The Good | DoJ Charges Phobos RaaS Admin & 5 Defendants Running Data Extortion Attacks
Russian national, Evgenii Ptitsyn, has been extradited from South Korea to the U.S. to face charges of wire fraud, conspiracy to commit computer fraud, and extortion related to hacking. According to court reports, Ptitsyn provided the Phobos ransomware-as-a-service (RaaS) operation with access to the payloads and platform used to extort ransom payments. Phobos is a long-running threat that has targeted over 1000 public and private companies with demands for payment totalling over $16 million.
As admin, Ptitsyn and his co-conspirators allegedly ran a dark market to sell and distribute the RaaS to affiliates who would then use stolen credentials to breach networks, encrypt data, and demand ransoms under the threat of leaking stolen files.
DC3 joined global efforts to support@TheJusticeDept in the extradition of Russian National Evgenii Ptitsyn from South Korea for administering Phobos ransomware. Over $16M extorted from 1,000+ victims, including schools & hospitals.

#Ransomwarehttps://t.co/l5Egkqg3NW pic.twitter.com/n1b8Yaga9n
— DoD Cyber Crime Center (DC3) (@DC3Forensics) November 18, 2024
The DoJ has also laid charges to five U.S. and U.K. nationals for wire fraud, wire fraud conspiracy, and aggravated identity theft as part of their association with the financially-motivated threat gang, UNC3944 (aka 0ktapus, Storm-0875, and Scattered Spider). Between 2021 and 2023, the gang stole millions from cryptocurrency wallets via SMS phishing attacks that targeted companies and individuals alike.
UNC3944 focuses on social engineering-based attacks, usually involving the impersonation of held desk technicians to steal credentials from company employees. Court documents also allege that the group used the logins to exfiltrate sensitive data including intellectual property, employee personal information, and confidential business databases, all later used in SIM swap attacks allowing the actors to hijack victims’ phone numbers and virtual wallets.
The DoJ and CISA offer technical details, IoCs, and mitigative recommendations for both Phobos ransomware and UNC3944 activity.
The Bad | New Version of NodeStealer Harvests Account Info Via Facebook Malvertising
