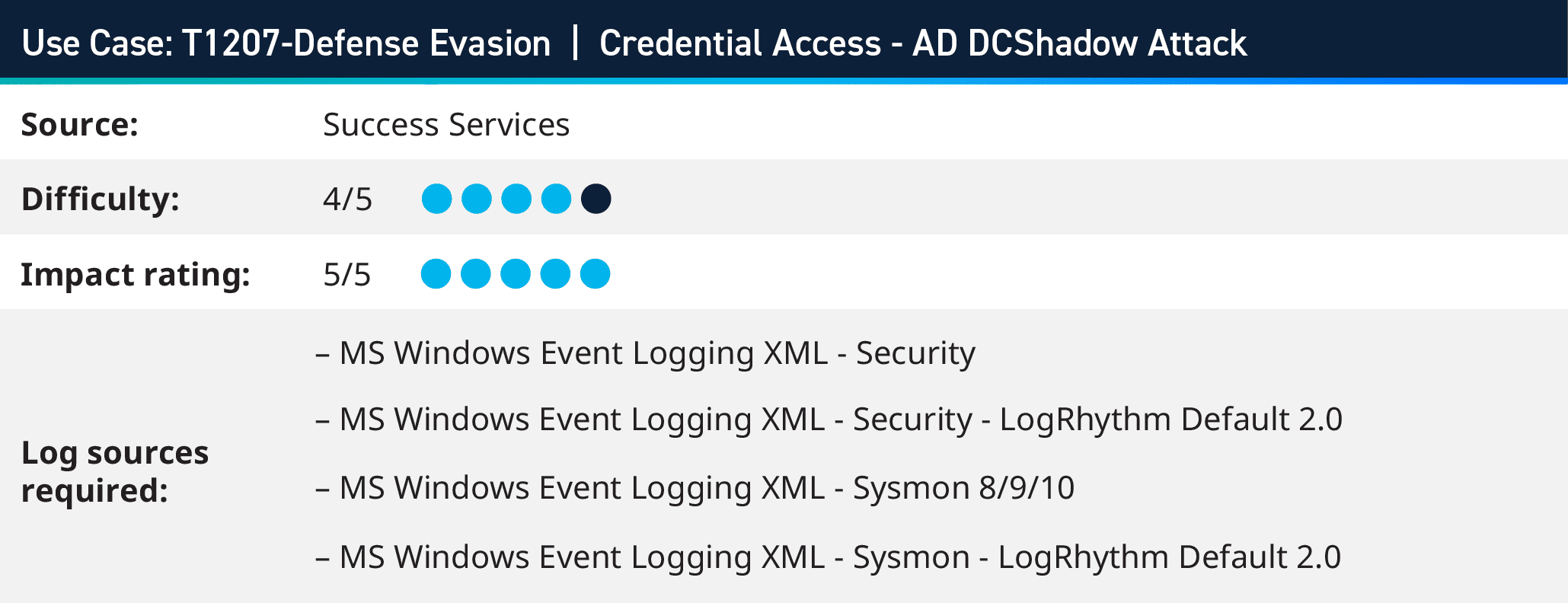
1. T1207: Defense Evasion|Credential Access – AD DCShadow Attack
Domain Domination via “DCShadow” is one of the preferred techniques used by advanced persistent threats (APTs) to inject Domain with its own data and reset Domain credentials by simulating the behavior of a Domain Controller. This can lead to Full Domain compromise for long-term persistence and privilege escalation in a single attempt.
Domain Domination evades detection and logging capabilities at most organizations if the malware execution was on mem-level or managed to evade the AV/EDR. This is because most activities are carried on the attacking machine in contradiction with DCSync variant where DC is requested for replicating Domain data.
DCShadow abuses the legal default MS-DRSR “Microsoft Directory Replication Service Remote Protocol” to push data updates like credentials or access level for Domain Account as remote DC replication. This leads to more sophisticated attack levels such as persistence, Admin Stealthy Account, and Credential Access.
Enabling “Audit AD Changes” and consuming Event IDs 5137, 5141 with Object Type = server, would allow us to monitor for any traffic that follows the DCShadow attack pattern.
