HashiCorp Vault 1.17 is now generally available, with new secure workflows, better performance, and improved secrets management scalability. HashiCorp Vault provides secrets management, data encryption, identity management, and other workflow capabilities for applications on any infrastructure.
The key feature additions to Vault 1.17 include:
- Workload Identity Federation (WIF) for Amazon Web Services, Microsoft Azure, and Google Cloud
- PKI support for IoT/EST-based devices
- PKI support for custom certificate metadata
Workload Identity Federation (WIF) for AWS, Azure, and Google Cloud
Workload Identity Federation (WIF) presents an opportunity to eliminate concerns around providing security credentials to Vault plugins. Using this new support for WIF, a trust relationship can be established between an external system and Vault's identity token provider to access the external system. This enables secretless configuration for plugins that integrate with external systems such as AWS, Azure, and Google Cloud. For example, a Vault-minted identity token can be exchanged for AWS credentials provided there is a trust relationship between Vault and AWS. By enabling secretless configuration, organizations reduce security concerns from using long-lived and highly privileged security credentials.

PKI certificate management enhancements
There are two major additions to PKI certificate management in Vault 1.17:
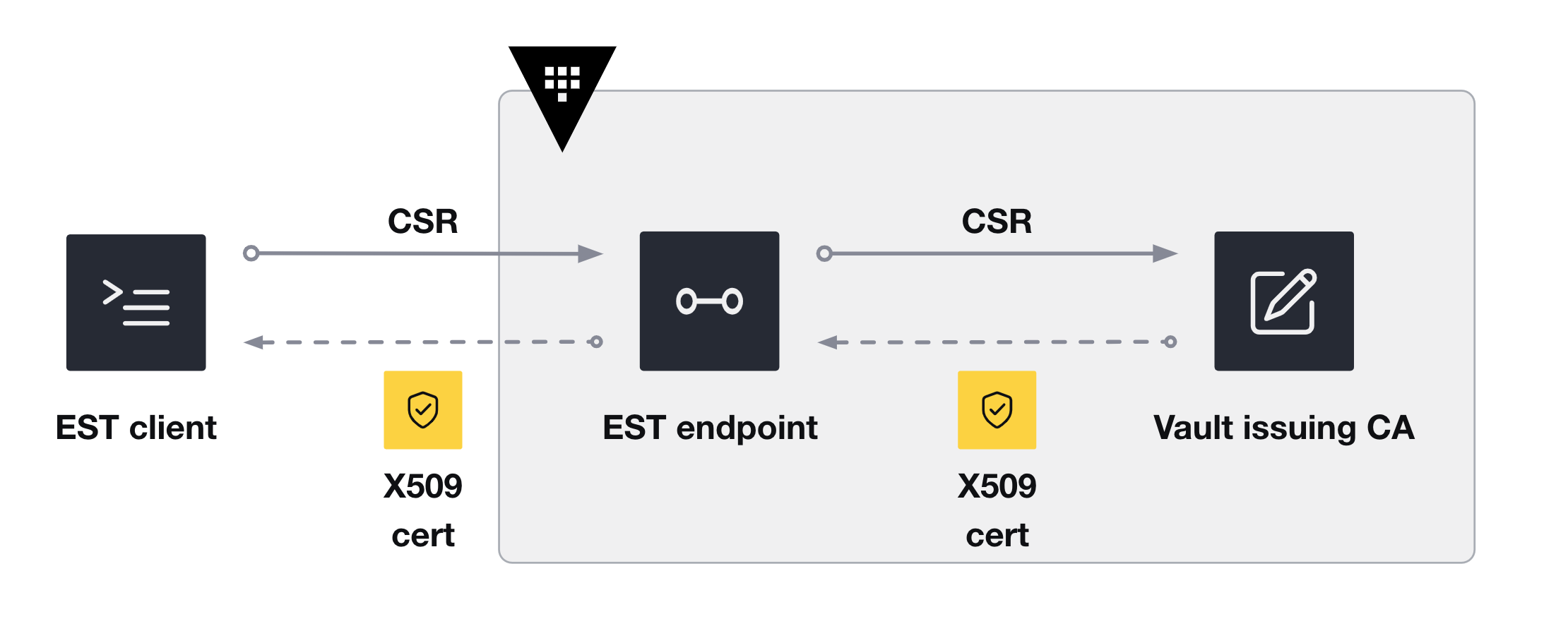
Support for IoT/EST-based devices
Vault PKI now adds support for automating X.509 certificates based on enrollment-at-scale requirements using the Enrollment over Secure Transport (EST) protocol. The rapid increase in the number of connected devices and services has expanded the attack surface area for enterprises, posing significant risks. Securing communications between devices and services is critical, but manual or ad hoc certificate lifecycle management is unrealistic at scale and may introduce additional security risks due to human error. Certificate automation within Vault now offers the ability to enroll and secure applications, virtual machines, containers, network components, infrastructure, and internet of things (IoT) devices with PKI EST. Learn how to use this new feature in our EST documentation.
