Amazon Web Services’ flagship cloud conference — AWS re:Invent — is back, and this year, as an Emerald sponsor, HashiCorp’s presence is bigger than ever. For both in-person and remote attendees, we’re pleased to share the latest news on our long-standing relationship with AWS and how we help organizations provision, secure, run, and connect applications running in AWS.
HashiCorp Infrastructure Lifecycle Management (ILM) with AWS lets you build, deploy, and manage** your infrastructure lifecycle the right way by enforcing policies, boosting productivity, sharpening visibility, and removing unneeded resources on AWS. As AWS re:Invent takes center stage, it’s a great moment to reflect on our major infrastructure collaborations with AWS and significant milestones from the past year.
Here are some highlights from 2024 with details further below:
Build. Establishing a robust and consistent approach to building your AWS environments is the cornerstone of effective ILM. Key highlights this year include:
- 3 billion downloads of the Terraform AWS provider: A testament to the trust and adoption of our tools by the community
- AWS Cloud Control provider launch: Seamlessly provisioning and managing AWS resources across services with ease
Deploy. Provision the infrastructure needed to deploy an application — then schedule and make it happen. Key highlights include:
- Pre-written Sentinel polices for AWS: Simplify governance with out-of-the-box policy enforcement
- Provider-defined functions: Build custom functions directly within AWS providers, giving you greater flexibility
- Terraform Stacks public beta: Streamline complex multi-account, multi-region environments
Manage. Provide a system of record for all infrastructure, images, workloads, and applications in one platform for visibility and management. Key highlights include:
- AppFabric support: Expanding HCP Terraform integration capabilities with AWS
- OIDC federation for HCP Terraform: Simplify and secure AWS access directly from HCP Terraform
Build
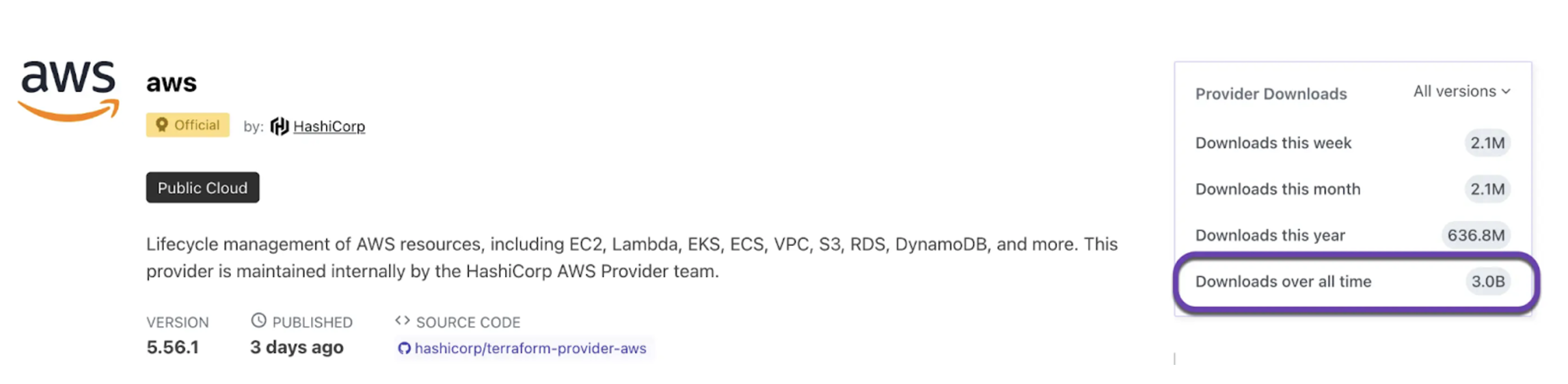
3 billion downloads of the Terraform AWS provider
This year, we reached the 10th anniversary of the Terraform AWS provider and crossed three billion downloads. These milestones represent the collective success of AWS builders and the essential role Terraform plays in shaping the future of infrastructure management. It underscores the growing recognition of the need for standardized IaC solutions as organizations scale. Terraform plays a pivotal role in empowering application teams to compose, reuse, and collaborate effectively on infrastructure provisioning, ultimately accelerating the build and deployment process. We look forward to the next major milestones.
AWS Cloud Control provider launch
Built around the AWS Cloud Control API and designed to bring new services to HashiCorp Terraform faster, the AWS Cloud Control (AWSCC) provider is now generally available. The 1.0 release of the AWSCC provider represents another step forward in our effort to offer launch-day support for AWS services. The Terraform AWS Cloud Control provider is automatically generated based on the Cloud Control API published by AWS, which means the latest features and services on AWS can be supported right away.
The AWSCC provider is a great complementary provider to add to your existing Terraform configurations that use the standard AWS provider. Given its ability to automatically support new features and services, this AWSCC provider will increase resource coverage and significantly reduce the time it takes to support new capabilities.