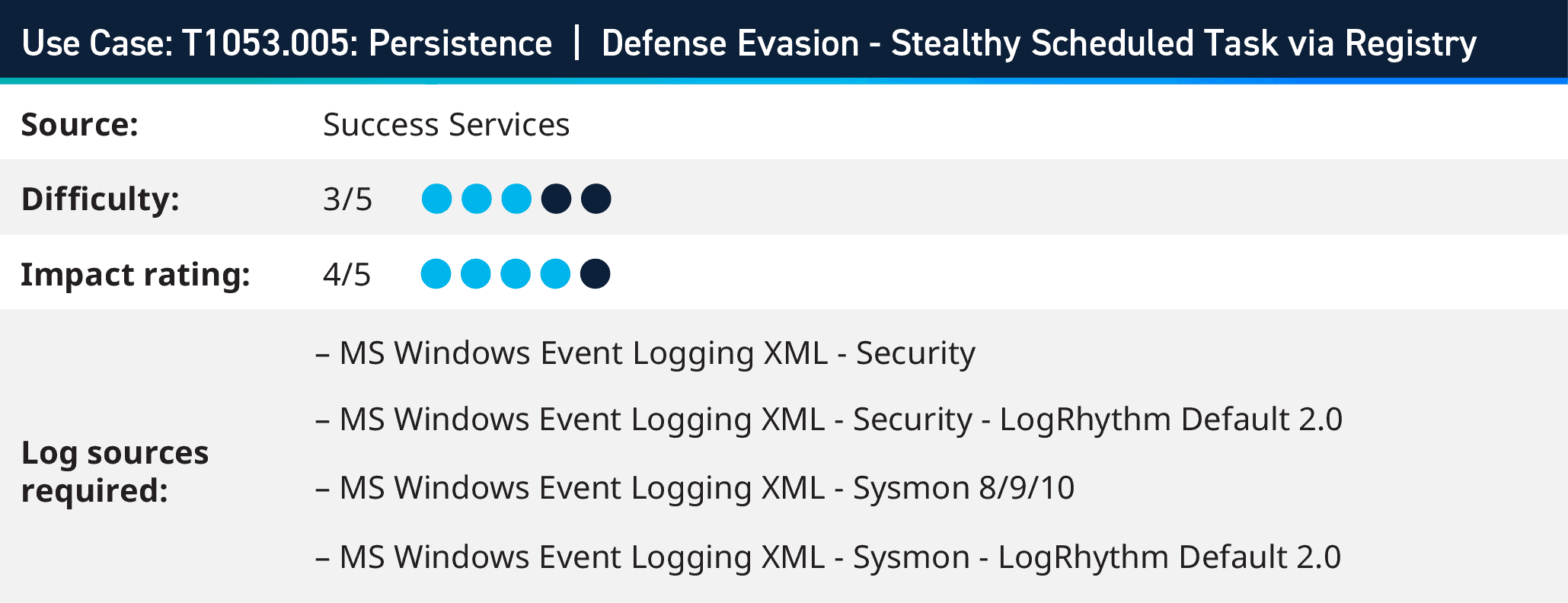
2. T1053.005: Persistence | Defense Evasion – Stealthy Scheduled Task via Registry
As part of LogRhythm’s ongoing process to enhance threat detection and expand MITRE ATT&CK® coverage, we’ve observed advanced persistent threats (APTs) employing a technique to create “hidden” scheduled tasks that remain concealed from both defender tools and analysts. This allows them to evade detection and avoid triggering any logging telemetry. They exploit the way scheduled tasks are stored in the registry to create or modify tasks without generating any telemetry, effectively bypassing common detection capabilities.
Here is an example:
HAFNIUM APT, also known as Silk Typhoon, is a state-sponsored group operating from China that has used this flaw via Tarrask malware on Windows devices to conceal their malicious activity on infected endpoints while establishing persistence.
Let’s explore briefly how Scheduled Tasks work on windows and which evidence generated behind it. When you configure a Scheduled Task normally via At.exe, Schtasks.exe, PS Register-Sch , and Task Scheduler, they usually go through RPC interface via svchost.exe and thus generating the below Event Ids that most of current detections consume:
EID 4698:4702 in MS Security Log
EID 106 in Microsoft-Windows-TaskScheduler/Operational Log
Going beyond that and abusing the following Registry entries will create/modify/hide the task without generating any of above Events.
