In 2024, artificial intelligence (AI) has prompted 65% of organizations to evolve their security strategies. Across the globe, this technological revolution has pushed security and business leaders to think critically about how to apply AI as a force multiplier to streamline security operations and instill competitive advantages.
If executed correctly, the promise of AI holds much potential for security operation centers (SOCs) to enhance threat detection and incident response, incorporate predicative capabilities, and improve overall efficiency and scalability of security measures against cyberattacks.
That said, SOC teams must proceed with caution and cannot lose sight of what matters the most to enable an AI-driven SOC. At the foundation of all AI tools and processes is the output of data — and without a doubt — the quality and integrity of your data will reflect the success of your AI program.
In this blog, I’ll dive into some challenges that poor data quality presents for AI models and reveal the honest conversations LogRhythm is having with customers and prospects about the matter. If you want to enable your SOC to be AI ready, then you must ensure you are checking these items off your list.
The Challenge of Poor Data Quality for AI
The rapid advancement of AI and machine learning (ML) in cybersecurity demands data of unparalleled quality. AI models operate at the potential of the data it receives. Today, too many cybersecurity vendors boast about leveraging AI, but overlook a critical factor: data quality.
This can lead to several challenges, including:
Challenge #1: Unclear output
Poor data input creates unclear output. When AI tools operate on substandard input, it causes cluttered or irrelevant output, taking away from true indicators and slowing down response times.
Challenge #2: More noise
Feeding AI tools corrupted data causes them to produce inaccurate results, leading to false alarms and unnecessary noise. This makes it harder for security analysts to do their job effectively and compromises the overall security of your system.
Challenge #3: Inconsistency
When speaking with prospects in the field, they’ve run into issues with using AI tools from certain cybersecurity vendors because of inconsistent data. For example, Microsoft Sentinel requires teams to use a complex query language. To appease this pain point, they added an AI feature to put natural language search in front of the query language. The issue is users obtain different results for the same natural language search. At best, they must think about prompt engineering during an incident.
This is an example of focusing on technology, but not the original problem that is causing frustration for security professionals. If the original data fed into an AI tool is inconsistent, then it will create more noise and inaccuracy, causing security teams to lack confidence and waste time trying to understand what actions to take.
Requirements for High Data Quality — What to Look For
Staying ahead of threats isn’t just about having advanced technology — it’s about having data you can trust. Ensuring that the data fed into AI tools is clean and accurate is crucial for maintaining robust and effective security measures. Here’s what you should look for when assessing security vendors handling your data:
#1 Ease of Data Ingestion and Integrations
The success of your security program depends on extensive access to logs and other security data from all your on-premises and cloud environments. It’s important to evaluate how robust and user-friendly your security tool’s data ingestion capabilities are.
This should start with the number of formal partnerships and out-of-the-box integrations the vendor has with your existing security tool. You should also ensure that the vendor supports a diverse set of data ingestion techniques, including cloud collectors, agents, and API and webhooks integrations, along with user-friendly mechanisms for creating custom data parsing policies when necessary.
Questions to ask a vendor:
- Can you quickly and consistently ingest my data sources?
- What is the full list of techniques you use to ingest customer data?
- Can you walk me though the process for creating a custom parsing rule?
