In today’s digital age, cyberattacks are becoming increasingly frequent and sophisticated, posing serious threats to both digital and physical infrastructures. Incidents like Stuxnet, which targeted power plants, have demonstrated the dangerous interrelationship between cyberattacks and physical damage. As the adoption of smart city technologies accelerates, the potential for cyberattacks on critical infrastructure grows significantly.
The Rising Threat to EV Charging Stations
Electric Vehicle (EV) Charging Stations are a critical component of smart city infrastructure and are becoming common in major cities worldwide. These stations, essential for the proliferation of electric vehicles, have become prime targets for cyberattacks due to their public accessibility and integration with the power grid. A compromised EV charging station can disrupt the power supply, gather sensitive data from vehicles, and cause widespread issues.
Understanding the Vulnerabilities
EV Charging Stations are vulnerable through their three primary charging methods: Conductive, Inductive, and Battery Swap. Conductive Charging, which involves directly connecting a cable to the vehicle, is the most susceptible to cyberattacks. Recently, significant vulnerabilities have been identified in the ABB Terra AC wallbox, specifically versions 1.6.5 for the UL32A model and 1.5.5 for the UL4080A model. These vulnerabilities, cataloged as CVE-2023-0863 and CVE-2023-0864, allow attackers to exploit the system via Bluetooth Low Energy (BLE), potentially taking control of the station to eavesdrop on communications or alter configurations.
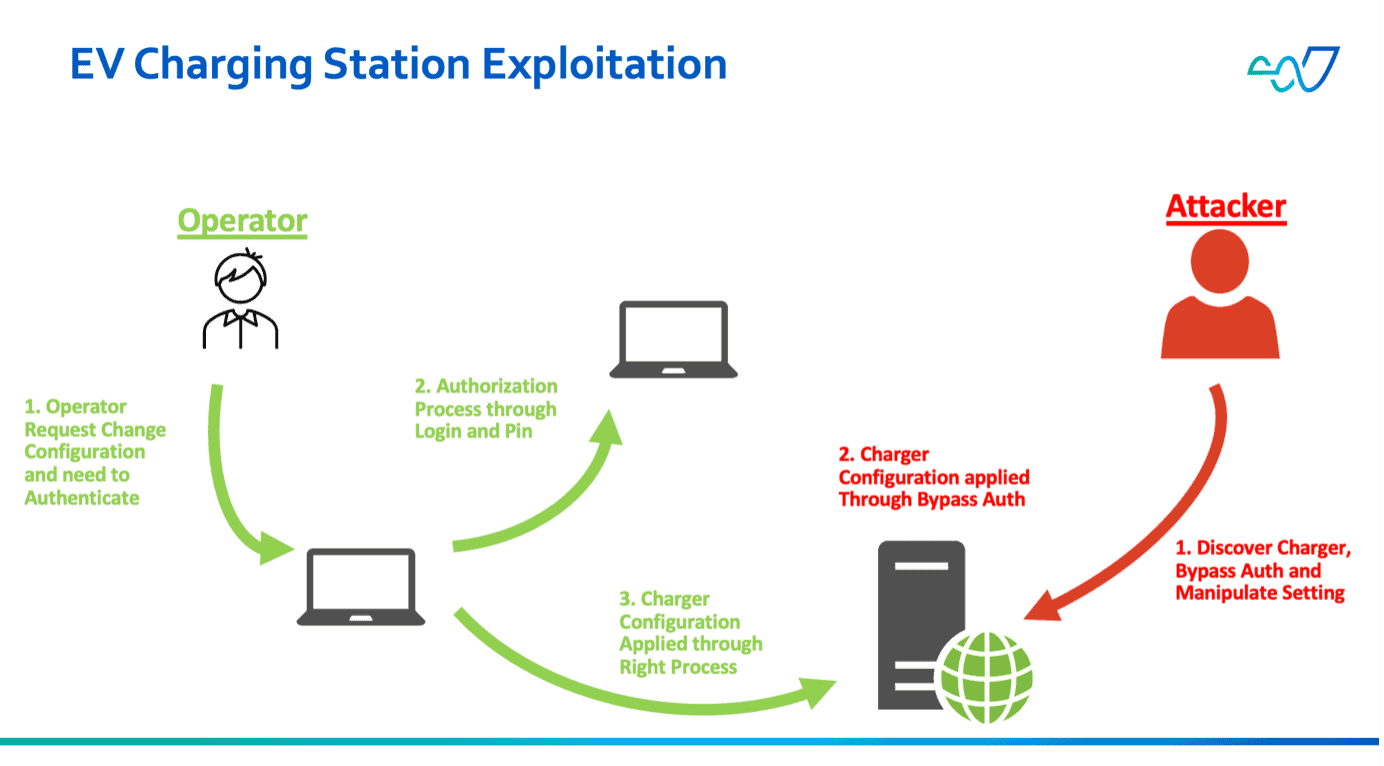
Case Study: ROOTK1T Hacker Group
A notable incident highlighting these vulnerabilities involved the ROOTK1T Hacker Group, which claimed to have taken over the EV charging infrastructure of Tenaga Nasional Berhad (TNB). This incident underscores the severity of such vulnerabilities and the importance of robust cybersecurity measures in protecting smart city infrastructure.