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree
To successfully identify stealthy scheduled task we must first modify our audit policy to identify Scheduled Tasks actions by enabling logging “TaskOperational” within Microsoft-Windows-TaskScheduler/Operational. We must also Enable and centralize the following Task Scheduler logs. we can then leverage Logrhythm to monitor for those events mentioned below when they trigger. Even if the tasks are ‘hidden’, these logs track key events relating to them that could lead you to discovering a well-hidden persistence mechanism.
- Event ID 4698 within the Security.evtx log
- Microsoft-Windows-TaskScheduler/Operational.evtx log
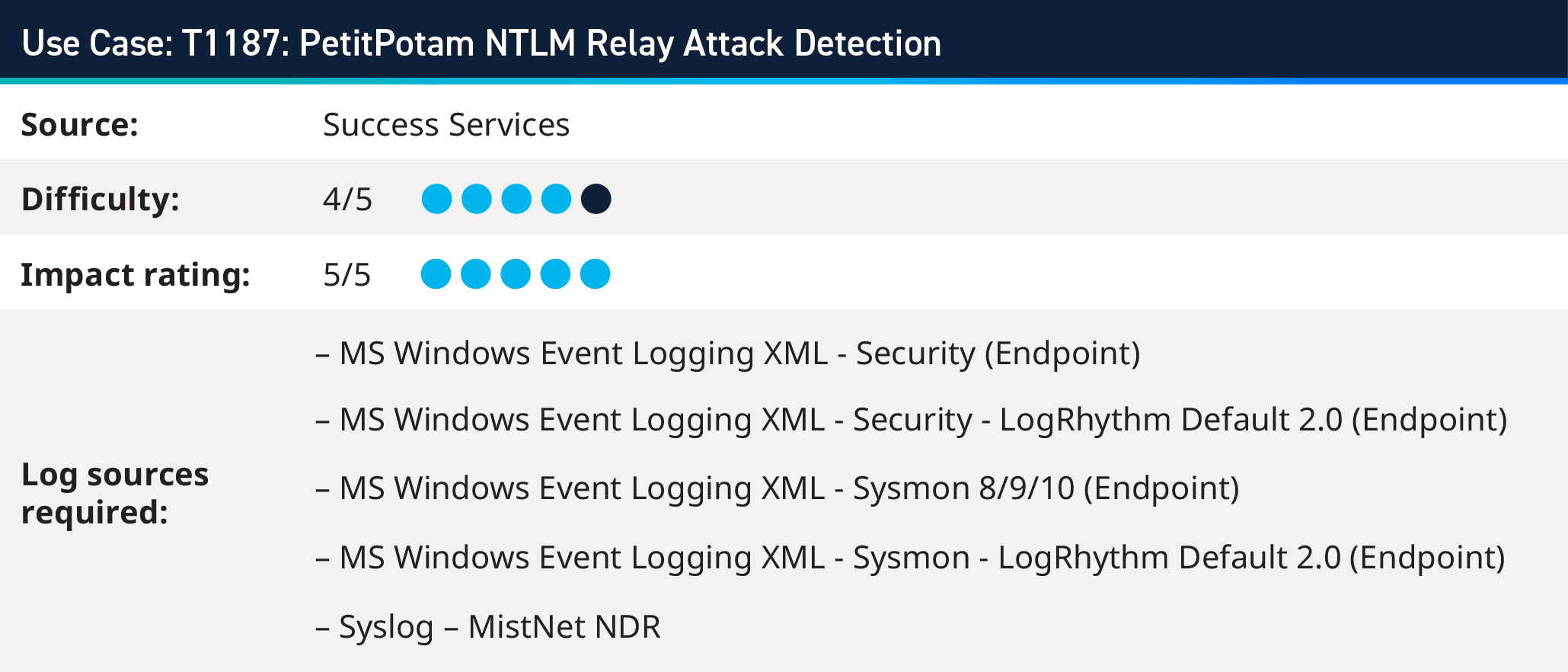
3. T1187: PetitPotam NTLM Relay Attack Detection
PetitPotam is an NTLM relay attack vulnerability affecting Windows operating systems. It leverages the EfsRpcOpenFileRaw function, which is part of the Encrypting File System Remote Protocol (MS-EFSRPC). By coercing a machine into attempting to authenticate via NTLM to an attacker-controlled server, PetitPotam can lead to relay attacks, enabling threat actors to compromise network authentication and potentially take control of domain controllers or other critical systems.