Threat researchers are raising awareness about an updated version of NodeStealer, a Python-based malware designed to exploit Facebook Ads Manager accounts and extract digital payment data stored in web browsers. Their report details how the infostealer now employs new techniques such as leveraging Windows Restart Manager to unlock browser database files, using batch scripts to generate and execute Python scripts, and adding junk code.
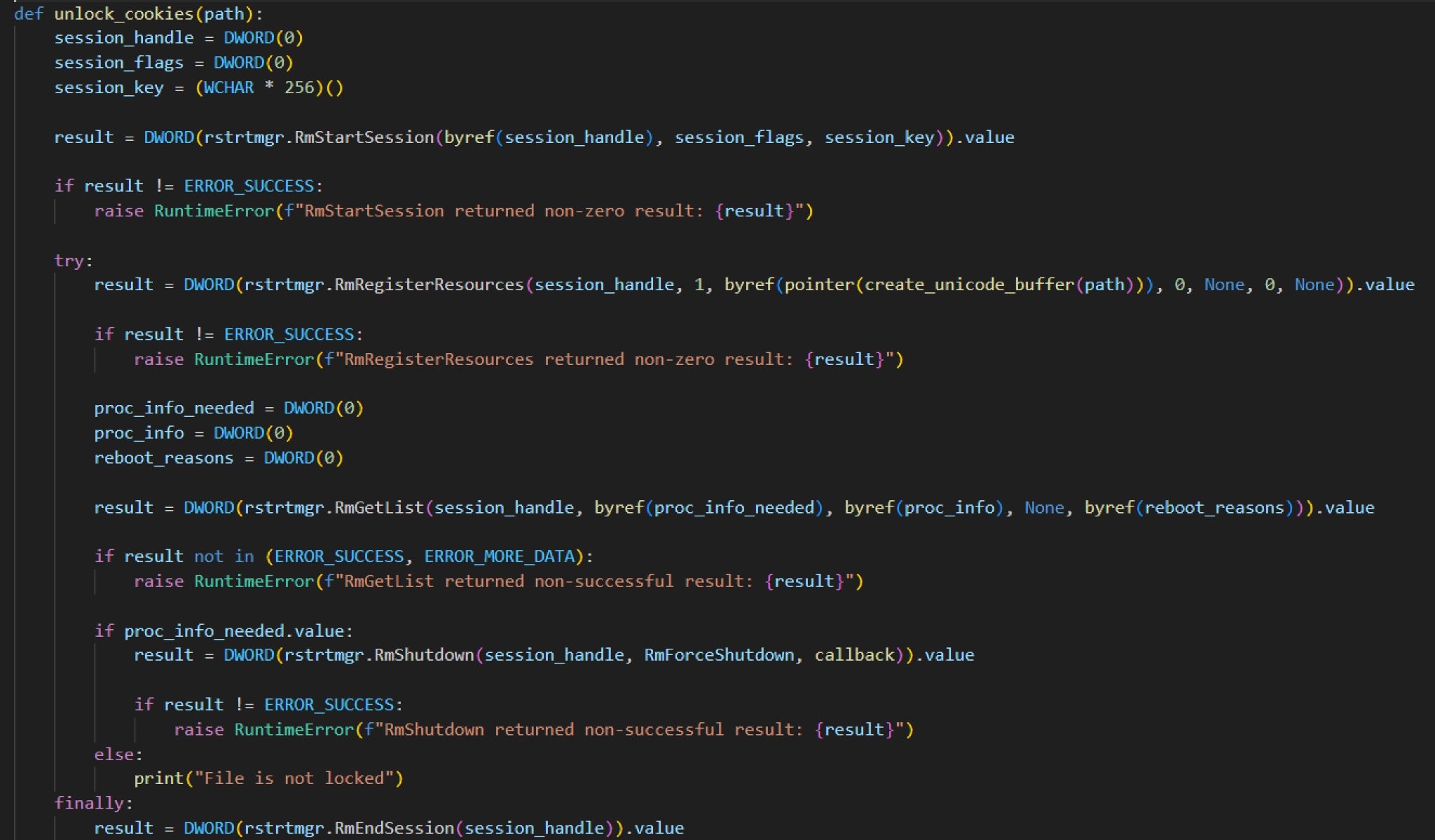
Initially documented as a JavaScript malware, NodeStealer has since evolved into a Python stealer that gathers data associated with Facebook accounts to facilitate their takeover. NodeStealer is attributed to Vietnamese-based threat actors primarily focused on hijacking Facebook advertising and business accounts to fuel their malvertising campaigns. In these campaigns, malware is disguised as trusted software or games to establish an infection pathway – the most recent attacks mimicking Bitwarden password manager through Facebook sponsored ads, for example, to install a rogue Chrome browser extension.
The latest version of Python NodeStealer harvests tokens and business-related data via Facebook Graph API by generating access tokens from cookies collected on victims’ devices. Researchers note that certain NodeStealer samples were observed using the Windows Restart Manager to unlock SQLite database files possibly used by other processes. This allows the threat actors to exfiltrate credit card information tied to the account over to Telegram.
Malvertising continues to run rampant on platforms like Facebook, where attackers can impersonate any number of well-known brands to target large numbers of users at once. In addition to gathering lucrative payment data, any personally identifiable information (PII) gathered by NodeStealer is then either sold on dark markets or used for identity fraud schemes later on. A list of IoCs can be found here.
The Ugly | DPRK IT Front Companies Impersonate U.S. Firms to Fund State Activities
The DPRK operates a wide network of IT workers, skilled across high-demand IT verticals, as individuals and under front companies. A new report from SentinelLabs calls out four recently discovered DPRK IT Worker front companies, adding to our understanding of this extensive scheme and the methods North Korea uses to generate revenue for the regime and evade international sanctions.
