We are excited to announce the public beta of pre-written Sentinel policy sets for AWS, now available for use in the Terraform registry. These new policies are co-created and co-owned by HashiCorp and AWS. They are written specifically to help organizations comply with industry standards and lower the barrier of adoption for infrastructure policy enforcement.
With this release, we aim to provide a turnkey solution to complex governance challenges and empower organizations to move faster without trade-offs between speed and security. This joint effort highlights the unique value of pairing AWS’s cloud infrastructure with HashiCorp’s automation and security capabilities.
Challenges in policy adoption
Sentinel is an embeddable policy as code framework that provides logic-based policy enforcement over infrastructure configurations in HashiCorp Terraform and other HashiCorp product configurations. This approach lets organizations treat policies like application code, meaning the code can be version controlled, audited, tested, and understood by stakeholders across the organization.
Sentinel policies help organizations control what Terraform users are allowed to do, ensuring that certain thresholds for infrastructure provisioning are not exceeded, and blocking insecure or non-compliant configurations.
See how Fannie Mae, a well-known and highly regulated financial institution, uses Sentinel policies to enforce 400+ preventative security, architectural, and financial guardrails to make sure its infrastructure meets compliance requirements.
While Sentinel can be used as a powerful tool to ensure cloud governance at scale, we understand that adopting policy as code workflows may be a daunting and time-consuming process. This is especially true for organizations that lack the resources and expertise to write policies from scratch. Starting from the ground up can lead to significant delays in the development and implementation of policies, and increase the risk of human error and misconfigurations.
Introducing co-owned pre-written policy sets with AWS
To address these challenges, HashiCorp and AWS co-developed a library of pre-written policies that cover a wide range of use cases, including security, compliance, and operational efficiency. These policies have been written by experts with years of experience in the industry, and have been tested and validated to ensure their reliability and efficiency. The policies are also customizable, allowing organizations to quickly adjust them to meet their specific needs.
These policies are written specifically for AWS services in compliance with the Center for Internet Security (CIS). CIS is a non-profit organization that provides prescriptive configuration recommendations that represent the consensus-based effort of cybersecurity globally. Our pre-written policy sets help with CIS AWS Foundation Benchmarks v1.2, v1.4, and v3.0, with supported services including:
- EC2
- KMS
- Cloudtrail
- S3
- IAM
- VPC
- RDS
- EFS
Users can now browse the Terraform Registry policy library to discover and reference the pre-built policies. With Sentinel’s native integration, users can quickly deploy the policy sets into their HCP Terraform organizations.
After deploying these policies, administrators can set three different enforcement levels:
- Hard mandatory - If a policy fails, the run stops. You must resolve the failure to proceed.
- Soft mandatory - Lets an organization owner or a user with override privileges proceed with the run in the event of failure.
- Advisory - Will notify you of policy failures, but proceed with the operation.
The example Terraform run below shows two advisory-level CIS policies that were triggered.
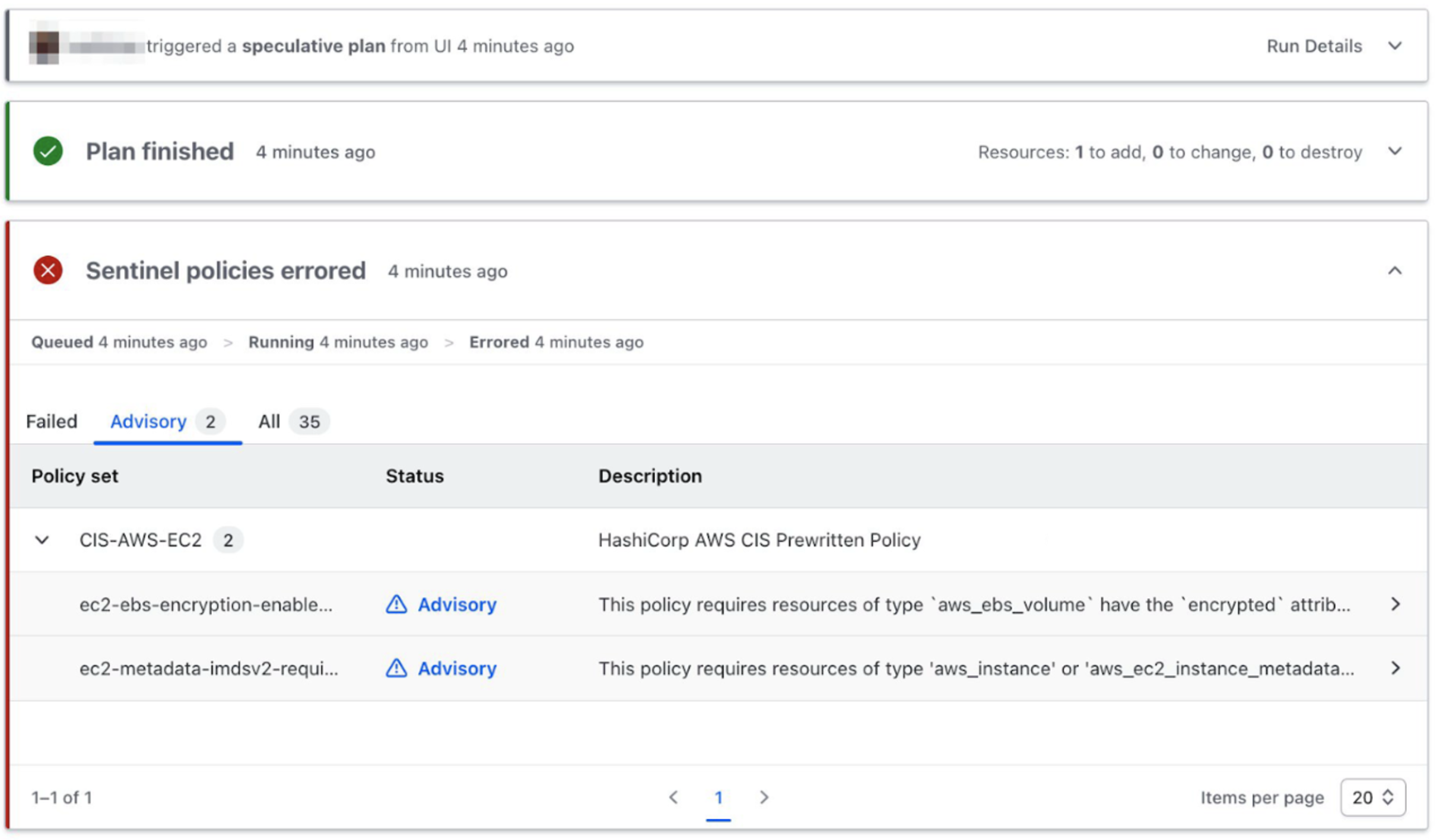
With this solution, organizations can consistently enforce policies of varying strictness across all of their infrastructure efficiently at scale. These pre-written policies should help organizations using AWS jumpstart their policy as code adoption — unlocking more speed and more security with no trade-offs.
Next steps
Try HCP Terraform out for free and see the benefits of policy as code workflows in action. For more information on Sentinel language and specifications, visit the Sentinel documentation page. If you would like to engage with the community to discuss information related to Sentinel use cases and best practices, visit the HashiCorp Community Forum.
Don’t forget to link your HCP Terraform and HashiCorp Cloud Platform (HCP) accounts for a seamless sign-in experience.
from HashiCorp Blog https://bit.ly/49m4z04
via IFTTT
No comments:
Post a Comment