It’s critical to monitor network traffic for abnormal patterns related to NTLM authentication, such as unexpected authentication requests or repeated authentication attempts.
You should analyze network logs for inconsistencies or unauthorized attempts to establish connections.
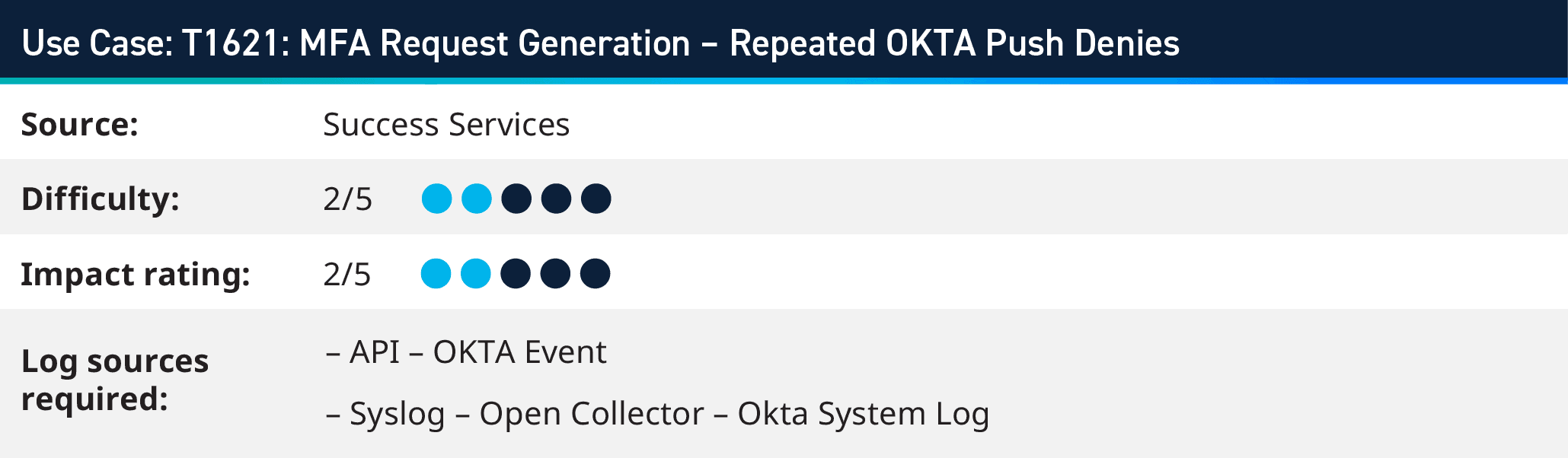
4. T1621: MFA Request Generation: Repeated OKTA Push Denies
In a typical scenario, when a user tries to authenticate, Okta sends a push notification to the user’s registered device. The user approves the authentication request via the Okta mobile app, confirming their identity. However, in this scenario, repeated denials of the push notification requests occur. This could indicate an abnormal situation:
An attacker might repeatedly deny or ignore legitimate push notifications, attempting to bypass the MFA process by preventing the user from approving the authentication requests. It could also be the result of an automated script or tool continuously denying the push notifications, attempting to prevent access or disrupt the authentication flow.
Repeated denials of Okta push notifications during MFA authentication could signal attempted bypass or manipulation of the authentication process. Implementing robust monitoring, behavioral analysis, and proactive measures can help detect and mitigate such suspicious activities, ensuring the integrity and effectiveness of the MFA system within the Okta environment.
To learn more about how LogRhythm can help defend against MFA fatigue attacks, watch this SIEM demo.