DPRK-linked front companies are often based in China, Russia, Southeast Asia, and Africa, allowing the IT workers to mask their true origins and secure remote roles with businesses worldwide. To boost their legitimacy, these companies pose as U.S.-based software and tech consulting businesses by copying branding from real organizations.
SentinelLabs adds four more to the growing list: Independent Lab LLC (copied from custom software firm, Kitrum), Shenyang Tonywang Technology LTD (copied from DevOps consulting company, Urolime), Tony WKJ LLC (copied from India-based software and web development company, ArohaTech IT Services), and HopanaTech (copied from iTechArt). Each of these websites have since been seized by law enforcement including the DoJ, FBI, and Homeland Security Investigations.
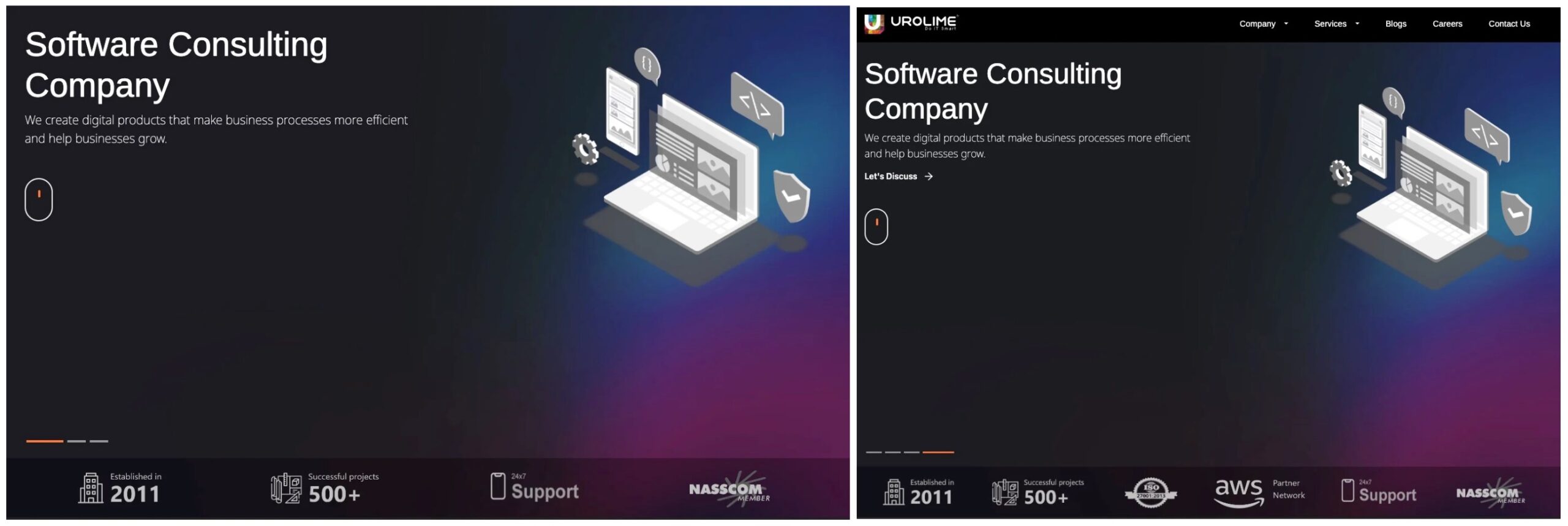
Right: Legitimate Urolime business, source of copied website design used by DPRK
Expanding on details from the official takedowns, SentinelLabs connects the four new DPRK IT front companies to a larger, active network of front companies being created in China. This connection highlights both the scale and depth of North Korea’s strategy to finance state activities, circumvent sanctions, and evade detection in the long term. By impersonating legitimate U.S. firms and software brands, these IT front companies continue to emerge and present significant risks to employers such as insider threats, theft of intellectual property, reputational damage, and malware attacks. Organizations can protect themselves by heightening their awareness of these schemes and fortifying their vetting processes for contractors and suppliers.
from SentinelOne https://ift.tt/CZ10Ynr
via IFTTT
No comments:
Post a Comment