Mitigation Strategies with LogRhythm
To counter these risks, it is crucial to implement timely patches and activate Security Event Notifications for “AttemptedReplayAttacks.”
LogRhythm provides a comprehensive solution to monitor and detect exploitation attempts. By leveraging LogRhythm’s capabilities, organizations can identify suspicious activities, such as BLE attacks, in real-time.
For instance, the following log entry indicates a detected BLE attack:
{
"SecurityEventNotification": {
"type": "AttemptedReplayAttacks",
"techInfo": "bleAttacks",
"timestamp": "2024-02-18T20:33:38.000Z"
}
}
Advanced Monitoring with LogRhythm
LogRhythm’s advanced monitoring tools help organizations understand the normal activity of their EV infrastructure, making it easier to detect anomalies. Suspicious activities, such as cleared security logs, invalid firmware signatures, or unexpected device startups, can signal potential cyber threats.
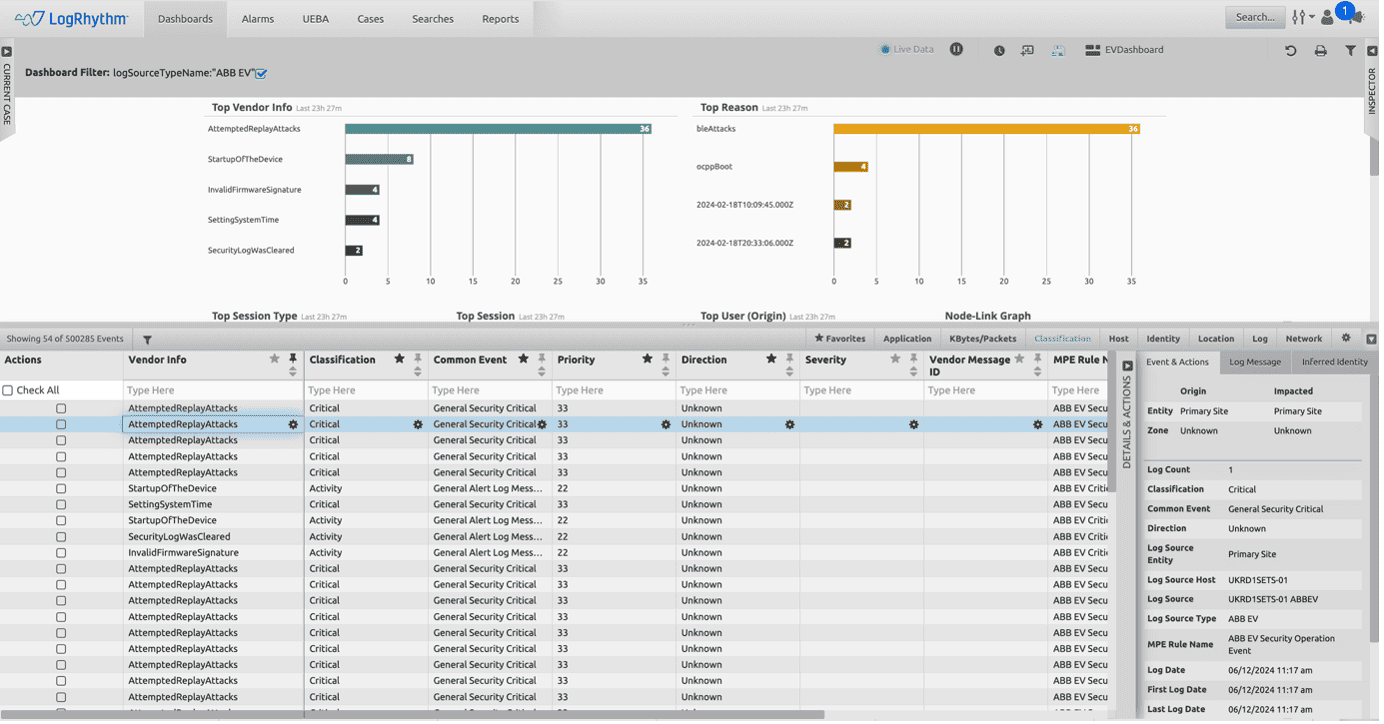
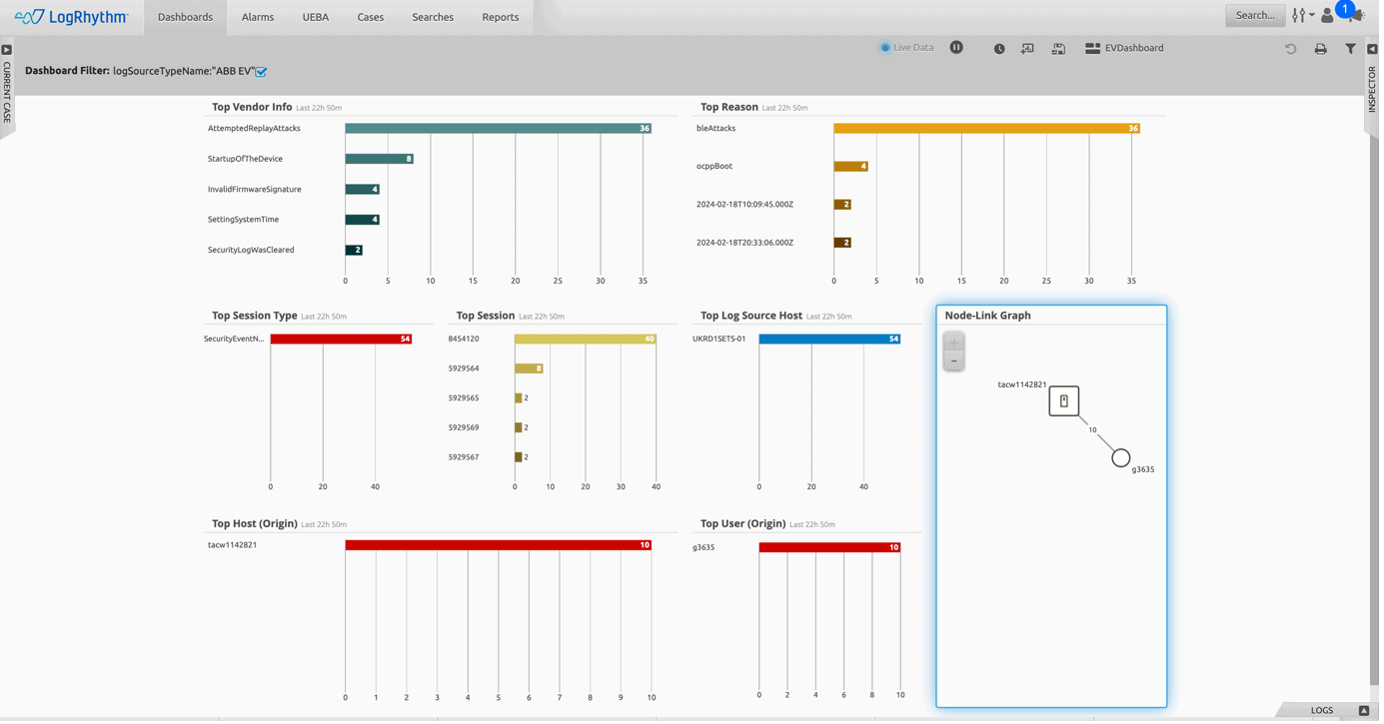
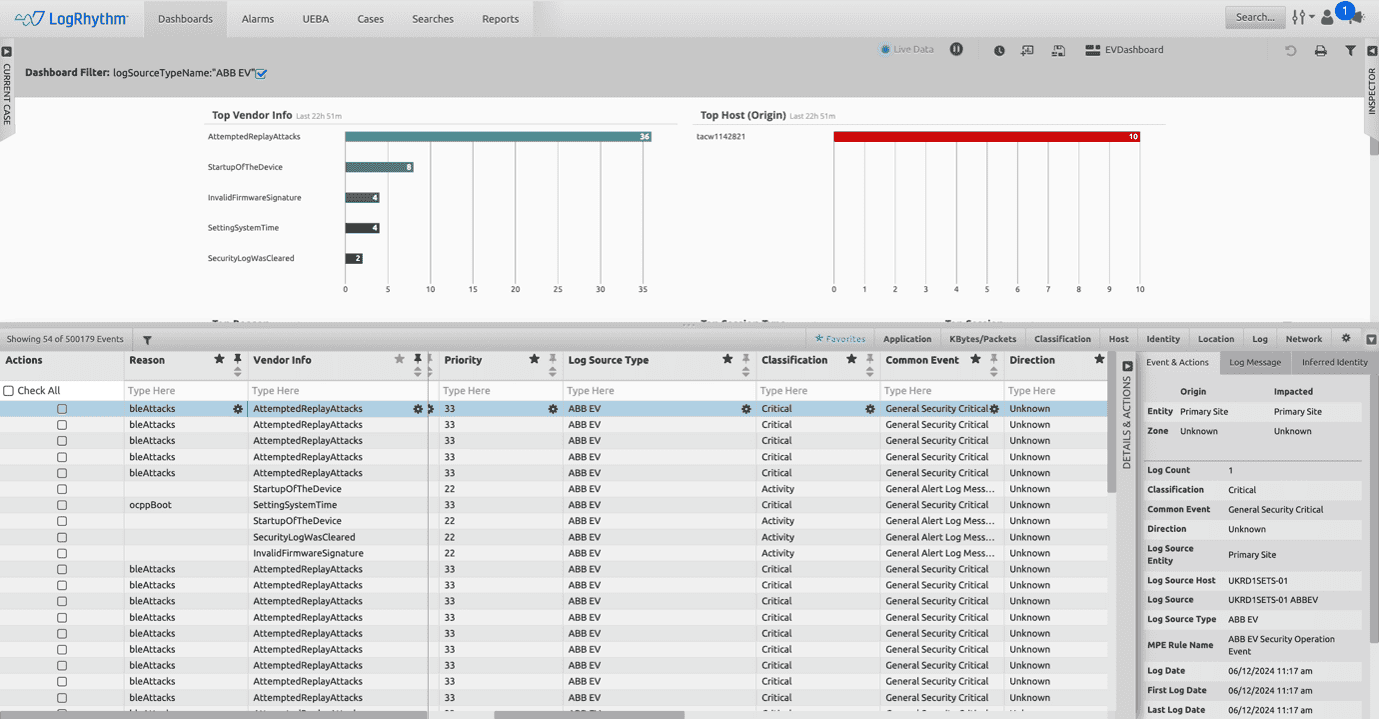
LogRhythm’s dashboard offers a consolidated and holistic view of security across Electric Vehicle infrastructure, integrating data from OT, IoT, and IT systems to provide comprehensive monitoring and threat detection capabilities.
Conclusion
As cyber threats continue to evolve, it is essential for organizations to protect all aspects of their infrastructure, including EV charging stations. These stations, though seemingly mundane, can have significant impacts if compromised. LogRhythm plays a crucial role in enhancing security visibility and ensuring the resilience of smart city infrastructure. By implementing robust monitoring and detection capabilities, organizations can safeguard their EV charging stations against cyberattacks, ensuring secure and reliable service for all users.
The post Supercharged Protection: Preventing EV Chargers Cyberattacks with LogRhythm appeared first on LogRhythm.
from LogRhythm https://ift.tt/SofsL13
via IFTTT
No comments:
Post a Comment