Deploy
Pre-written Sentinel polices for AWS
Earlier in June, in partnership with AWS, HashiCorp agreed to co-develop a comprehensive set of Terraform policies to provide expert guidance for architecting, configuring, and operating on AWS. These policies will enforce compliance with standards such as CIS, HIPAA, FINOS, and the AWS Well-Architected Framework.
This joint effort is intended to help customers implement infrastructure and security lifecycle management, accelerate time-to-value, mitigate implementation risk, and provide a framework to address outcome-driven use cases surrounding security and compliance.
At re:Invent, we are excited to announce the public beta of pre-written Sentinel policy sets for AWS, now available for use in the Terraform registry. These new policies are co-created and co-owned by HashiCorp and AWS, and are written specifically to help organizations comply with industry standards. With this release, we aim to lower the barrier of adoption for infrastructure policy enforcement and accelerate the time to value for customers looking to address cloud governance at scale. For more information on this collaborative effort, please see our blog post or the AWS blog post.
This first set of policies has been written specifically for AWS services in compliance with the Center for Internet Security (CIS). CIS is a non-profit organization that provides prescriptive configuration recommendations that represent the consensus-based effort of cybersecurity globally. Our pre-written policy sets help with CIS benchmarks v1.2, v1.4, and v3.0, with supported services including EC2, IAM, Cloudtrail, S3 and more.
Users can now browse the Terraform Registry Policy Library to discover and reference the pre-built policies. With Sentinel’s native integration, users can quickly deploy the policy sets into their HCP Terraform organizations. Sentinel policy will inspect the Terraform configuration plan and block resource provisioning if it fails one of the defined policy checks.
Provider-defined functions
Provider-defined functions in the AWS provider represent yet another step forward in our unique approach to ecosystem extensibility. Provider-defined functions will allow anyone in the Terraform community to build custom functions within the AWS providers and extend the capabilities of Terraform.
The 5.40 release of the Terraform AWS provider includes its first provider-defined functions to parse and build Amazon Resource Names (ARNs), simplifying Terraform configurations where ARN manipulation is required. The arn_parse provider-defined function is used to parse an ARN and return an object of individual referenceable components, such as a region or account identifier.
Terraform Stacks public beta
Terraform Stacks are a feature intended to simplify infrastructure provisioning and management at scale. When deploying and managing infrastructure at scale, teams usually need to provision the same infrastructure multiple times with different input values, across multiple cloud provider accounts, regions, environments (dev, staging, production) and landing zones.
Before Terraform Stacks, there was no built-in way to provision and manage the lifecycle of these instances as a single unit in Terraform, making it difficult to manage each infrastructure root module individually. Now, Stacks help users automate and optimize the coordination, deployment, and lifecycle management of interdependent Terraform configurations, reducing the time and overhead of managing infrastructure.
Manage
AppFabric support for Terraform
AWS AppFabric now supports Terraform. IT administrators and security analysts can use AppFabric to quickly integrate with Terraform, aggregate enriched and normalized SaaS audit logs, and audit end-user access across their SaaS apps. This launch expands AWS AppFabric supported applications used across an organization.
AWS AppFabric quickly connects SaaS applications, or data lakes like Amazon Security Lake. For HCP Terraform users, this integration can accelerate time-to-market and help developers release new features to production faster with streamlined infrastructure provisioning and application delivery workflows.
To learn more, visit the AWS AppFabric page and then check out how to connect AppFabric to your Terraform account.
OIDC federation for HCP Terraform
Storing access keys in Terraform configurations poses a security risk. While HCP Terraform secures sensitive credentials as write-only variables, you must audit the usage of long-lived access keys to detect if they are compromised. Not only is leaking the access key a risk, but many organizations have a policy to block the creation of such access keys.
Fortunately, in many cases, you can authenticate with more secure alternatives to access keys. One such alternative is AWS IAM OIDC federation, which uses identity and access management (IAM) to grant external identities (such as HCP Terraform) the ability to assume an IAM role.
HCP Terraform’s dynamic provider credentials allow Terraform runs to assume an IAM role through native OpenID Connect (OIDC) integration and obtain temporary security credentials for each run. These AWS credentials allow you to call AWS APIs that the IAM role has access to at runtime. These credentials are usable for only one hour by default, so their usefulness to an attacker is limited.
This brief tutorial will show you how to set up an OIDC provider and access AWS from HCP Terraform using dynamic provider credentials and OIDC federation.
Learn more about AWS and HashiCorp
AWS and HashiCorp continue to extend our partnership, building new integrations to help customers work faster, take advantage of more services and features, and provide developer-friendly ways to deploy cloud infrastructure.
To learn the basics of Terraform using the AWS provider, follow the hands-on tutorials for getting started with Terraform on AWS on our developer education platform. Interact with AWS services, including Lambda, RDS, and IAM, by following the AWS services tutorials.
from HashiCorp Blog https://ift.tt/hjzivEV
via IFTTT
No comments:
Post a Comment