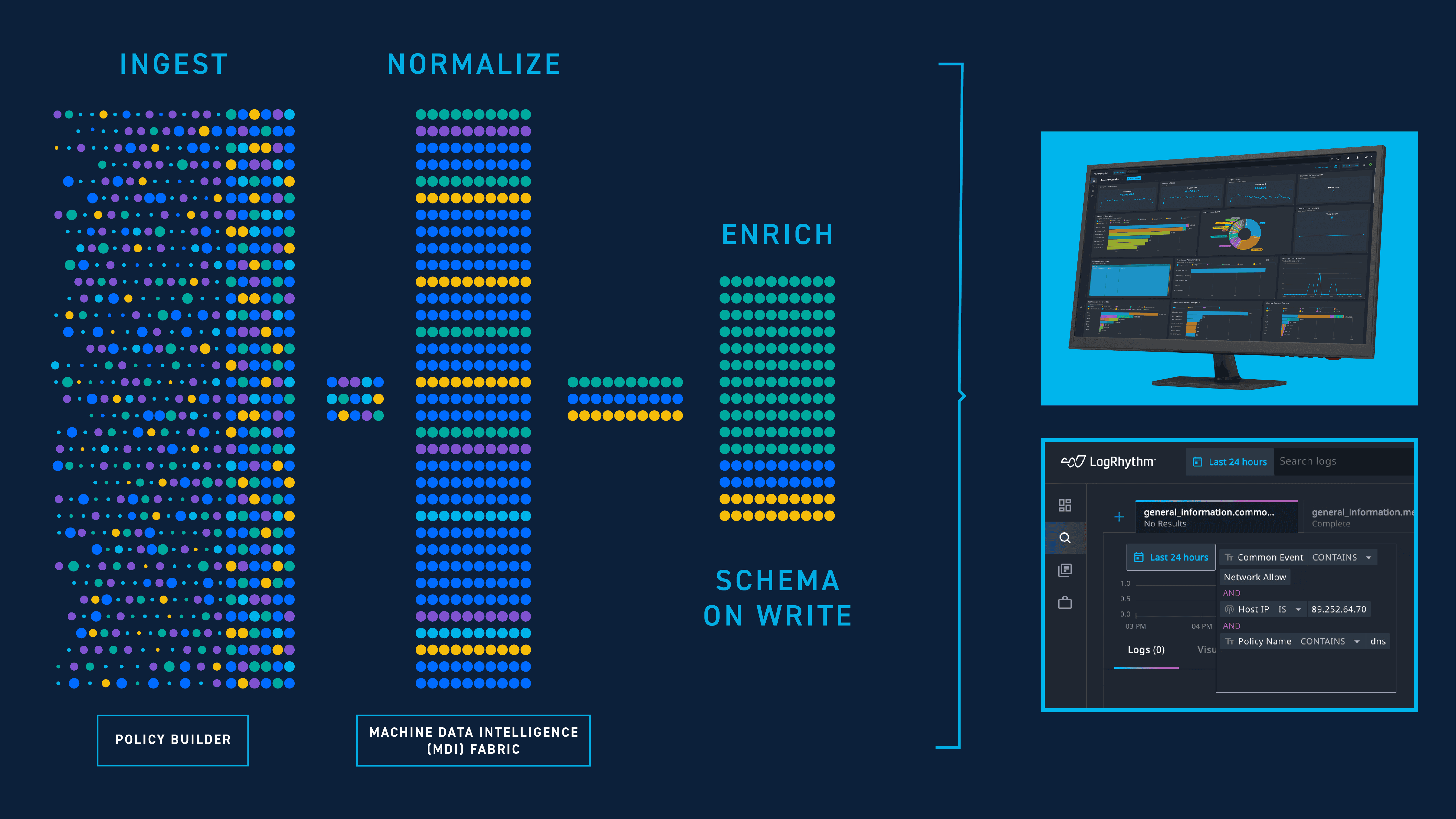
#2 Data Normalization, Enrichment, and Searchability
You need to be able to extract meaningful insights from large volumes of raw security event data. When evaluating vendors, closely scrutinize how effectively they bring varying data types into a consistent format, extract and organize meaningful metadata, and enable searchability. Both users and AI tools thrive on high-quality data. Robust normalization and enrichment capabilities empower users to conduct precise searches, while comprehensive schemas significantly enhance the performance of AI models.
Search capabilities should include support for basic search operators, as well as more sophisticated queries that include compound search operators, separators, and regular expression operators.
When evaluating search capabilities, you should also look for analyst convenience features such as assisted search wizards, saved searches, search history views, and auto-refresh capabilities.
Questions to ask a vendor:
- What types of processing do you do to raw log data that you collect?
- Can I perform complex searches on my data using compound search operations, separators, and regular expressions?
- Is the data normalized to make searching easy across various log sources?
- Is it easy to search across days, weeks, or months of logs?
- What features do you offer to guide users through complex searches?
#3 Architecture, Resilience, and Scalability
One of the biggest challenges in the security operations domain is the sheer volume of data that must be collected and analyzed continuously. It’s critical to assess your vendor’s architectural design and operational practices and ensure that they have a track record of scaling to meet the needs of organizations with similar size and characteristics as yours. This evaluation should include factors like platform uptime and performance considerations such as security event data processing throughput.
Questions to ask your vendor:
- How do you ensure that performance isn’t degraded as usage and data volumes grow?
- How do you prevent a misconfigured tenant from impacting other SaaS customers?
- What is required to scale up or down? Is there downtime required?