Custom certificate metadata
Customers want the ability to store custom metadata associated with certificate signing requests that are not part of the standard certificate signing request (CSR) submitted to Vault PKI. Some customers are using manual or alternate methods for maintaining such metadata, which is not a reliable or scalable solution. With Vault 1.17, customers have the ability to submit additional custom metadata along with the CSR. Vault PKI will retain the metadata along with the issued certificate, which can then be ingested into external systems for further processing.
Vault Enterprise seal high availability (Seal HA)
Prior to this release, Vault Enterprise customers relied on a single key management system (KMS) provider to securely store the Vault seal key (AWS KMS, hardware security modules, HSMs, etc.). This could create a challenge for the customer if the seal key becomes unavailable from the KMS provider due to issues such as KMS instance deletion, compromise, or disaster. In such cases, Vault can’t be unsealed (as Vault will not have access to the seal key) resulting in a production outage. The new Vault Enterprise seal high availability feature lets customers configure independent seals secured with multiple KMS providers. This protects the continuity of business operations by giving Vault alternate configured KMS providers from which to access a seal key in case of KMS or HSM unavailability. To use this feature, administrators need to enable it via a configuration option.
Extend namespace and mount limits
For customers with very large deployments of Vault, limits on the number of namespaces and mounts a cluster can accommodate may become a bottleneck when onboarding new teams and services to Vault. Vault 1.17 introduces the ability to increase the size of specific storage entries so you can raise the capacity of mounts and the number of namespaces while keeping the rest of Vault's API at its default value. In effect, this new capability provides more room to vertically scale the cluster prior to scaling horizontally by adding more clusters.
Vault Secrets Operator (VSO) instant updates
Since the release of Vault Secrets Operator for Kubernetes in June of 2023, we continue to enhance the capability to directly connect Vault to native Kubernetes secrets, and Vault Enterprise 1.17 adds instant updates.
Due to emergencies or security events, a secret may need to be revoked or rotated before it expires. This could result in downtime because VSO would not be aware that the secret has been changed. With Vault Enterprise 1.17, VSO users can set the instant update flag to avoid this situation. When secrets change in Vault Enterprise, instant updates will notify VSO that relevant secrets have been updated and that it should immediately refresh the secret instead of waiting for its repolling window, minimizing downtime. Instant sync currently supports KVv2 and KVv1 secrets.
Vault 1.17 upgrade details
This release also includes more new features, workflow enhancements, general improvements, and bug fixes. All of these updates can be found in the Vault 1.17 changelog. Please visit the Vault release highlights page for step-by-step tutorials demonstrating the new features.
As always, we recommend upgrading and testing new releases in an isolated environment. If you experience any issues, please report them on the Vault GitHub issue tracker or post to the Vault discussion forum. As a reminder, if you believe you have found a security issue in Vault, please responsibly disclose it by emailing security@hashicorp.com — do not use the public issue tracker. For more information, please consult our security policy and our PGP key.
For more information about HCP Vault and Vault Enterprise, visit the HashiCorp Vault product page.
from HashiCorp Blog https://ift.tt/6OwRSr0
via IFTTT
No comments:
Post a Comment