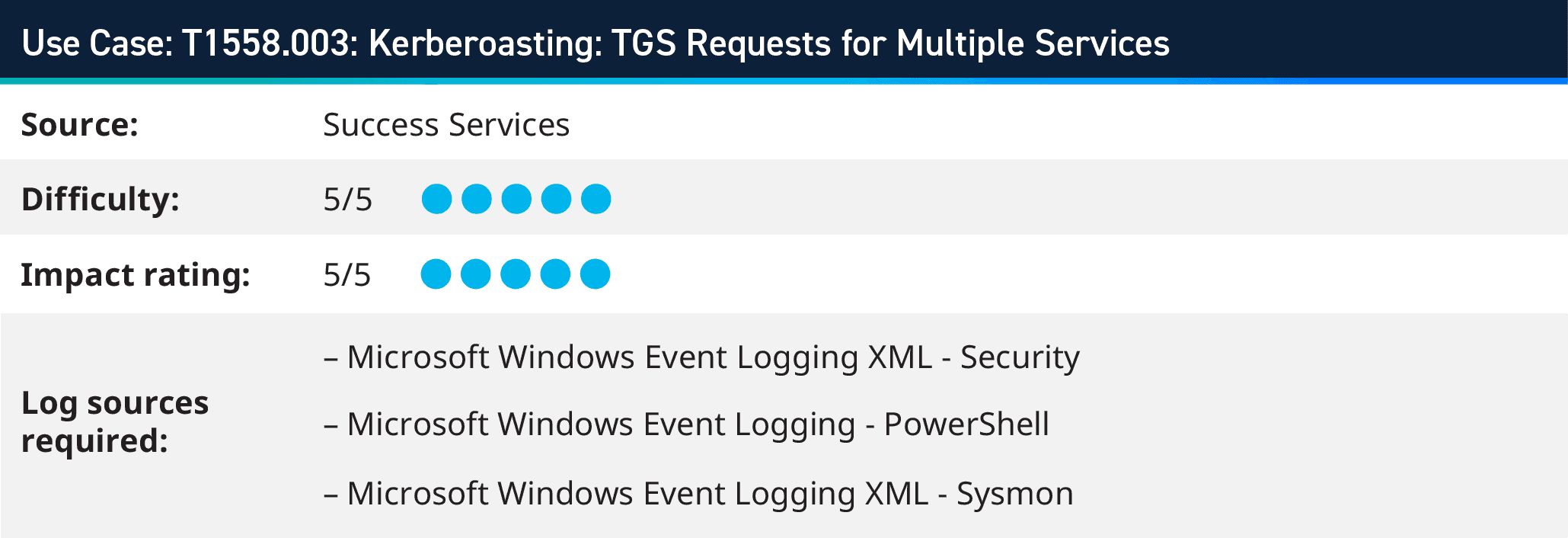
5. T1558.003: Kerberoasting: TGS Requests for Multiple Services
Kerberoasting (T1558.003) poses a significant risk to Active Directory environments by targeting service accounts and attempting to crack their passwords offline. Detecting and mitigating these attacks involves proactive monitoring, access control, and regular password rotations to minimize the impact of compromised service account credentials. Attackers enumerate Active Directory (AD) to identify accounts that have associated service principal names (SPNs). These SPNs indicate accounts eligible for Kerberoasting. Attackers request TGS tickets for these service accounts from the domain controller. TGS tickets contain encrypted data, including the service account’s hash encrypted with the account’s password.
Once obtained, attackers extract TGS tickets and save them for offline brute-force attacks. These tickets can be cracked offline using powerful computational resources to retrieve plaintext passwords. Attackers use tools like hash-cracking software to perform brute-force attacks on the extracted tickets, attempting to recover the plaintext passwords associated with the service accounts.
By monitoring event ID 4769 with multiple unique servers with the LogRhythm unique rule block we can trigger an alarm if we detect such traffic in your environment.
Where to Find Out More?
These use cases and others are available to download immediately within our Subscription Services Group Hub on the LogRhythm Community – for our customers using Success Services. Understanding that these use cases can be valuable, we do then share these to the wider Community after some time.
To glimpse over other use cases our Co-Pilot team has worked on in previous quarters, visit the following blogs below:
To learn more about our Success Services and how we can improve your threat detection and response, learn more here. If you are a customer and you have questions, reach out to your customer success manager or account team to get more information about how we can help with your use cases and analytics!
The post Q4 2023 Security Use Cases: Insights From Success Services appeared first on LogRhythm.
from LogRhythm https://bit.ly/48GUKbe
via IFTTT
No comments:
Post a Comment