#4 Requirement: Data Governance and Compliance
Governance and compliance are integral to ensuring your data is of the highest quality. Effective governance includes policies for data retention, archiving, and disposal, which helps in managing data quality over its lifecycle. Governance provides the mechanisms for auditing and tracking data usage, which is vital for detecting and responding to security incidents. Your cybersecurity vendor should enable you to easily follow compliance frameworks and best practices that enforce consistency, accuracy, and reliability of data.
When leveraging AI tools, proceed with caution and ensure you have a well-defined compliance strategy. For example, if you send data to a security tool, and it subsequently forwards it to a third party for AI use cases, the data may be transferred more frequently than you’re aware of.
Questions to ask your vendor:
- Do your detection techniques map to any industry frameworks or best practices?
- How much effort will it take for me to configure your product to support my compliance needs?
- What other companies are you working with in my industry?
- How does your AI feature abide by the compliance mandates I must follow?
How LogRhythm Brings Quality to Your Data
Imagine a world where the AI tools you use to defend your company against cyberattacks are fed the cleanest, most reliable data possible. At LogRhythm, we envision a future where cybersecurity isn’t just reactive but proactively adaptive to emerging threats. We recognize that it is of the upmost importance to LogRhythm’s customers that we provide a strong base and quality in our data; this foundation is the key to a successful AI-driven SOC.
Enhancing Data with Machine Data Intelligence (MDI) Fabric
LogRhythm’s Machine Data Intelligence (MDI) Fabric makes this world a reality. For over twenty years, LogRhythm’s MDI fabric has gone through rigorous validation processes and continuous fine-tuning to guarantee the accuracy and reliability of the data ingested into our security information and event management (SIEM) solutions. It’s not just clean data, it’s battle-tested and proven.
MDI Fabric is enhanced by Apache Flink as a real-time engine for complex event processing and advanced analytics. This technology behind the threat detection engine benefits from having quality metadata the same way users and AI features do.
Equipped with this proprietary security-infused data switching technology, customers are enabled with faster and more accurate search queries and analysis.
Continually Implementing New and Enhanced Log sources
LogRhythm continually provides new and enhanced log sources to customers. By properly maintaining and normalizing log messages, customers gain maximum value from logs ingested into LogRhythm’s SIEM solutions and security insights derived from LogRhythm’s MDI Fabric.
To prove our commitment to making and keeping these promises, stay up to date with our quarterly release product communications. Our next big announcement is right around the corner! On July 1st, LogRhythm SIEM product managers will reveal 70 new log sources across operating systems, firewall security, and applications.
Delivering an AI-Driven Policy Builder
It’s critical for customers to access the highest quality metadata. Our cloud-native SIEM, LogRhythm Axon, has an AI-driven Policy Builder that leverages robust data infrastructure to construct sophisticated and customized parsing policy. This key component makes it simple to map metadata to LogRhythm Axon’s schema.
The benefit? This helps customers more easily identify any piece of data within a log and map it to the LogRhythm Axon schema — without complex query languages or programming. This is incredibility useful for security teams strapped with little resources. New users can be effective within minutes or hours because it’s easier to understand the graphic user interface (GUI).
Also, in the future, LogRhythm Axon will assess vulnerabilities and will evaluate security environments to provide customized strategies that will strengthen your defense posture, highlighted within the user interface.
Providing Faster Time to Value with Your Data
Complexity causes poor data management experiences, which can be a common pain point for security professionals. LogRhythm simplifies cybersecurity management by eliminating complex queries and jargon. LogRhythm supports searches using both structured queries and full text search to allow for maximum flexibility and ease of use when conducting investigations.
Another aspect of having high-quality data is the speed at which updates can be made to data sets. In an AI-driven world, you need to quickly adapt to changing AI models and prompts or updated parsing methods — without breaking anything. To help customers quickly adapt to change, LogRhythm has an update pattern that allows AI models to adjust quickly.
Trust Your Data and Your Security Partner
AI offers powerful tools for enhancing cybersecurity, but it also introduces new challenges that must be carefully managed. Successful integration of AI into cybersecurity teams requires balancing the benefits and challenges with strategic planning and continuous adaptation.
With LogRhythm, you can make decisions in your AI-driven SOC with confidence, knowing your insights are grounded in authentic and actionable information.
To learn more about how LogRhythm can empower your cybersecurity with trusted data, request more information today.
The post How to Ensure Your Data is Ready for an AI-Driven SOC appeared first on LogRhythm.
from LogRhythm https://ift.tt/OFhbAty
via IFTTT
No comments:
Post a Comment